Vulnerability Description: Reflected Cross-Site Scripting - CWE-79
Software Version: <= 2.40-2
NIST: https://nvd.nist.gov/vuln/detail/CVE-2021-35489
CVSv3: 6.1
Severity: Medium
Credits: Mattia Campanelli, Alessandro Bosco, Alessandro Sabetta, Massimiliano Brolli
Thruk version 2.40-2 allows /thruk/#cgi-bin/extinfo.cgi?type=2&host=[HOSTNAME]&service=[SERVICENAME]&backend=[BACKEND] Reflected XSS on 'host' and 'service' parameters. A malicious user leveraging this vulnerability could inject arbitrary JavaScript into extinfo.cgi. The malicious payload will then be triggered every time an authenticated user browses the page containing it.
The vulnerable functionality can be reached through the following URL:
A PoC is possible inserting the malicious payload in one of the host or service fields (GET Request):
This occurs due to the closure of a comment, as demonstrated in the next screenshot.
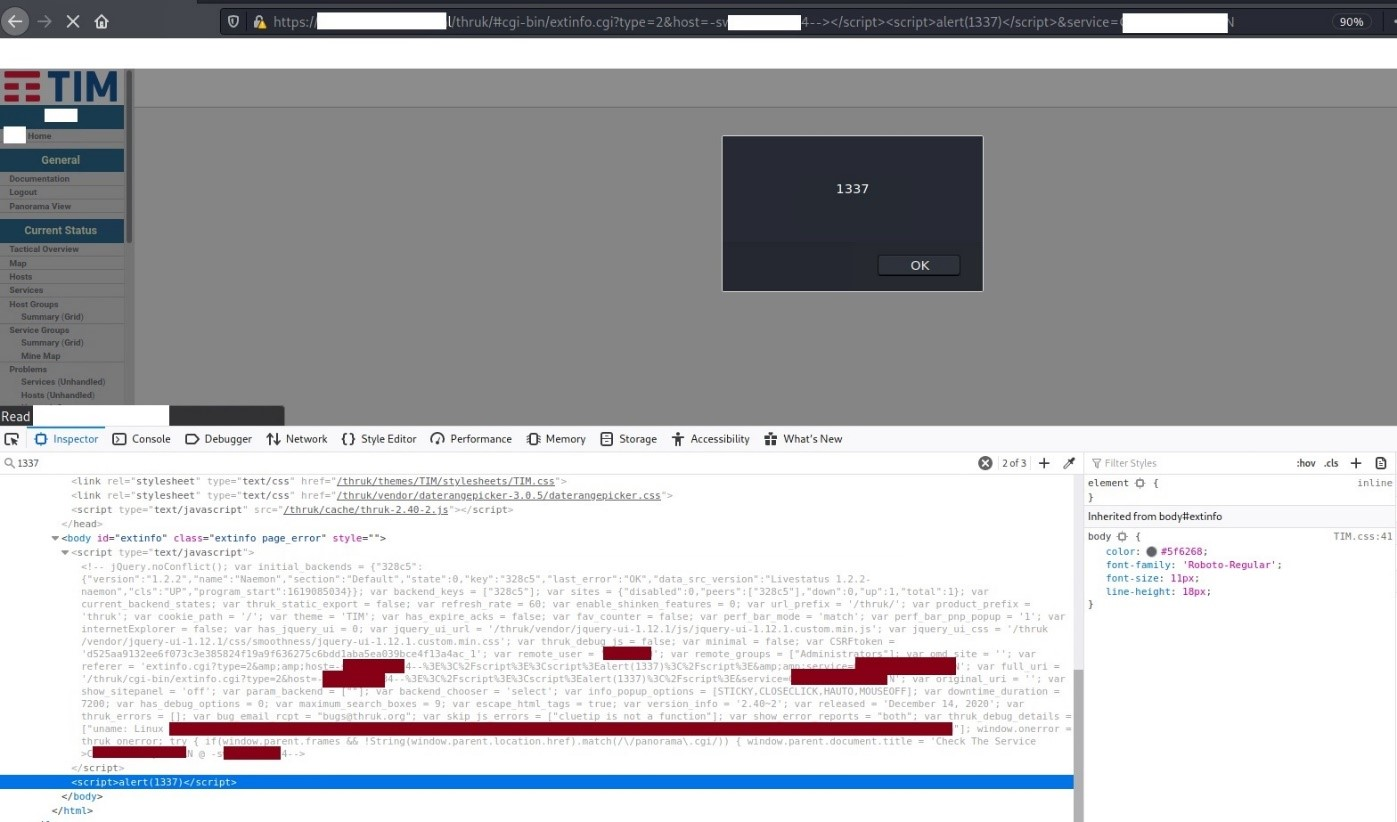
Figure 1: Reflected XSS on extinfo.cgi – Payload 1
Some other screenshots demonstrating the vulnerability:
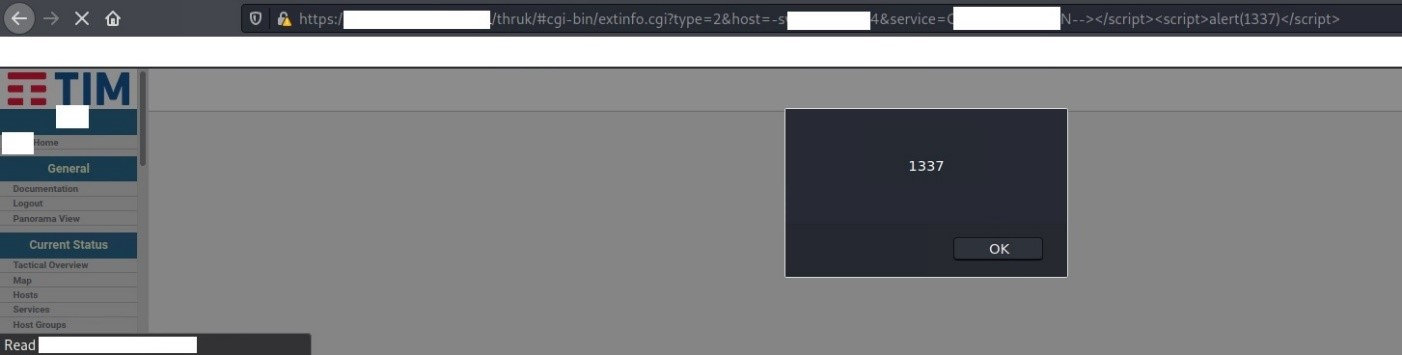
Figure 2: Reflected XSS on extinfo.cgi – Payload 2
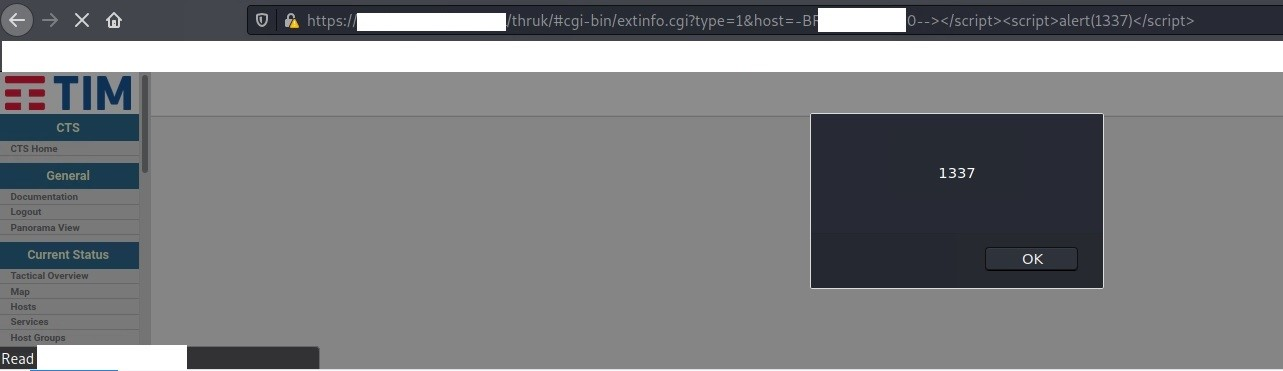
Figure 3: Reflected XSS on extinfo.cgi – Payload 3
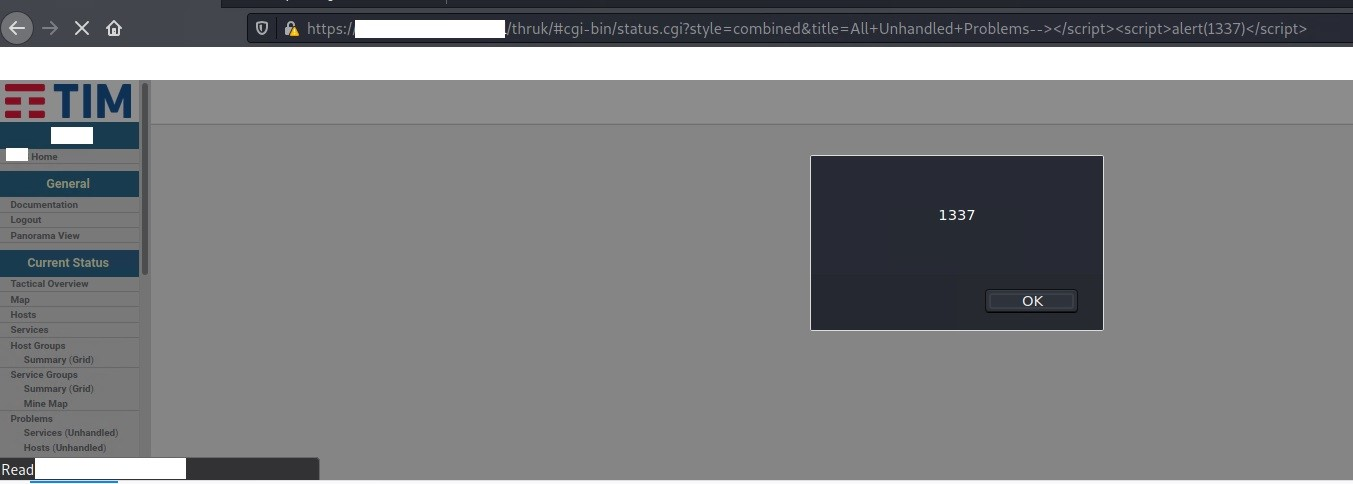
Figure 4: Reflected XSS on extinfo.cgi – Payload 4