Vulnerability Description: Improper Neutralization of Formula Elements in a XLSX File (‘XLSX Injection’)- CWE-1236
Software Version: 16.22.40
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-22063
CVSS: 9.0
Severity: Critical
Credits: Stefano Carbè, Cristina Coppola, Andrea Carlo Maria Dattola, Stefano Scipioni, Massimiliano Brolli
The vulnerability occurs in ZENIC-ONE ZTE R58, version 16.22.40, when user-supplied information in an Excel (XLSX) file is not neutralized or is neutralized incorrectly so that special elements could be interpreted as a command when the file is opened by a spreadsheet product.
Step-by-step instructions and PoC
A remote user authenticated to the web application “Zenic-One” is able to clone a job from the GUI and, by intercepting the HTTP Request, can inject a payload in the “neId” parameter. Thus, when the Excel report for that job is downloaded by any user, clicking on the infected cell executes the payload on the victim's operating system.
Affected Endpoints
· URL: https://[IP]:[PORT]/uportal/framework/defaulthtml#/_mw-upgrade-task-management
· HTTP Parameter: neId
Below is the evidence with the vulnerability details and the payloads used.
This first step consists of the interception of the POST HTTP request generated by the “New” button on the GUI’s Upgrade Job Section after clicking the 'clone' button of a job.
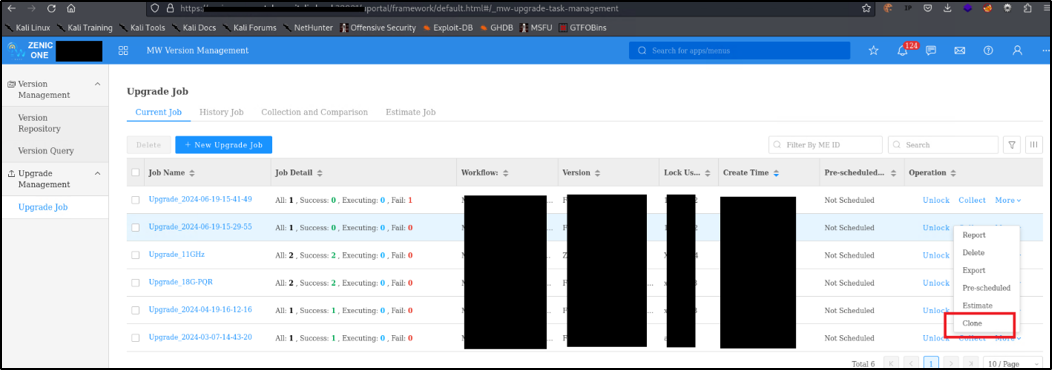
Figure 1: Clone button on the GUI
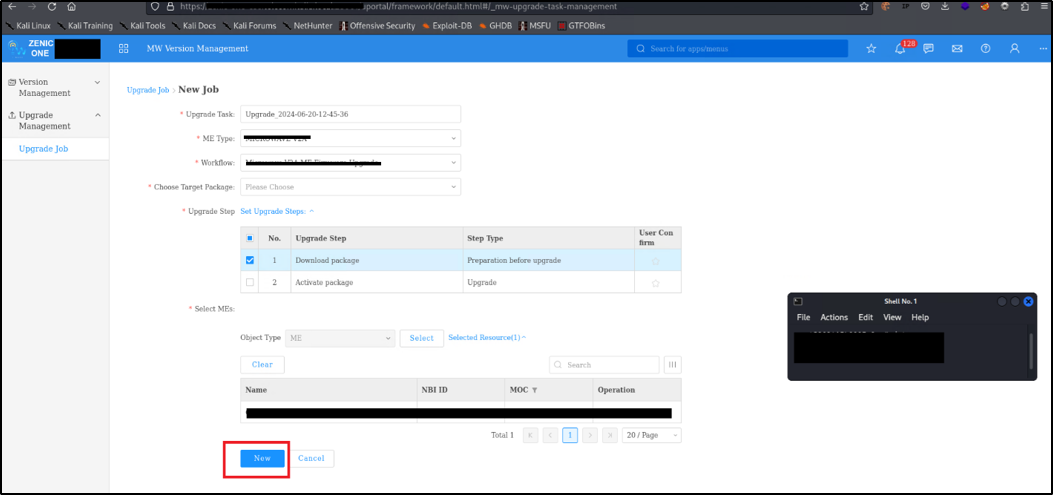
Figure 2: New button on the GUI
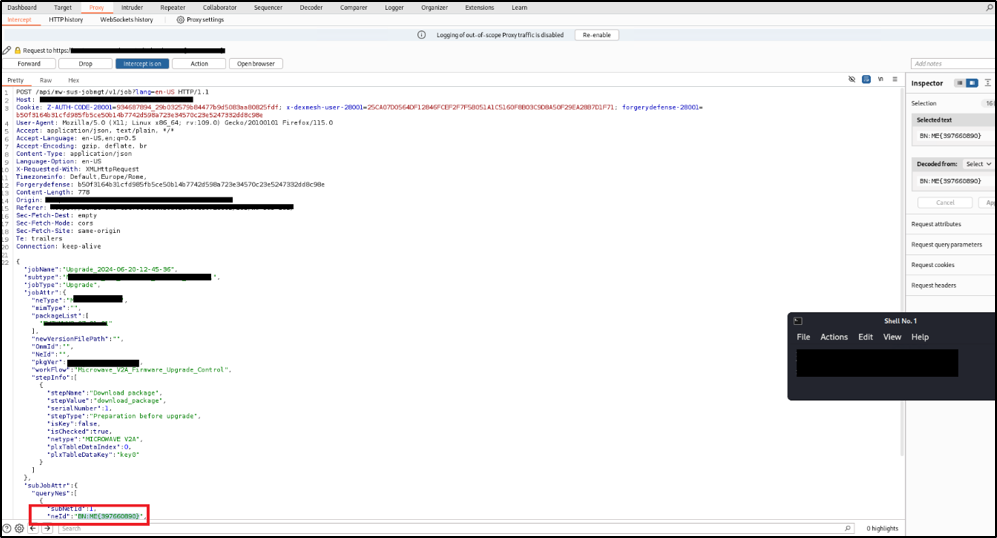
Figure 3: Interception of the HTTP Request with the neId parameter value inherited from the original job
The second step is changing the value of the neId parameter with a malicious payload.
In this case the following payload has been used: =calc|a!z
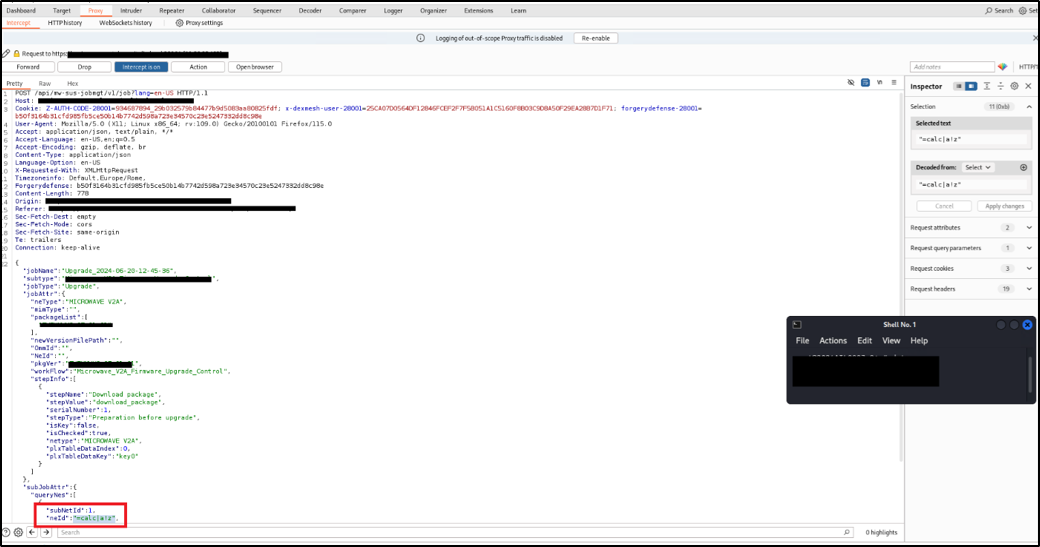
Figure 4: HTTP Request modified with the injected payload
The third step is for a user to download the report for that job and open the Excel file locally on his PC.
