Vulnerability Description: Improper Access Control- CWE-284
Software Version: < R18 Firmware v4.13.00
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-28866
CVSv3: 8.8
Severity: High
Credits: Andrea Carlo Maria Dattola, Massimiliano Brolli
Multiple Improper Access Control was discovered in Nokia AirFrame BMC Web GUI < R18 Firmware v4.13.00. It does not properly validate requests for access to (or editing of) data and functionality in all endpoints under /#settings/* and /api/settings/*. By not verifying the permissions for access to resources, it allows a potential attacker to view pages, with sensitive data, that are not allowed, and modify system configurations also causing DoS, which should be accessed only by user with administration profile, bypassing all controls (without checking for user identity).
Affected Endpoints
· URL: https://[IP]/#settings/ext_users
· URL: https://[IP]/#settings/redundancy
· URL: https://[IP]/#settings/services/edit/2
· URL: https://[IP]/#settings/mouse
· URL: https://[IP]/#settings/log
· URL: https://[IP]/#settings/pef
· URL: https://[IP]/#settings/smtp
· URL: https://[IP]/#settings/ssl
· URL: https://[IP]/#settings/firewall
· URL: https://[IP]/#settings/sol
· URL: https://[IP]/api/settings/*
Step-by-step instructions and PoC
The following images show some vulnerable endpoints, as PoC, that can be accessed by an unauthorized user:
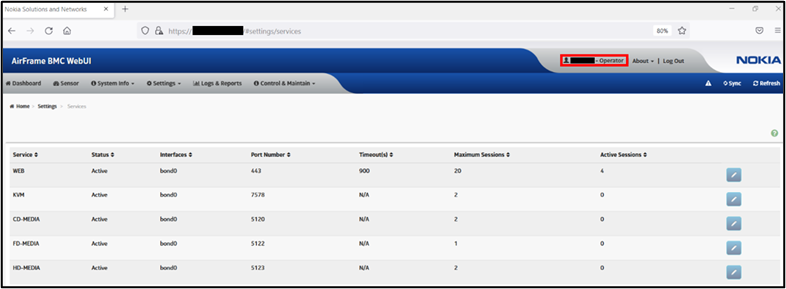
Fig. 1
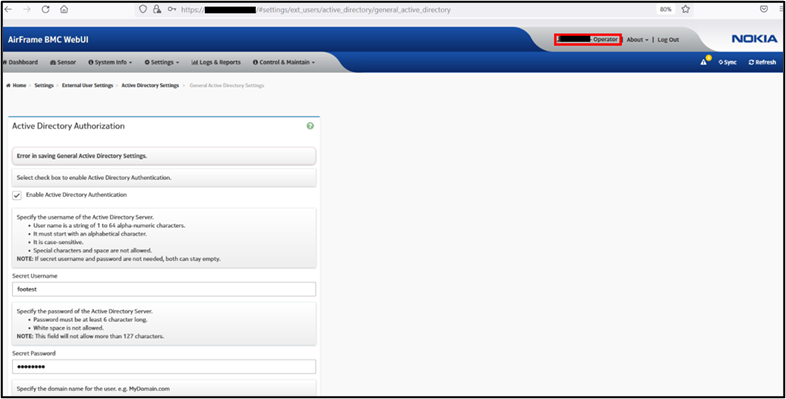
Fig. 2
The following steps show that an Operator user is able to edit configuration pages bypassing both access controls on the endpoint and client side access controls. In the specific case, the endpoint under analysis is: https://[IP]/#settings/redundancy.
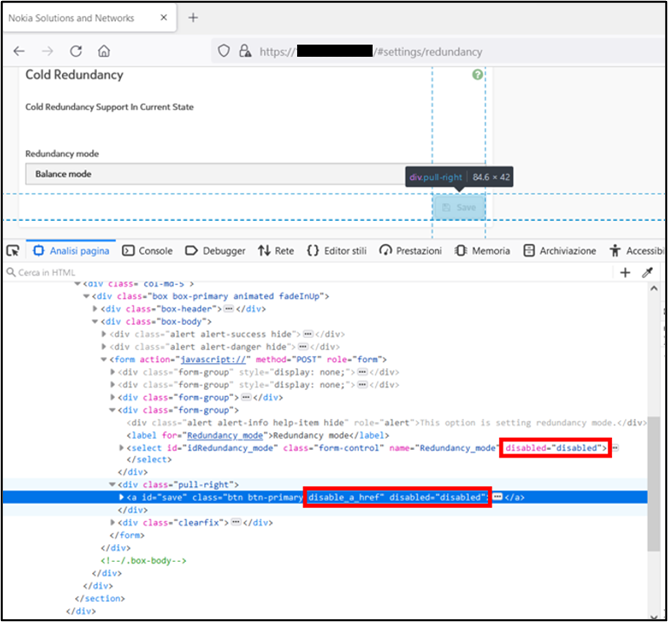
Fig. 3
As a first step, you can enable any javascript by removing the "disabled" attribute within the "select" and "a" tags..
