Vulnerability Description: Improper Neutralization of Input During Web Page Generation ('Reflected Cross-site Scripting') – CWE-79
Software Version: R19.9
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-41762
CVSv3: 6.1
Severity: Medium
Credits: Luca Di Giuseppe, Alessandro Bosco, Stefano Scipioni, Massimiliano Brolli
Multiple Cross-site scripting Reflected (XSS) vulnerability allows unauthenticated remote attackers to inject arbitrary web script or HTML into HTTP/GET parameter which reflects the user input without sanitization.
Step-by-step instructions and PoC
The Web application, and to be more precise the module that manages the VM element (qemu Webui), does not properly check the parameters sent as input from clients before is re-included within the HTTP response returned by the application. Due to the lack of validation of user input, allows an attacker to modify the HTML code and the expected execution flow could be altered.
Affected Endpoints
· URL: https:// [...]/cgi-bin/R19.9/log.pl?logfile=&bench=1734&c=test&pid=19247&cmd=test
o HTTP GET Parameter: all parameters
· URL: https:// [...]/cgi-bin/R19.9/top.pl?logfile=/var/file&bench=[REDACTED]&c=1&pid=15883&cmd=test
o HTTP GET Parameter: bench, pid
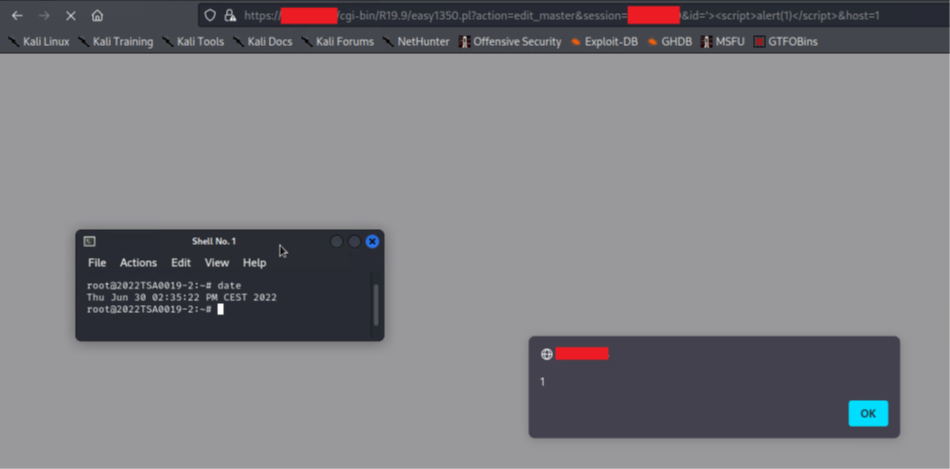
· URL: https:// [...]/cgi-bin/R19.9/easy1350.pl?action=edit_master&session=[REDACTED]&id=1&host=1
o HTTP GET Parameter: id
Below are the evidences with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
GET /cgi-bin/R19.9/log.pl?logfile="</script><img+src=1+onerror=alert(1)>&bench=123&c=test&pid=19247&cmd=test HTTP/1.1
Host: X.X.X.X
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
This first step consists of replacing the value in the “logfile” GET parameter with the javascript code to modify the content of the HTML response page, the content of the parameter is printed in several places on the page without any checks being made. The same behavior is the same for all parameters of the request.
Click to Enlarge
Security Impact
Successful attacks of this vulnerability can result in unauthorized access to critical data or complete account takeover.