Vulnerability Description: Login Brute Force - CWE-307
Software Version: 7.0.15
NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-9342
CVSS: 9.8
Severity: Critical
Credits: Claudia Bartolini, Marco Ventura, Andrea Carlo Maria Dattola, Debora Esposito, Massimiliano Brolli
In Eclipse GlassFish version 7.0.15 is possible to perform Login Brute Force attacks. This vulnerability arises when the product does not implement sufficient measures to prevent multiple failed authentication attempts within a short time frame, making it more susceptible to brute force attacks
Step-by-step instructions and PoC
A remote unauthenticated user can perform Login Brute Force attacks. Successfully exploitation of this vulnerability can allow the administration access to an attacker.
Affected Endpoints
• URL:
– https://[IP]:[PORT]/j_security_check
– https:// [IP]:[PORT]/management/domain
• HTTP GET Parameter:
– j_password
– Header Authorization
Below there is the evidence with the vulnerability details and the payloads used.
As shown in the figure below, an attacker can perform 50 failed login attempts and can login successfully at the 51st to the web application. This behavior occurs because the product does not implement sufficient measures to prevent multiple failed authentication attempts within a short time frame.
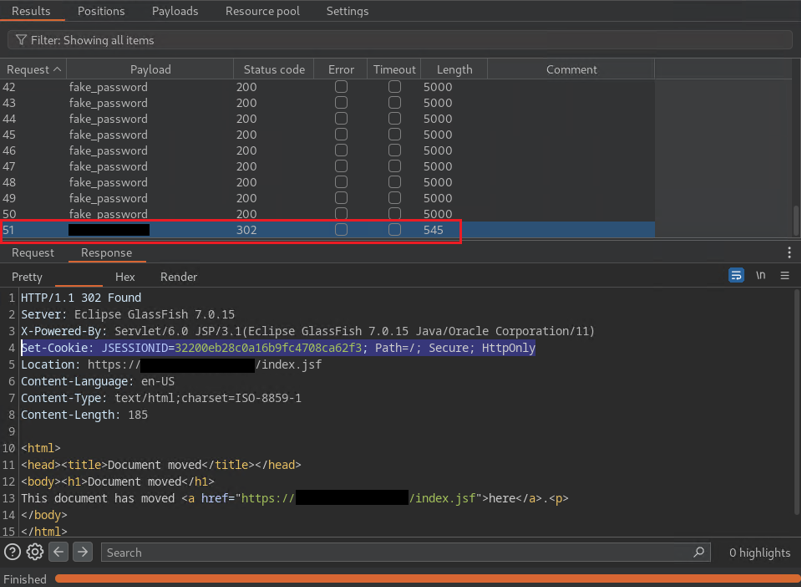
Figure 1: PoC - Brute Force Login
In the similar way it is possible to perform the same attack’s type, described previously, in the management REST interface, as shown below:
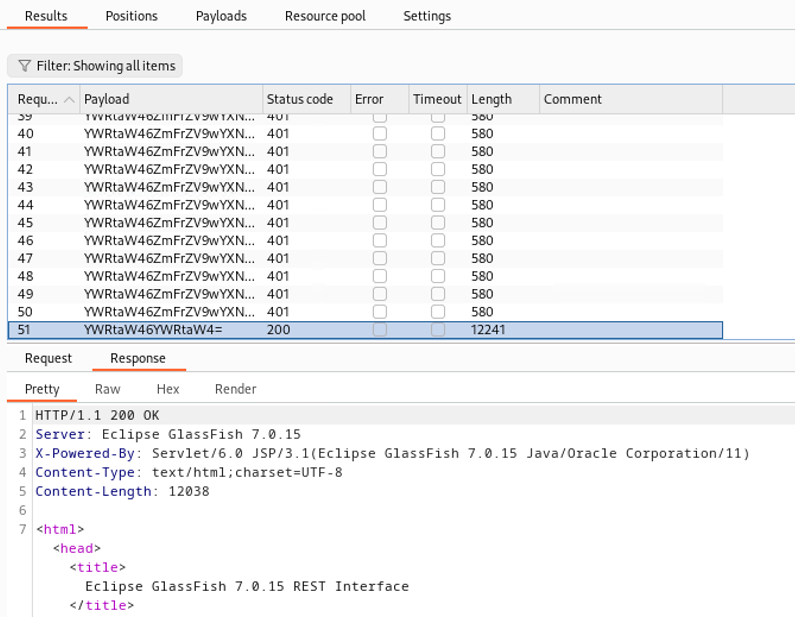
Figure 2: PoC - Brute Force Login REST interface
Security Impact
An attacker can exploit this vulnerability to obtain the administration access within the Administration Console or Management REST Interface.
Remediation Steps
It is suggested to temporarily disable the account after a certain number of failed attempts. This will prevent attackers from continuing to try to brute-force their way in once they have reached a certain threshold. The account can be automatically re-enabled after a period of time, or the user can be required to contact customer support to have it reset.