Vulnerability Description: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') – CWE-79
Software Version: 34.0.0.Beta
NIST: https://nvd.nist.gov/vuln/detail/CVE-2025-23366
CVSS: 4.8
Severity: Medium
Credits: Claudia Bartolini, Marco Ventura, Massimiliano Brolli
The product WildFly 34.0.0.Beta does not neutralize or incorrectly neutralizes user-controllable input before it is placed in output that is used as a web page that is served to other users.
Two types of XSS attack have been found. In the first, the attacker must be authenticated as a user that belongs to management groups “SuperUser”, “Admin”, or “Maintainer”. In the other, the actor must be authenticated as user that belongs to whichever management group.
A remote user, authenticated to the HAL Console, can store malicious JavaScript code within the “Name” attribute, in the Standalone Server Configuration page. Successfully exploitation of this vulnerability can cause the extraction of some information and/or the execution of arbitrary HTTP Request in the context of victim's session.
Affected Endpoints
· URL: http://[IP]:[PORT]/console/index.html#standalone-server
· Vulnerable Configuration Parameter: Name
Below the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
><img src=x onerror=alert('XSS')>
As a first step, the attacker must be logged in the HAL Console and has to enter the Runtime session and click on “View” button relating the server, as shown below:
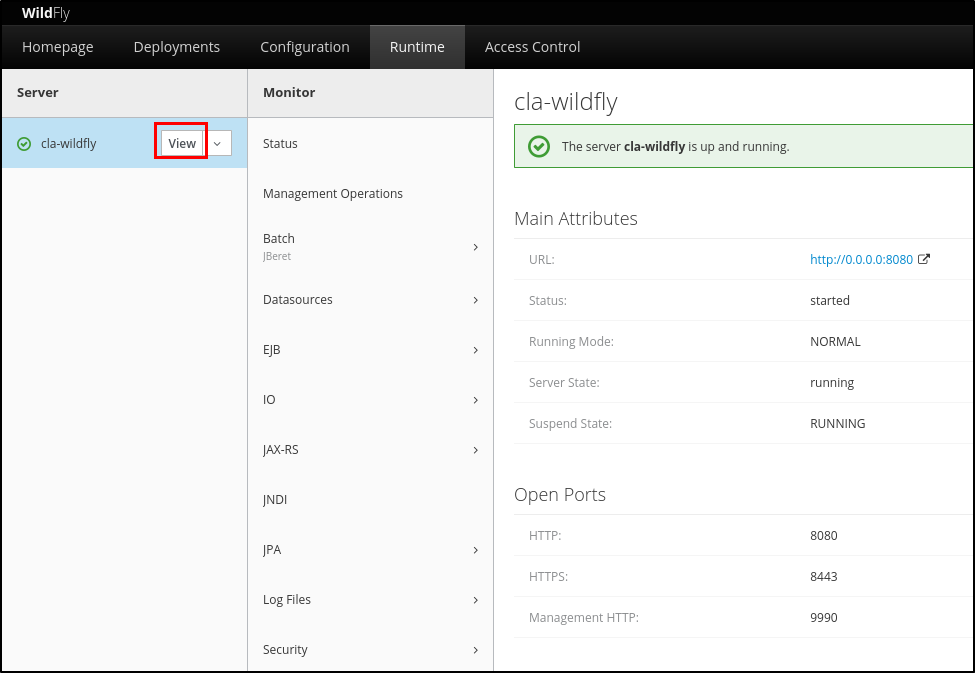
Figure 1: click on “View” button
And in the next page, the attacker just needs to click the “Edit” link label and replace the “Name” attribute and save it:
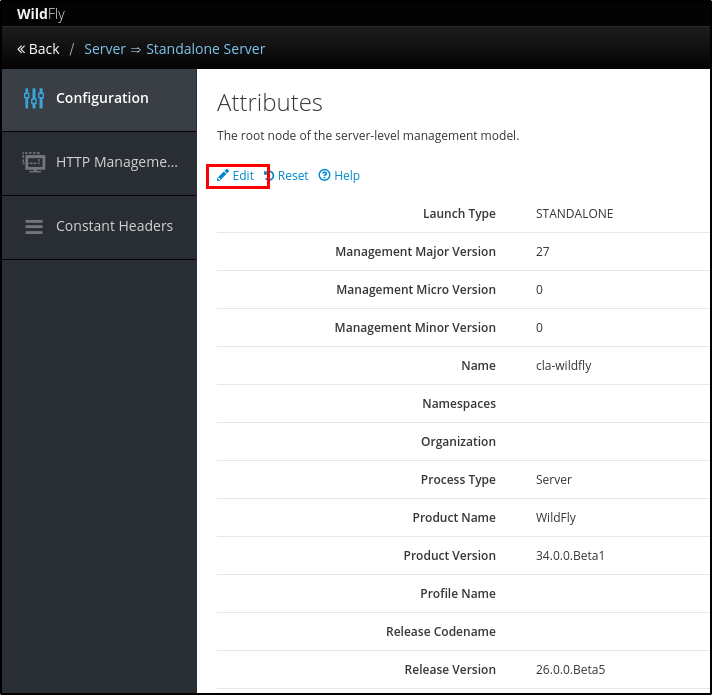
Figure 2: Edit link label
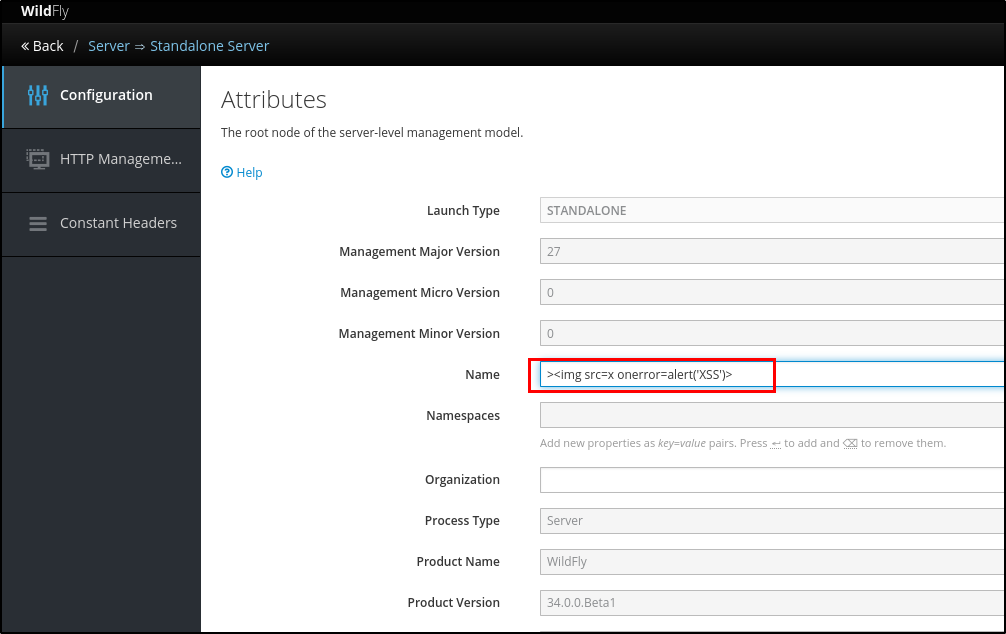
Figure 3: replace the Name attribute with the malicious script
After the server has been reloaded, the server name changed and, when the attacker select “Configuration Changes” as shown below, the script runs
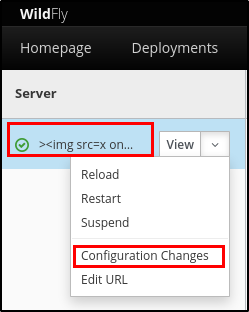
Figure 4: Select Configuration Changes for the server involved
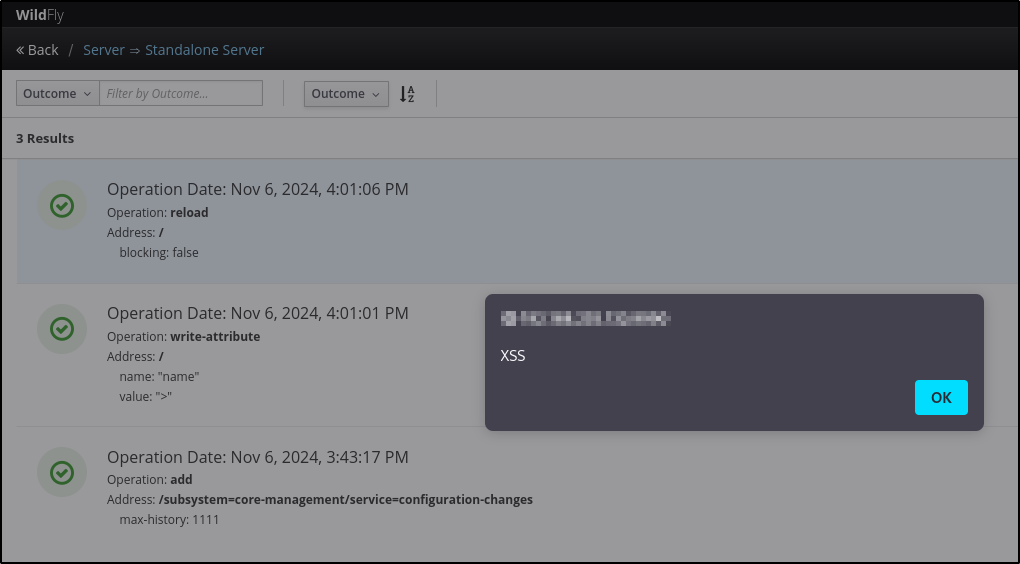
Figure 5: Stored Cross-site Scripting
Security Impact
If an attacker can control a script that is executed in the victim's browser, then they can typically fully compromise that user. The attacker places their exploit into the application itself and simply waits for users to encounter it.
