Vulnerability Description: Insufficiently Protected Credentials - CWE-522
Software Version: 1.6.4
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-31840
CVSSv3: 6.5
Severity: Medium
Credits: Luca Carbone, Fabio Romano, Federico Draghelli, Massimiliano Brolli
The web application inserts plain passwords in the HTML source code.
Step-by-step instructions and PoC
An authenticated user is able to edit the configuration of the email server. Once the user access to the edit function, the web application fills the edit form with the current credentials for the email account, including the plain password.
Below are the evidences with the vulnerability details and the payloads used.
URL: https://[HOST]/[NODE-NAME]/supervoip/api/v1/getEmailServer/[ACCESS-TOKEN]/[REDACTED]/it
The page displays the plaintext password of the email address.
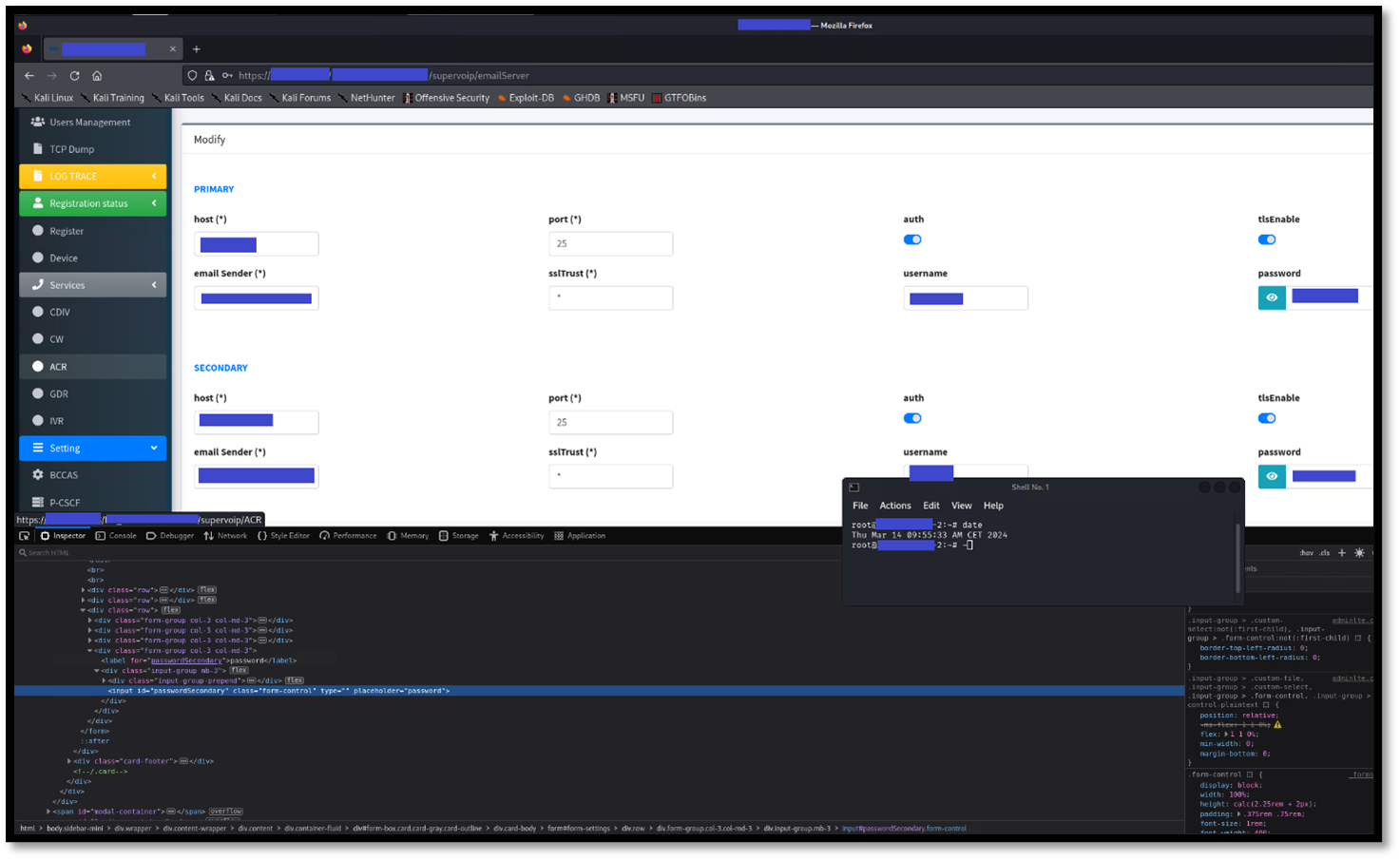
Figure 1 - Mail server configuration
When you get to this page, the following request is sent to the server. The response contains the plaintext password of the email address.
