Vulnerability Description: Generation of Error Message Containing Sensitive Information - CWE-209
Software Version: 1.6.4
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-31844
CVSSv3: 5.3
Severity: Medium
Credits: Luca Carbone, Fabio Romano, Federico Draghelli, Massimiliano Brolli
The server does not properly handle application errors. In some cases, this leads to a disclosure of information about the server.
Step-by-step instructions and PoC
An unauthenticated user is able craft specific requests in order to make the application generate an error. Inside this error, some information about the server is revealed, like the absolute path of the source code of the application. This kind of information can help an attacker to perform other attacks against the system. This vulnerability can be exploited without authentication.
Below are the evidences with the vulnerability details and the payloads used.
URL: https://[HOST]/[NODE-NAME]/supervoip/api/v1/auth/login
Figure 1 - Payload
In the following screenshot, a malformed JSON is submitted. The server responses with an error message containing absolute paths referring to the web application source code.
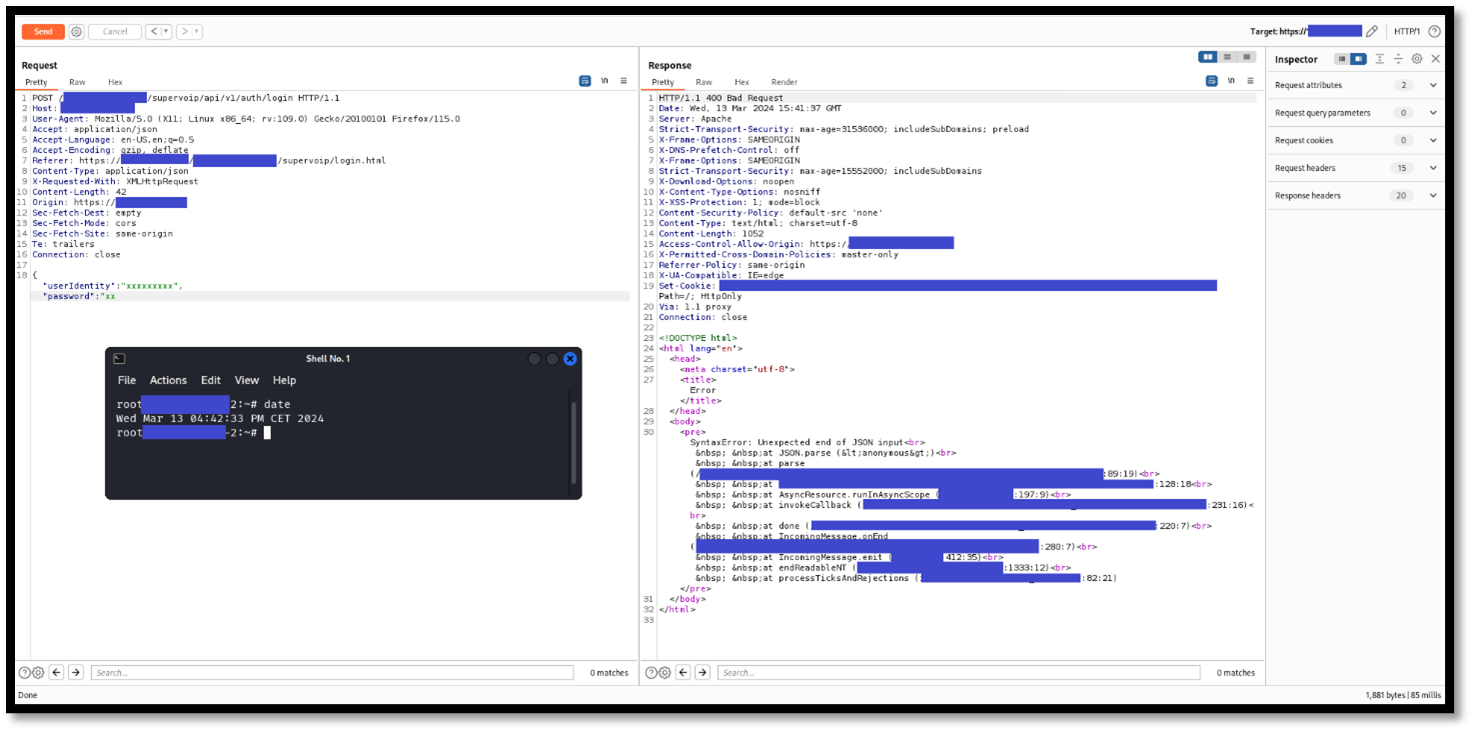
Figure 2 - Information Disclosure
Security Impact
An attacker can gather information about the system to perform additional attacks.