Vulnerability Description: Observable Response Discrepancy – CWE-204
Software Version: ≤v031
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45177
CVSv3: 7.5
Severity: High
Credits: Luca Borzacchiello, Andrea Carlo Maria Dattola, Massimiliano Ferraresi, Massimiliano Brolli
The Web application provides different responses to incoming requests in a way that reveals internal state information to an unauthorized actor outside of the intended control sphere.
Step-by-step instructions and PoC
An attacker, without authentication, through Collaboration vDesk, is able to understand the state of the server and the users inside through the "User Enumeration" vulnerability.
Affected Endpoints
· https://vdeskbridge.[REDACTED]/api/v1/vdeskintegration/user/isenableuser
· https://vdeskbridge.[REDACTED]/api/v1/sharedsearch?search=[NAME]+[SURNAME]
· https://vdesk.[REDACTED]/login
Below is the evidence with details of the vulnerability and the payloads used.
Payload used to exploit the vulnerability:
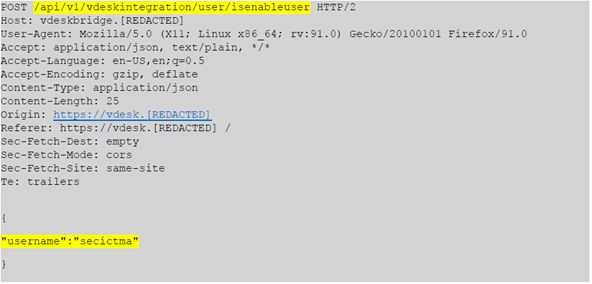
Figure 1 - Payload used to exploit the user enumeration vulnerability. By Iterating the username parameter, it is possible to verify, without any authentication, whether the user exists and can log in within the Collaboration vDesk system.
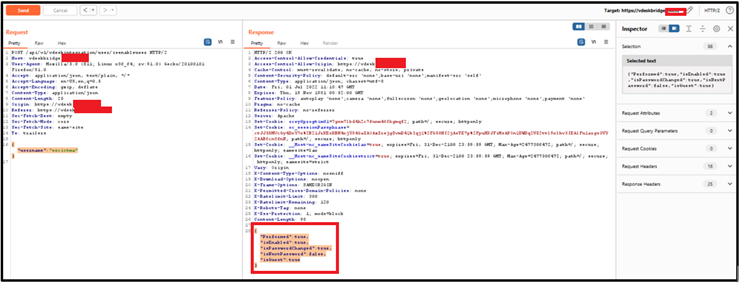
Figure 2 - Pair of HTTP requests and responses showing how the user "secictma" exists
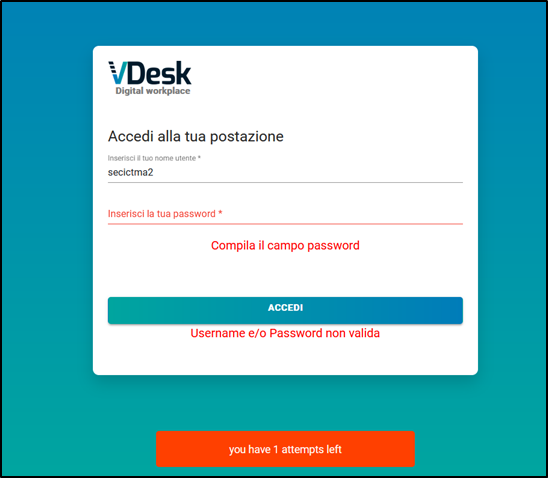
Figure 3 - Figure demonstrating the existence of the user "secictma2"
Security Impact
A user can gain access to confidential information such as the presence of all users on the system by facilitating the password bruteforce phase or by exploiting other vulnerabilities such as "Multiple Broken Access Control".