Vulnerability Description: Improper Handling of Parameters - CWE-233
Software Version: 7.0.15
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-9329
CVSS: 6.1
Severity: Medium
Credits: Marco Ventura, Claudia Bartolini, Andrea Carlo Maria Dattola, Debora Esposito, Massimiliano Brolli
The Host HTTP parameter could cause the web application to redirect to the specified URL, when the requested endpoint is '/management/domain'. By modifying the URL value to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials.
Step-by-step instructions and PoC
The application presents an Open Redirect on the Host parameter, when the /management/domain endpoint is requested via an HTTP GET request.
Affected Endpoints
URL: https://[IP]:[PORT]/management/domain
HTTP Parameter: Host
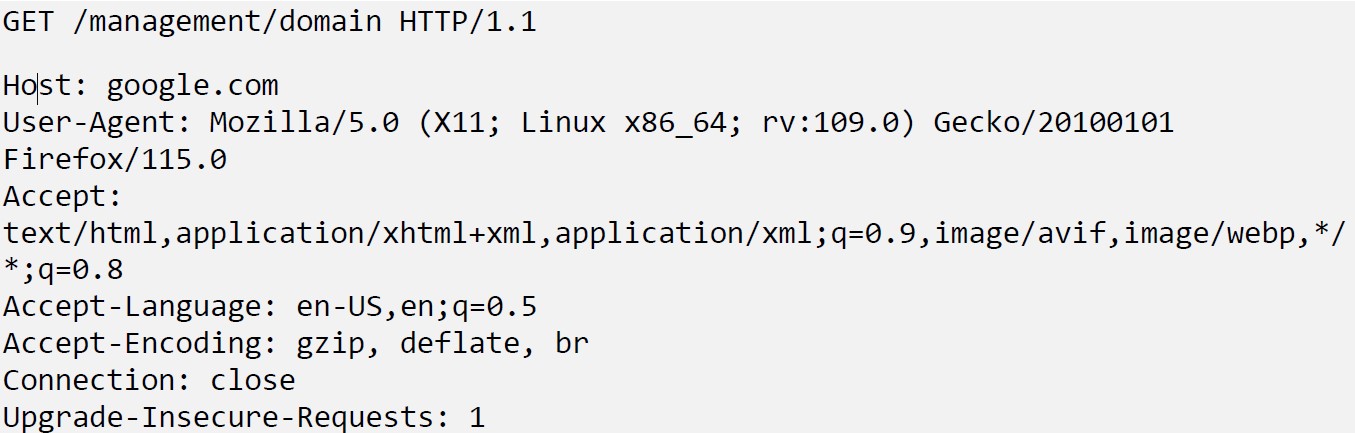
Figure 1: Host parameter modified
Below is the evidence with the vulnerability details and the payload used.
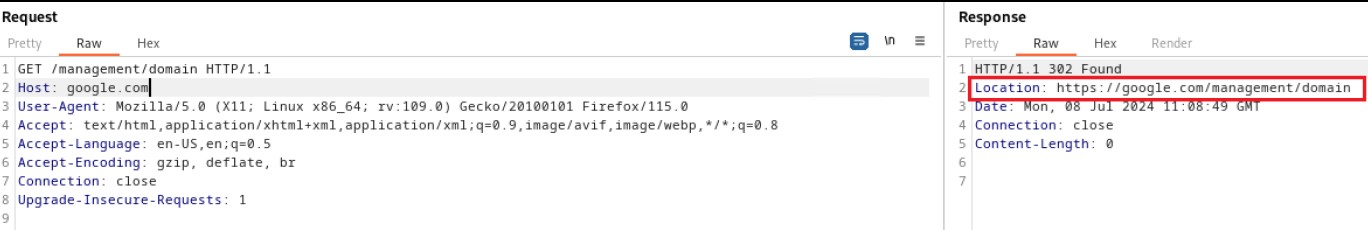
Figure 2: payload and evidence
To perform this attack, the attacker does not need to be authenticated to the target application.
Security Impact
An attacker can construct a URL within the application that causes a redirection to an arbitrary external domain. This behaviour can be leveraged to facilitate phishing attacks against users of the application. The ability to use an authentic application URL, targeting the correct domain and with a valid SSL certificate (if SSL is used), lends credibility to the phishing attack because many users, even if they verify these features, will not notice the subsequent redirection to a different domain.