Amongst other things, the attacker can:
• Perform any action within the application that the user can perform.
• View any information that the user is able to view.
• Modify any information that the user is able to modify.
• Initiate interactions with other application users, including malicious attacks, that will appear to originate from the initial victim user.
A remote user, authenticated to the Management Console, can store malicious JavaScript code within the “URL” attribute, in the Standalone Server Runtime page. Successfully exploitation of this vulnerability can cause the extraction of some information and/or the execution of arbitrary HTTP Request in the context of victim's session.
Affected Endpoints
· URL: http://[IP]:[PORT]/console/index.html#runtime;path=standalone-server-column~standalone-host-[HOST_NAME]
· Vulnerable Configuration Parameter: URL
Below the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
javascript:alert('XSS Runtime URL')
As a first step, the attacker, in this case an ordinary “auditor” user, must be logged in the HAL Console and has to enter the Runtime session and click on the dropdown menu’s trigger relating the server and select “Edit URL”, as shown below:
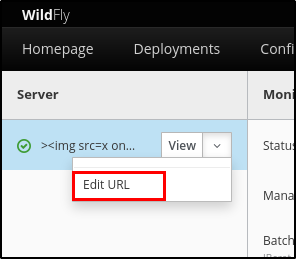
Figure 6: Edit URL
And modify the URL field with the javascript malicious code:
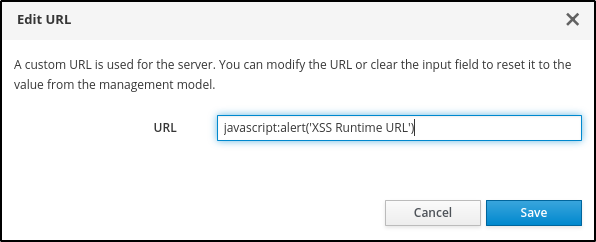
Figure 7: Add javascript in the URL field
Finally, the javascript is available, up and running
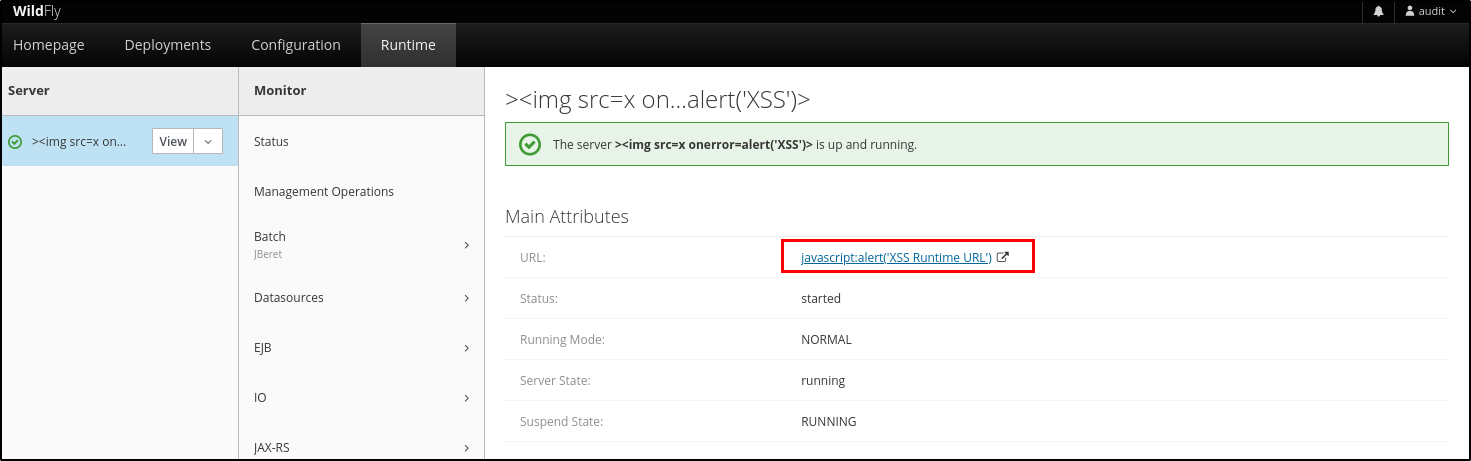
Figure 8: URL Link availability

Figure 9: XSS execution by runtime menu
Critically important, the previous javascript is also used by the web applications deployed in the web server, through the context root, especially for the admin users that are affected by javascript set by a non-admin user.
