Vulnerability Description: Stored Cross-Site Scripting - CWE-79
Software Version: FortiOS 6.0.7 - 6.0.15, 6.2.2 - 6.2.12, 6.4.0 - 6.4.9 and 7.0.0 - 7.0.3
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-40680
CVSv3: 5.4
Severity: Medium
Credits: Massimiliano Ferraresi, Massimiliano Brolli
A improper neutralization of input during web page generation ('cross-site scripting') in Fortinet FortiOS 6.0.7 - 6.0.15, 6.2.2 - 6.2.12, 6.4.0 - 6.4.9 and 7.0.0 - 7.0.3 allows a privileged attacker to execute unauthorized code or commands via storing malicious payloads in replacement messages.
Step-by-step instructions and PoC
Vulnerability can be reproduce through the following actions.
An attacker with system permission can inject arbitrary javascript code in the Replacement Messages pages.
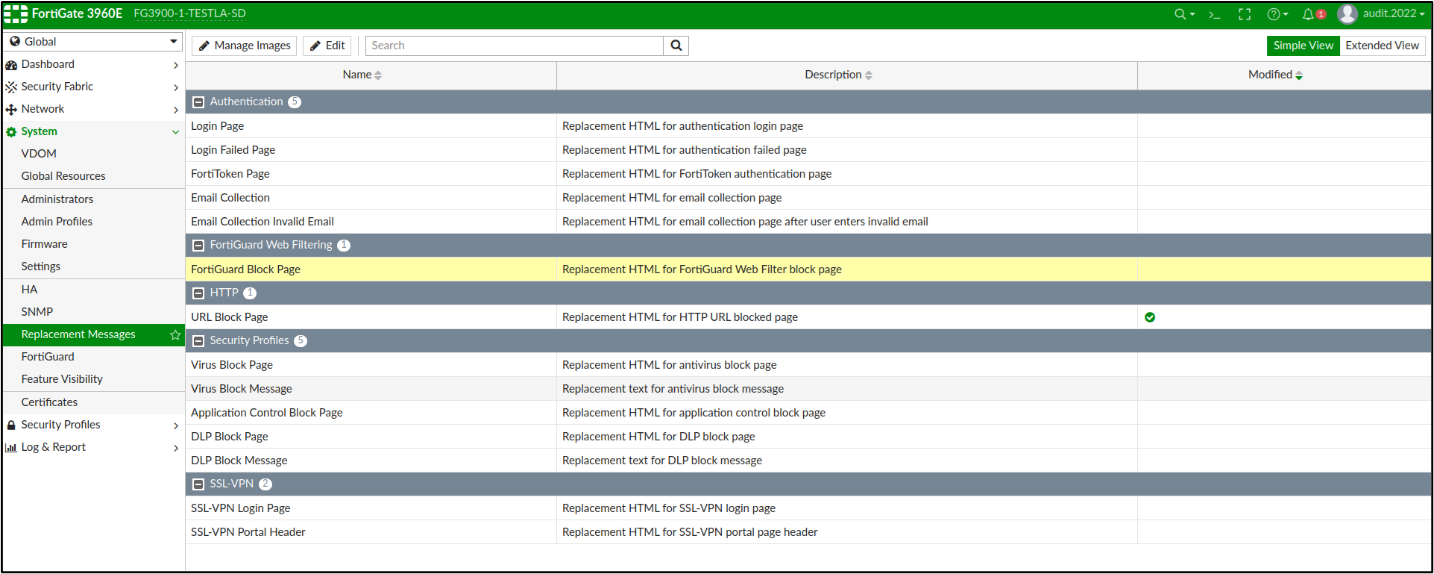
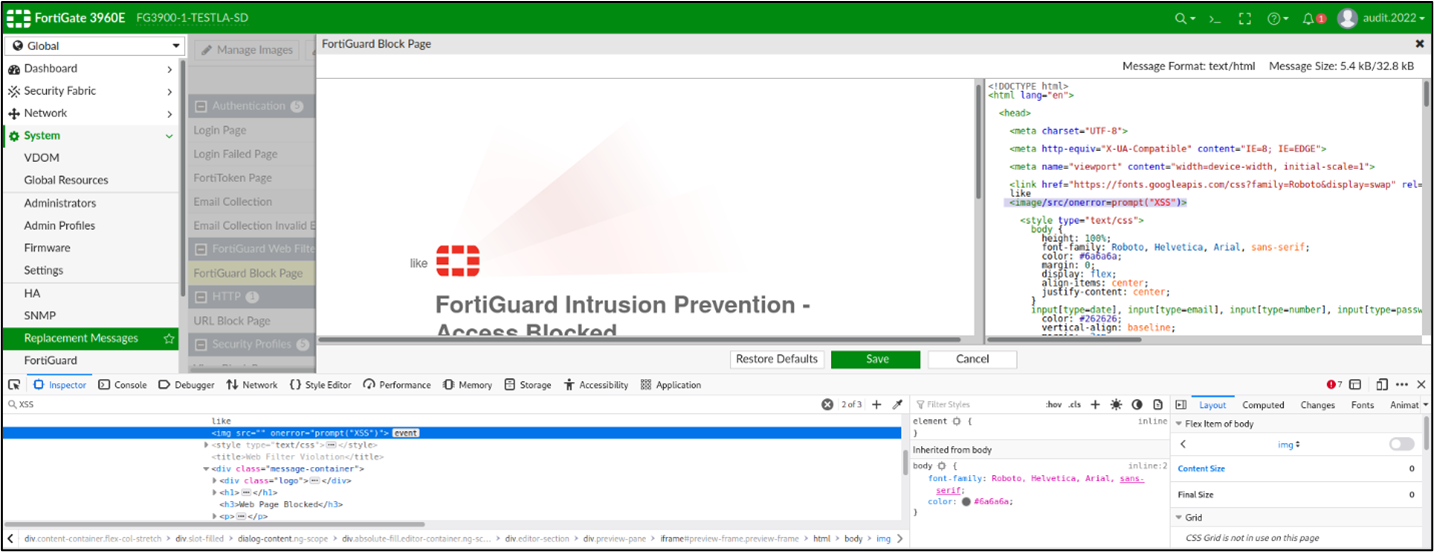
An attacker have to open and modify a page like “FortiGuard Block Page”:
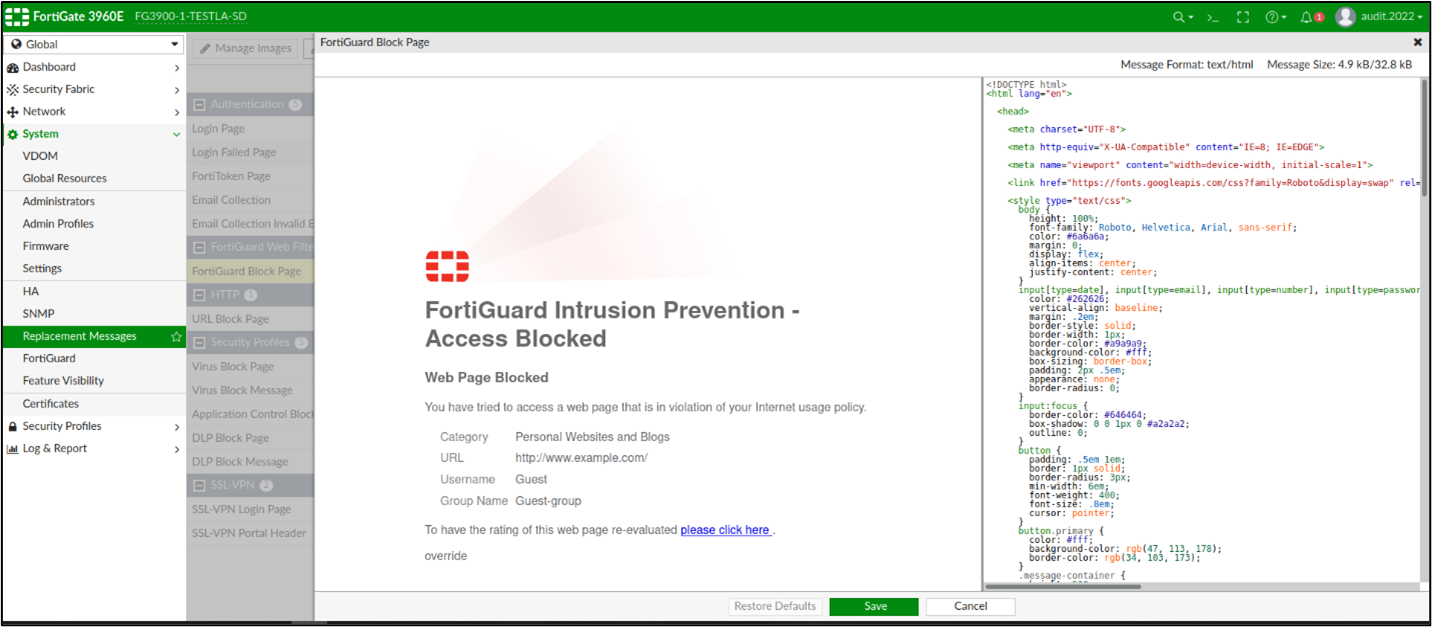
In the HTML source I tried to inject arbitrary javascript code, but with simple payload <script>alert(1);</script> the application did not execute anything:
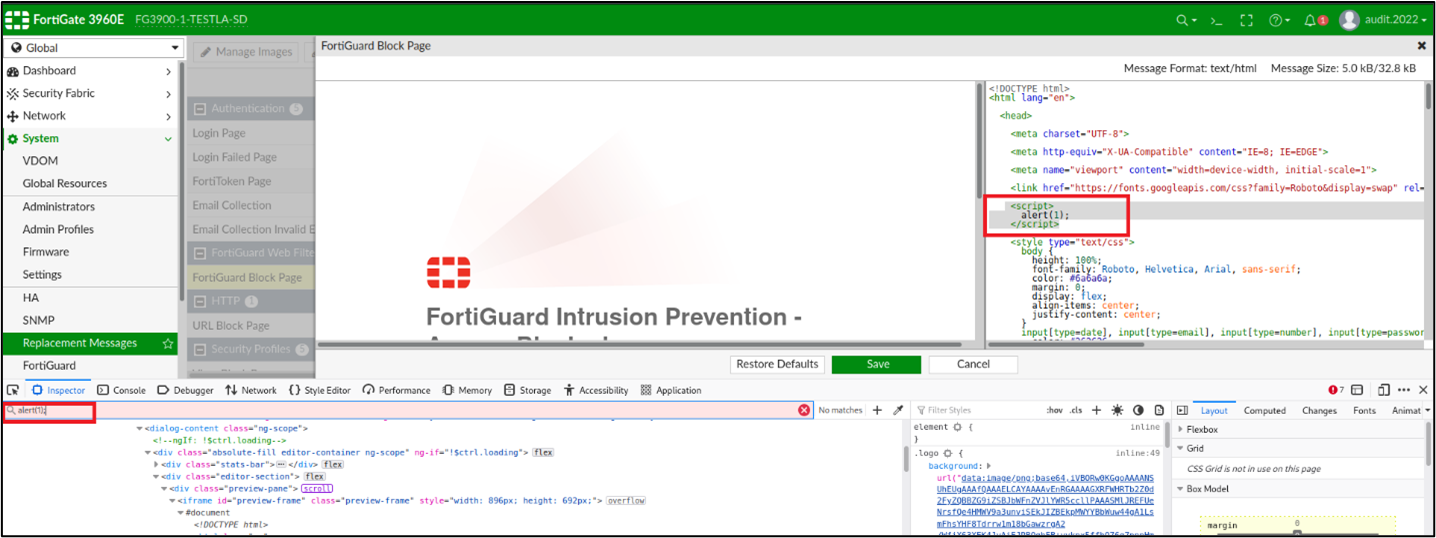
Probably the application satinizes the <script></script> content and does not execute the javascript code inside these tags, however with a custom payload like <image/src/onerror=prompt("XSS")> is possible to execute arbitrary javascript code:
