Vulnerability Description: Cross-Site Request Forgery (CWE-352)
Software Version: v22.0.0.62
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-30280
CVSv3: 8.8
Severity: High
Credits: Massimiliano Ferraresi, Massimiliano Brolli
/SecurityManagement/html/createuser.jsf in Nokia NetAct 22 allows CSRF. A remote attacker is able to create users with arbitrary privileges, even administrative privileges. The application (even if it implements a CSRF token for the random GET request) does not ever verify a CSRF token. With a little help of social engineering/phishing (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attacker's choosing. If the victim is a normal user, a successful CSRF attack can force the user to perform state changing requests like transferring funds, changing their email address, and so forth. If the victim is an administrative account, CSRF can compromise the entire web application.
Step-by-step instructions and PoC

It’s worth to remark that from the admin profile it is possible to add users with various privileges by exploiting this endpoint:
· https://hostname/SecurityManagement/html/listusers.jsf
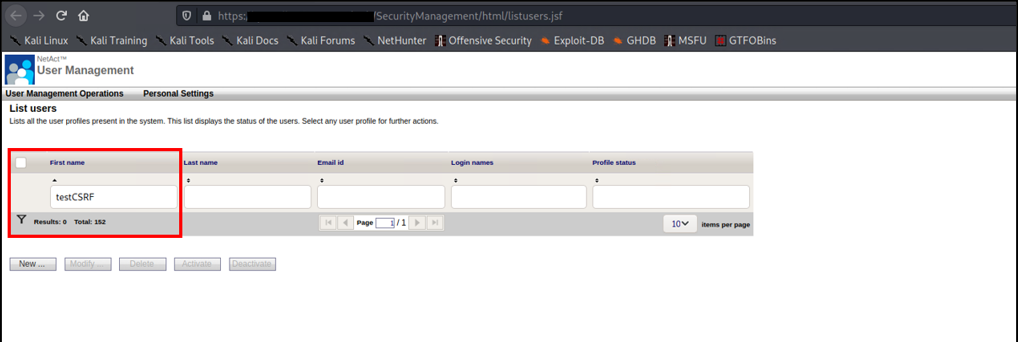
The following image shows the application without testCSRF profile:
The administrator, who is logged into the application, is induced to visit, by means of phishing or social engineering, an endpoint containing a specific HTML code csrf2.html
Then, the administrator's browser will sends the following HTTP requests to the NetAct application that accept the request with arbitrary Origin and Referer.
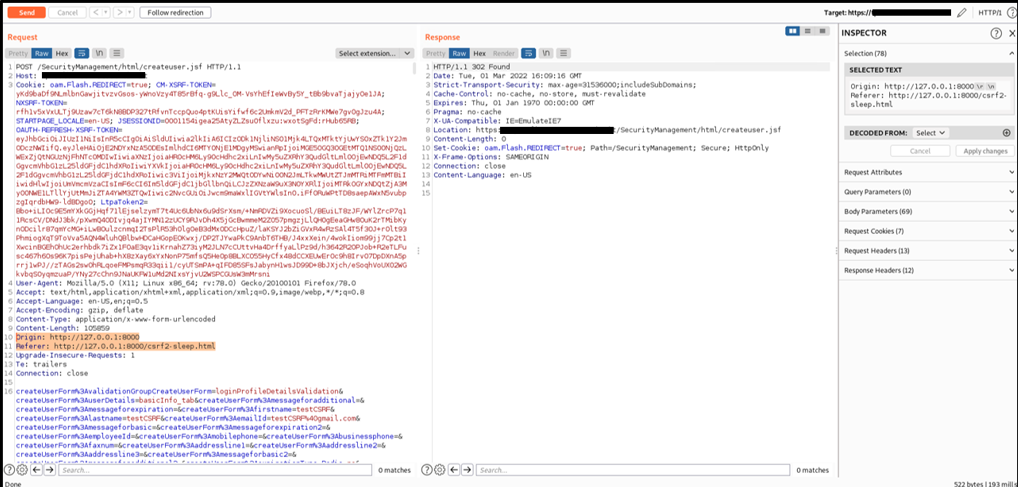
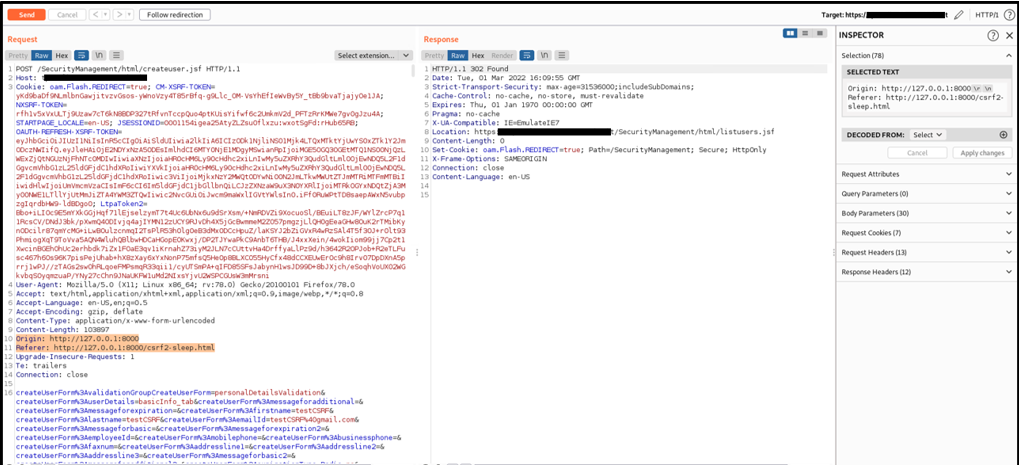
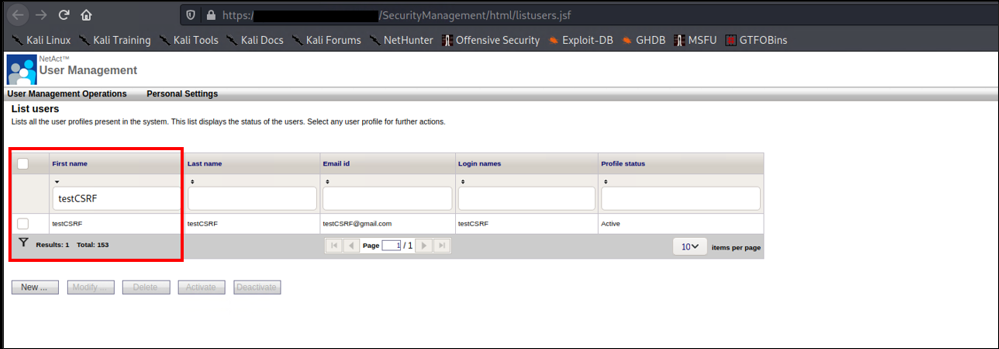
If a logged system administrator visits the endpoint with malicious javascript code crafted by an attacker, the new user testCSRF will appear in the application with admin privileges.
Security Impact
By exploiting this issue, a remote attacker is able to add arbitrary user on Nokia NetAct on behalf of a regular platform administrator.