Vulnerability Description: Multiple Improper Access Control- CWE-284
Software Version: 5.2.0-20211008
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-39811
CVSv3: 9,1
Severity: Critical
Credits: Luca Carbone, Fabio Romano, Stefano Scipioni, Massimiliano Brolli
Italtel NetMatch-S CI 5.2.0-20211008 has incorrect Access Control under NMSCI-WebGui/advancedsettings.jsp and NMSCIWebGui/SaveFileUploader. By not verifying permissions for access to resources, it allows an attacker to view pages that are not allowed, and modify the system configuration, bypassing all controls (without checking for user identity).
Step-by-step instructions and PoC
Any user logged in the web application can view pages or use functionalities that are normally accessible only by specific roles. In some cases, these functionalities can be accessed even without authentication. This vulnerability can be exploited in order to gather critical information or in order to have unauthorized access to some functionalities.
Affected Endpoints
· URL: https://[HOST]/[NODE-NAME]/NMSCI-WebGui/advanced-settings.jsp
· URL: https://[HOST]/[NODE-NAME]/NMSCI-WebGui/SaveFileUploader
Below are the evidences with the vulnerability details and the payloads used
URL: https://[HOST]/[NODE-NAME]/NMSCI-WebGui/advanced-settings.jsp
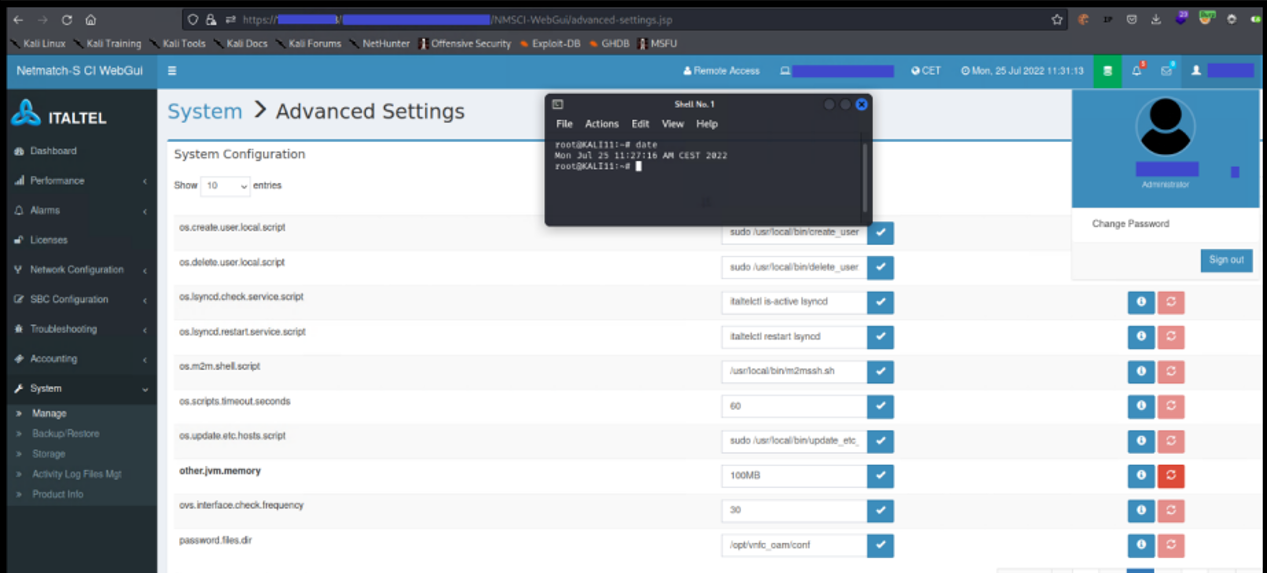
As an example, a user with the “Administrator” role can access the advanced settings page, which is normally available only to “System Administrator” users. This vulnerability can by exploited by simply inserting the appropriate endpoint in the URL.
URL: https://[HOST]/[NODE-NAME]/NMSCI-WebGui/SaveFileUploader
We can access the “Upload file” functionality in order to upload arbitrary files on the filesystem without authentication.
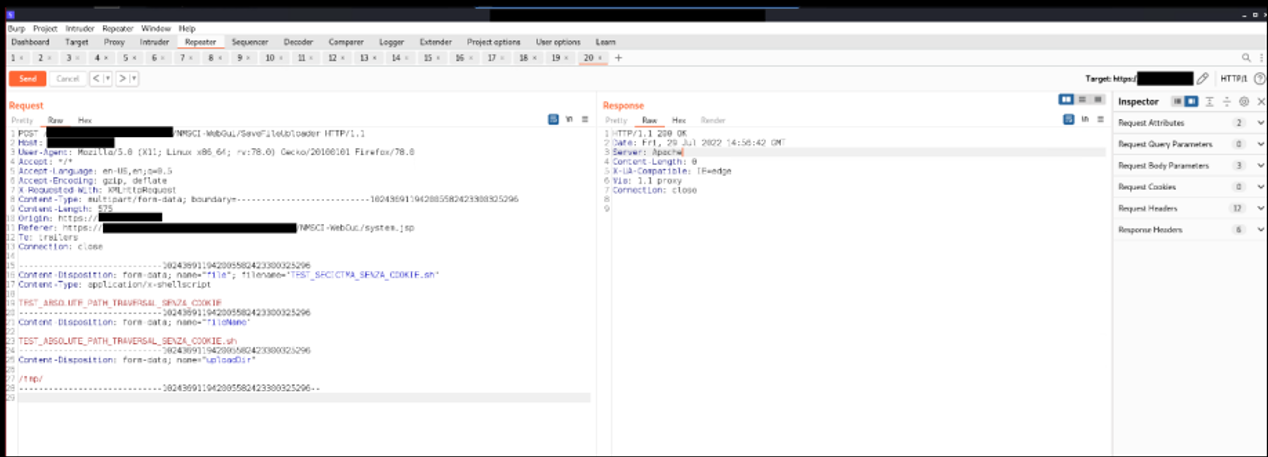
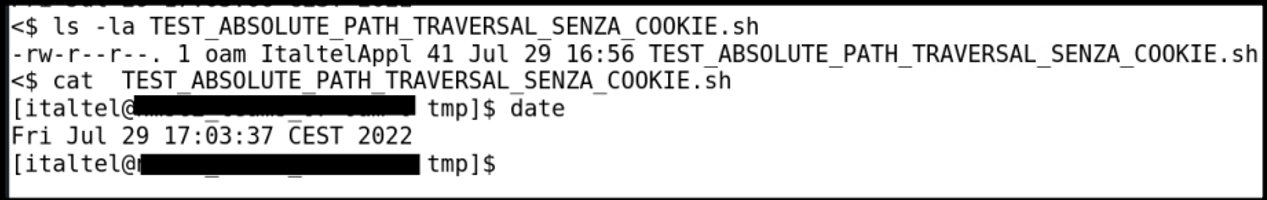
Security Impact
By exploiting this vulnerability on the web application it was possible to have unauthorized access to critical information and functionalities.