Below is represented the admin deployments frame in which is present the context root “webshell” that carry out the cross site scripting described previously:
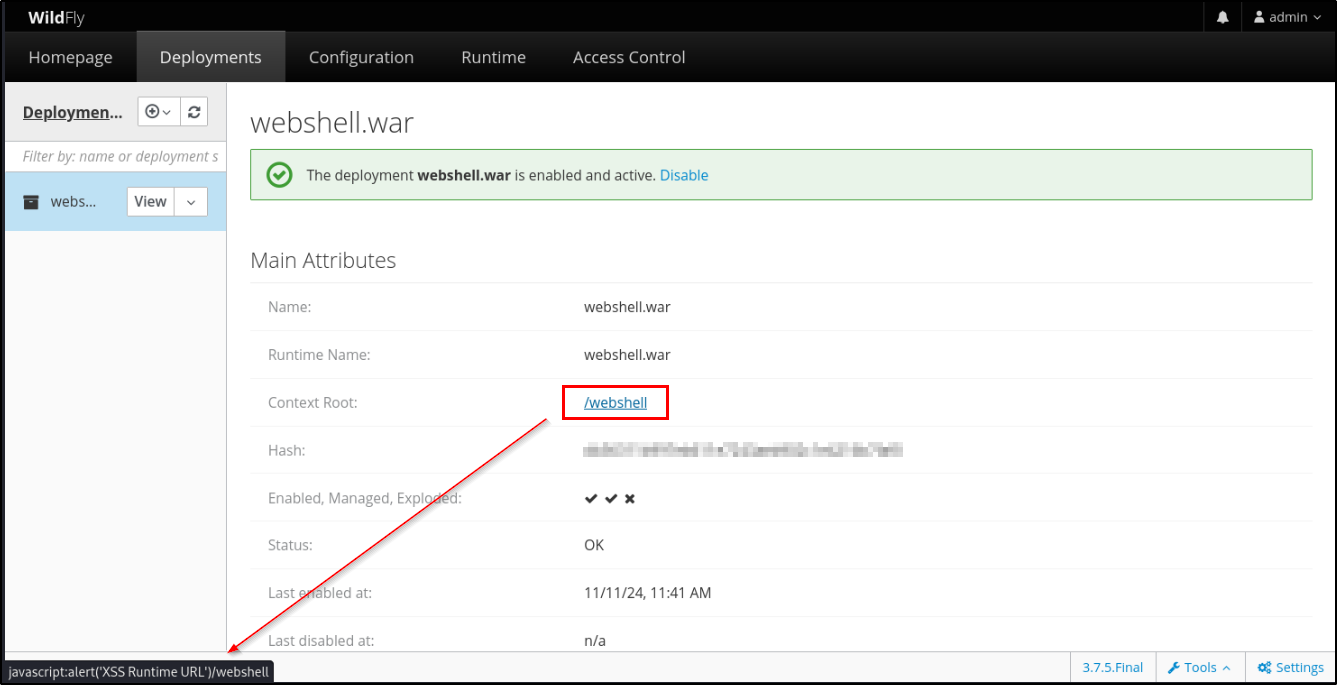
Figure 10: link to malicious javascript