Vulnerability Description: Cross Site Scripting Stored - CWE-79
Software Version: 12.20, 12.21, 12.22, 12.23, 12.24, 12.25, 12.26
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-5532
CVSS:
Severity:
Credits: Marco Ventura, Claudia Bartolini, Massimiliano Brolli
In OpenText™ Operations Agent, version 12.20, 12.21, 12.22, 12.23, 12.24, 12.25 and 12.26, is possible to perform Cross-site scripting Stored attacks. This vulnerability allows an attacker to compromise the interactions that users have with the vulnerable application. Cross-site scripting vulnerabilities normally allow an attacker to masquerade as a victim user, to carry out any actions that the user is able to perform, and to access any of the user's data. If the victim user has privileged access within the application, then the attacker might be able to gain full control over all of the application's functionality and data.
Step-by-step instructions and PoC
A remote user that has the permissions to modify the agent configuration file, can perform Cross-site scripting Stored attacks. In particular, by adding a malicious payload within the CORE_ID value, the attacker can inject an arbitrary javascript code in the HTML page.
Affected Endpoints
• URL:
– http://[IP]:[PORT]/Hewlett-Packard/OpenView/BBC/ovrg?html
– http://[IP]:[PORT]/Hewlett-Packard/OpenView/BBC/services?html
– http://[IP]:[PORT]/Hewlett-Packard/OpenView/BBC/ping?html
– http://[IP]:[PORT]/Hewlett-Packard/OpenView/BBC/status?html
• Vulnerable configuration parameter: CORE_ID
Below the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
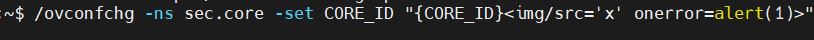
Figure 1: set vulnerable parameter
This first step consist of change the CORE_ID agent configuration parameter, by adding the “img” HTML tag, as reported previously.
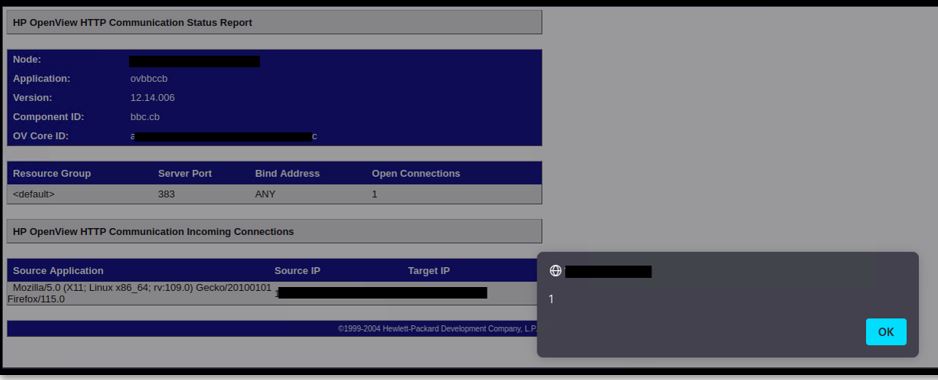
Figure 2- Cross-site Scripting Stored execution
Security Impact
An attacker is able to compromise the interactions that users have with the vulnerable application.