When a user with the Excel Macro enabled clicks on the infected cell, the injected code is executed.
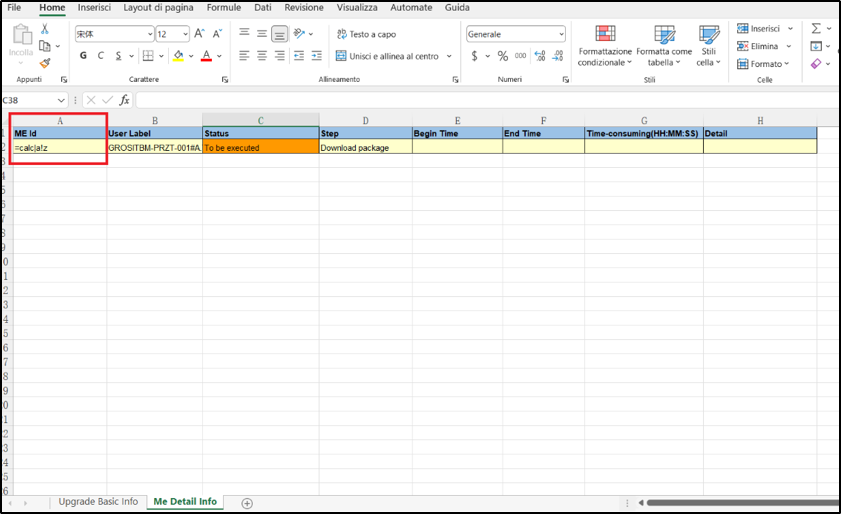
Figure 5: Infected Excel downloaded file
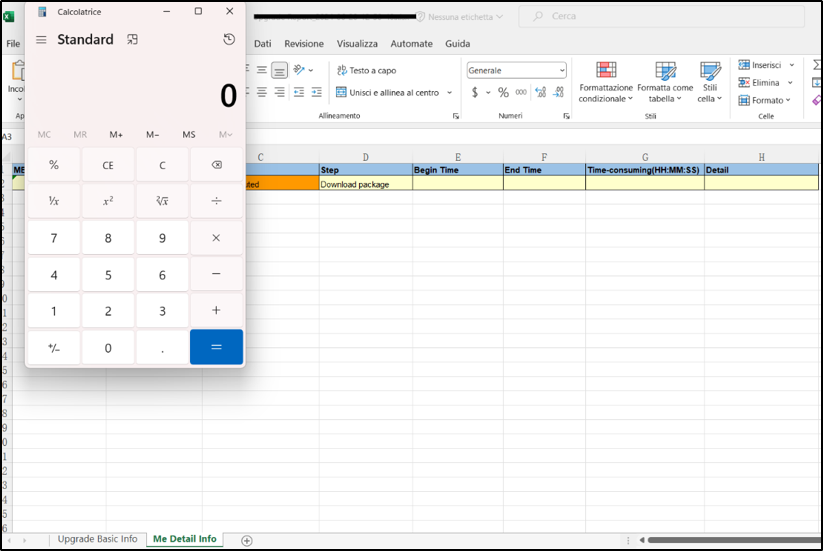
Figure 6: Execution of the injected payload
Security Impact
By exploiting this issue an attacker is able to inject arbitrary formulas into XLSX files.
This can potentially lead to remote code execution at client side (DDE) or to data leakage via maliciously injected hyperlinks.