Figure 2 - Payload
Click To Enlarge
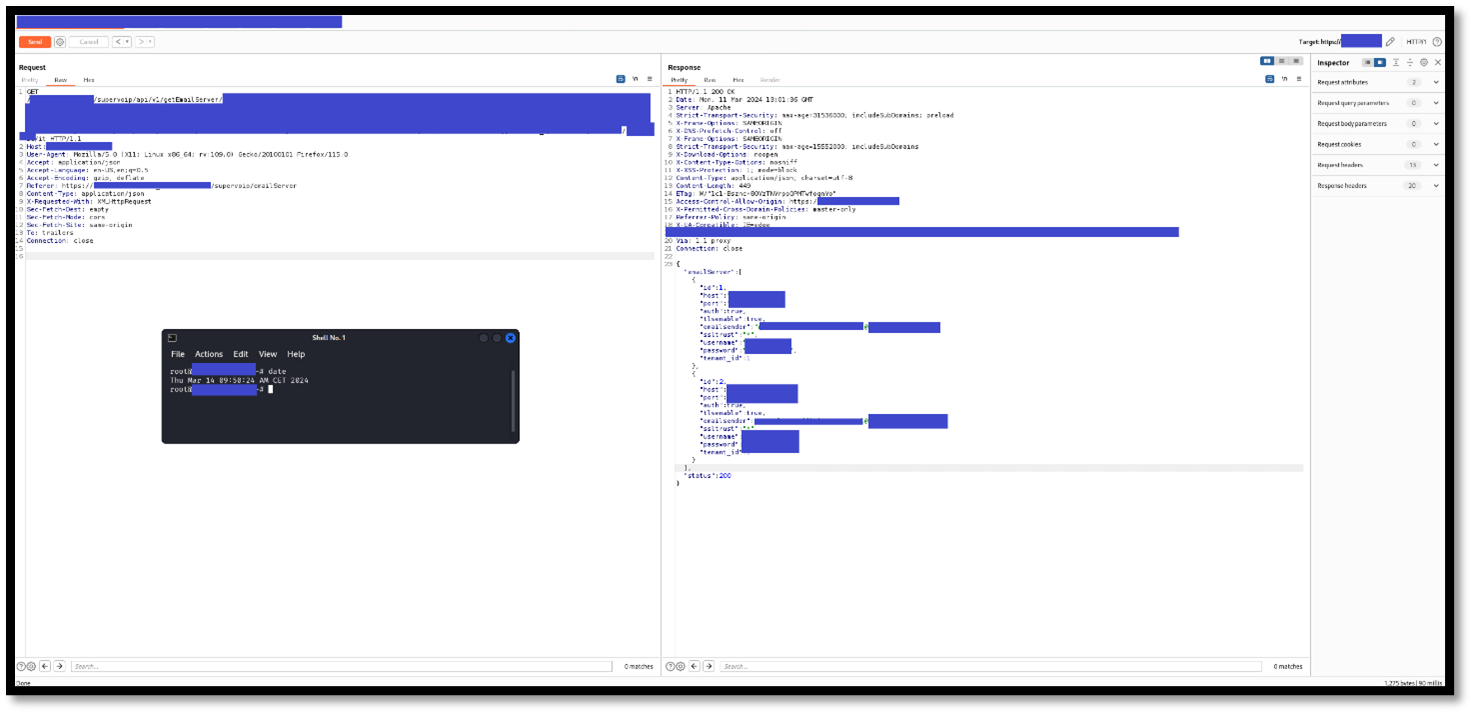
Figure 3 - The server responds with the plaintext password.
Security Impact
By exploiting this vulnerability, it is possible for an attacker to read the password of the mail server.