· <image/src/onerror=prompt("XSS")>
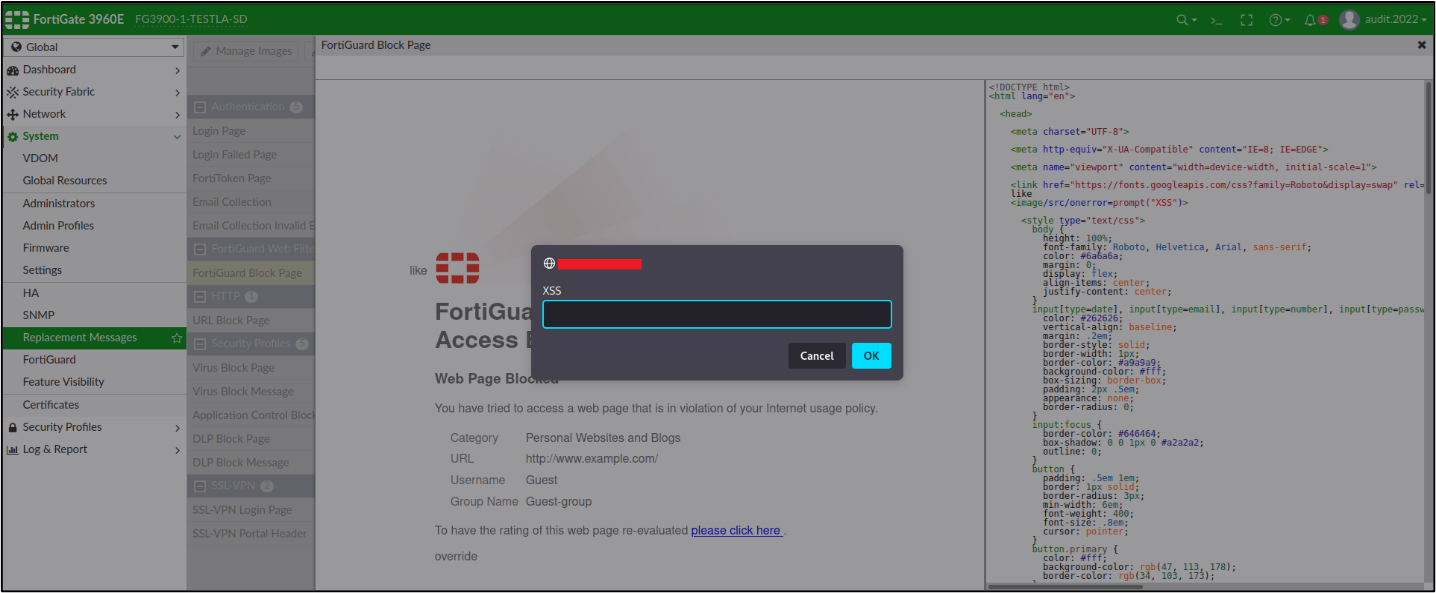
Click on “ok” and save the setting, the malicious code now is stored in the FortiGuardBlockPage, if the user visit this page the arbitrary javascript code will execute:
Security Impact
A potential attacker could modify the vulnerable web page with malicious javascript code permanently, thereby attacking anyone who visits the page.