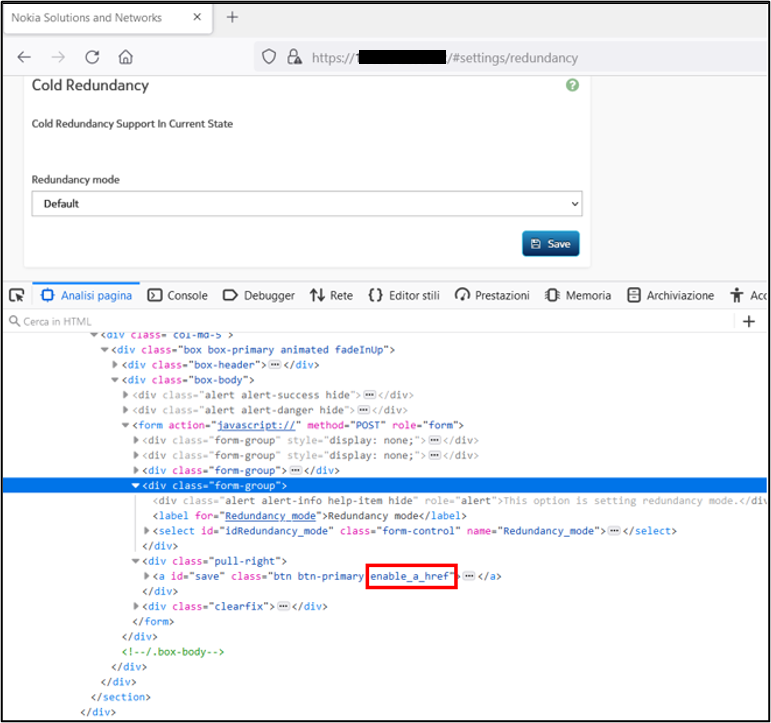
Fig. 4
The next image shows the request sent by the nonprivileged operator user to change the configuration and its response
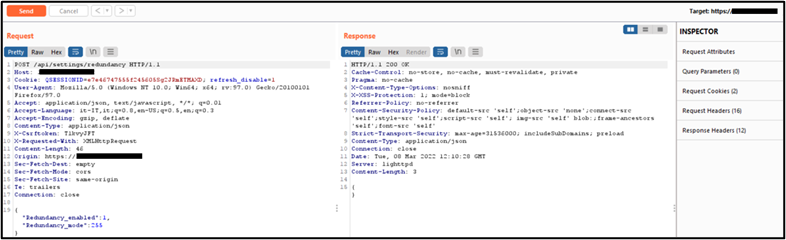
Fig. 5
The last image shows that the Operator user has successfully changed the configuration.
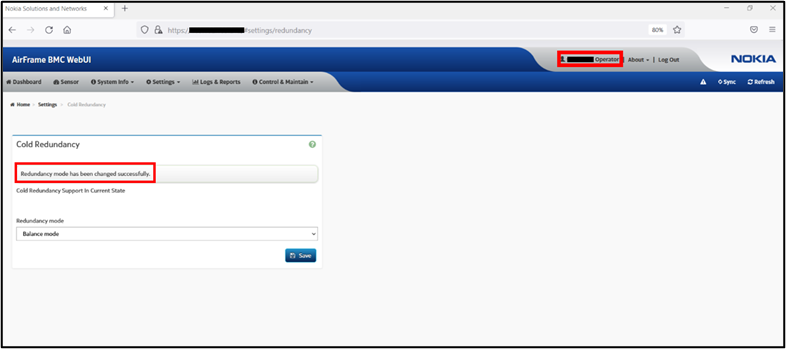
Fig. 6