Vulnerability Description: CWE-79: Cross-Site Scripting Stored
Software Version: Firmware 2XD_S000.002.271
NIST: https://nvd.nist.gov/vuln/detail/CVE-2022-25344
CVSv3: 6.1
Severity: Medium
Credits: Mattia Campanelli, Luca Carbone, Massimiliano Brolli
An issue was discovered on Olivetti d-COLOR MF3555 2XD_S000.002.271 devices. The Web Application doesn't properly check parameters, sent in a /dvcset/sysset/set.cgi POST request via the arg01.Hostname field, before saving them on the server. In addition, the JavaScript malicious content is then reflected back to the end user and executed by the web browser.
NOTE: This vulnerability has been fixed in the available firmware version 2XD_S000.002.703 from January 17th, 2022 and later versions.
Step-by-step instructions and PoC
The vulnerable functionality can be reached through the following actions:
Affected Endpoints
Below are the evidences with the vulnerability details and the payloads used.
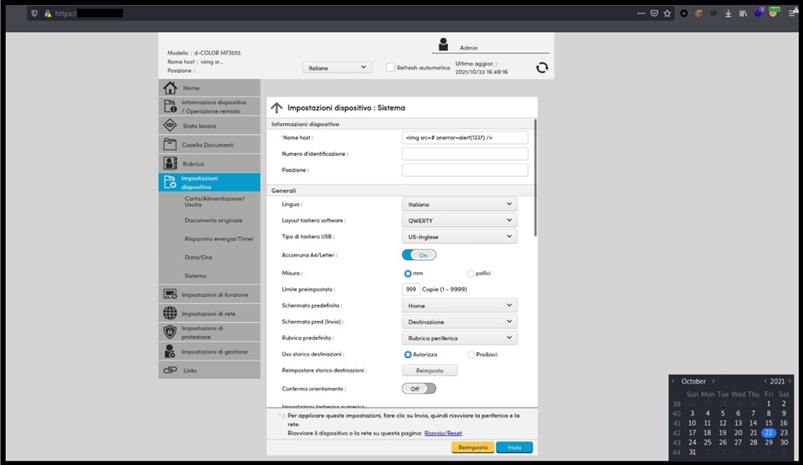
Figure 1: Administrative page to change the Host name
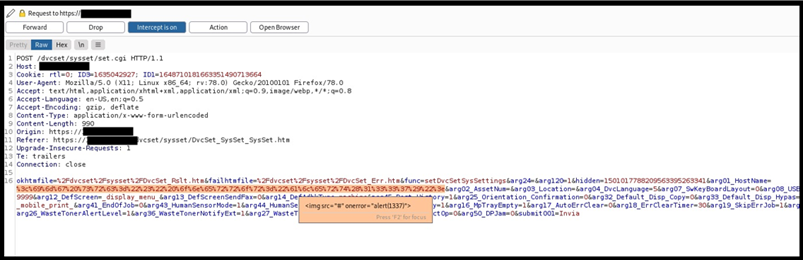
Figure 2: The malicious payload will be URL encoded, to bypass the client-side filters
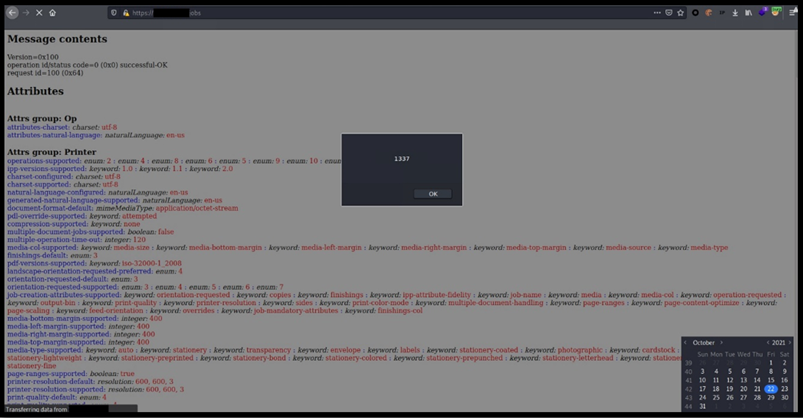
Figure 3: /jobs page stored javascript code